Is there any (Mac) OS X-specific malware around? Oh yes. But for some odd reason I haven't said anything interesting on this topic for quite a while… The last time was two and a half years ago. Yes...
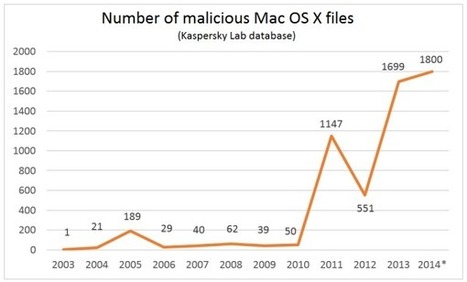
So what can we deduce from these data?
First: cybercriminals find it easiest making money with mostly legal (well, almost legal) approaches. Persistent advertising also makes money, and coupled with large-scale infections – big money.
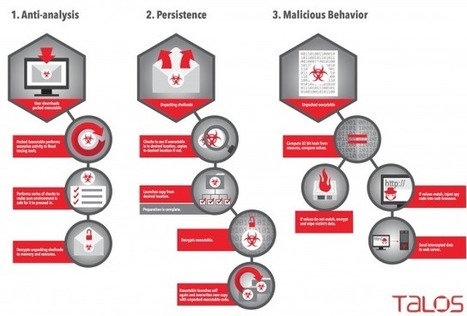
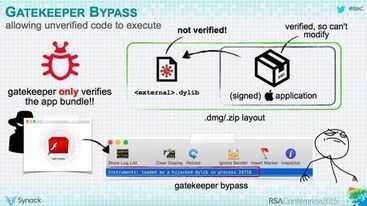
Second: OS X virus writers are a fairly rare but sophisticated species. Unlike the Windows virus scene, the OS X virus scene bypassed the childish stage of ‘viruses for fun’ and went straight to the grown-up – Mac OS – stuff with all the attendant hardcore malware tricks that are necessary for it. These are serious folks, folks! It’s very likely they honed their skills on the Windows platform first, and then went over to Mac to conquer new, uncharted territory in search of new untapped money-making possibilities. After all, the money’s there, and the users are relatively blasé about security, which means there are plenty of opportunities – for those blackhatters who are willing to put in the work.
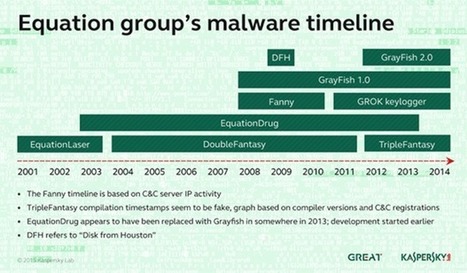
Third: professional espionage groups have really taken to exploiting OS X. Many APT attacks in the last few years acquired Mac-modules, for example Careto, Icefog, and the targeted attacks against Uyghur activists. Yes, here we’re talking pinpointed –exclusive as opposed to mass – attacks, aimed at specially chosen victims; this is why they don’t figure in the top-20. Not that they are any less dangerous; especially if your data may be interesting to intelligence agencies.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security



 Your new post is loading...
Your new post is loading...
















![H1 2014 Threat Report - F-Secure [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/3WKggSg7n-Fjl4tKZAeUKDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)








Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux