Gezielte, gut getarnte Phishing-Attacken sind große Gefahr für Unternehmen.
Der Security-Software-Hersteller ESET rät Unternehmen zu einer verstärkten Sensibilisierung für Phishing-Attacken und damit einhergehend zu einer besseren IT-Weiterbildung. Nur so können die eigenen Mitarbeiter vor gezielten und gut getarnten Angriffen geschützt werden. Denn Attacken dieser Art sind mittlerweile geschickt auf ihre Zielgruppen zugeschnitten und nur mit großer Sorgfalt und Verständnis erkennbar.
Anlass für den Ratschlag ist das Ergebnis eines Tests, den das Center of Excellence for Research, Innovation, Education and Industrial Labs Partnership (CEFRIEL) im Auftrag von 15 internationalen Unternehmen kürzlich durchführte. Die Einrichtung prüfte die Anfälligkeit von Mitarbeitern für speziell auf Unternehmen gemünzte Betrugsversuche, so genannte „Spear-Phishing“-Attacken. Das Ergebnis: Jeder Fünfte ging den Testern ins Netz.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Phishing



 Your new post is loading...
Your new post is loading...





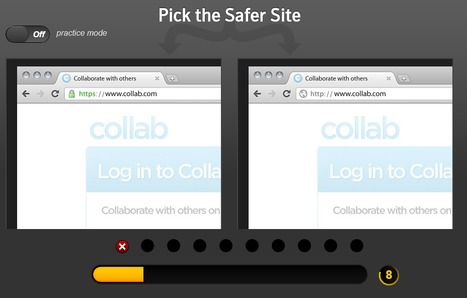

![Phishing Deceives the Masses [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/bpENVbKlv4q8nU8YQXp8jDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)





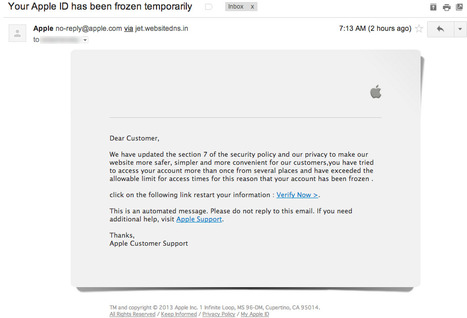





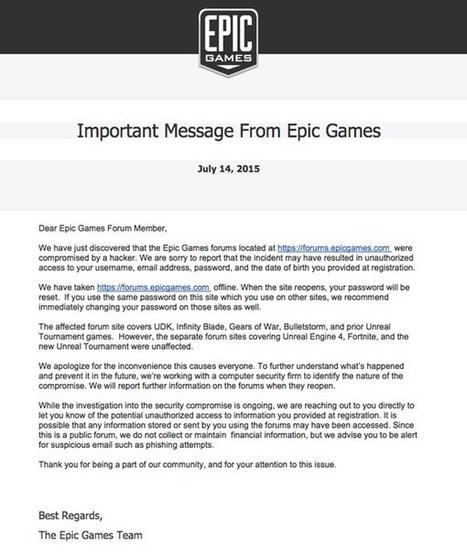



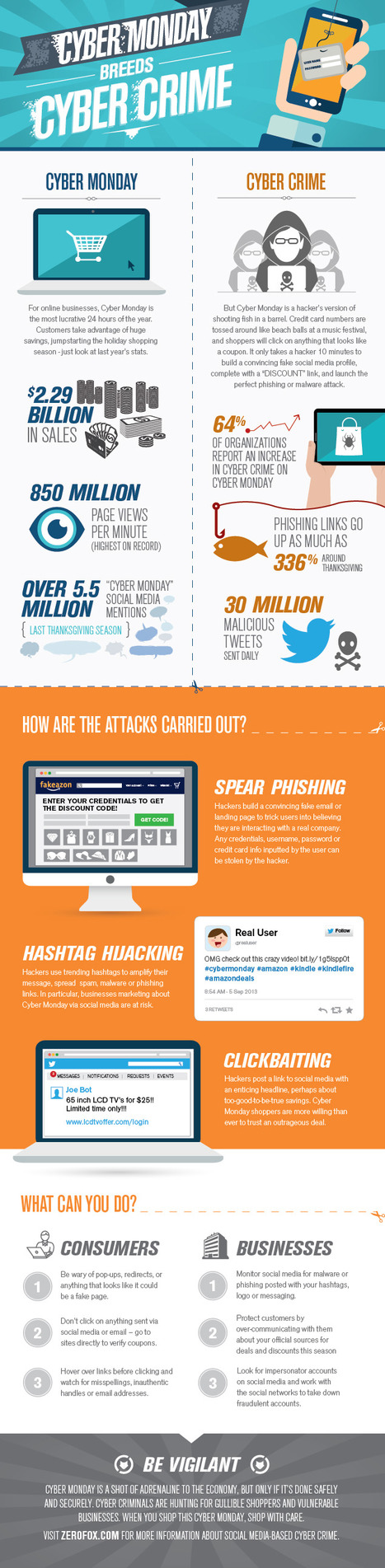
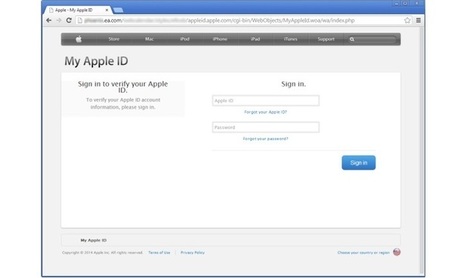



![L'hameçonnage : combien de personnes en sont victimes? [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/OXS9mYQx_J1s-8GXqYb4Gjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing
http://www.scoop.it/t/21st-century-learning-and-teaching/?&tag=Phishing