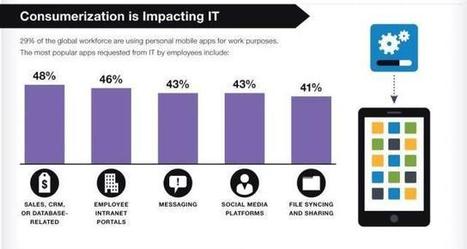
Der sorglose Umgang der Mitarbeiter mit mobiler Technologie gehört laut IDC neben Malware und Phishing-Attacken zu den häufigsten Risiken beim Thema Mobile Security in Unternehmen.

|
Scooped by Gust MEES |
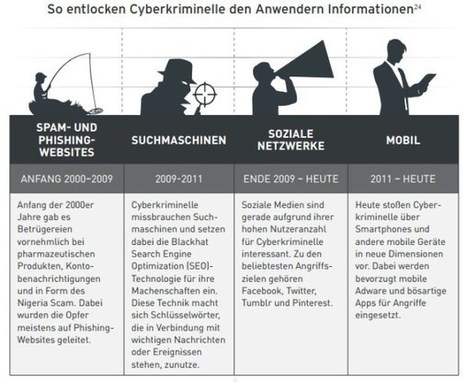
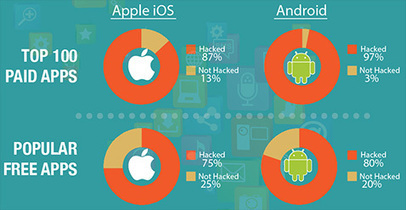
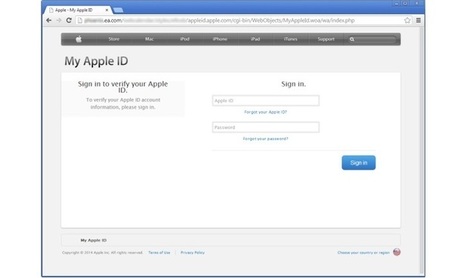
Zu den größten Sicherheitsrisiken aus Sicht der IT-Verantwortlichen zählen dabei Mobile Malware mit 42 Prozent, gefolgt von Phishing und Social Engineering mit 35 Prozent. Weitere 30 Prozent gaben an, dass das Fehlverhalten von Anwendern – vorsätzlich oder unabsichtlich – ein großes Risiko darstelle. Sie planen deshalb, die Mitarbeiter stärker für das Thema Mobile Security zu sensibilisieren.
Dies soll vor allem durch Trainings der Anwender und IT-Mitarbeiter sowie Richtlinien zur sicheren Nutzung mobiler Endgeräte geschehen - wobei hier die Wünsche der IT-Verantwortlichen und der User teils sehr unterschiedlich sind.
.
Learn more / Mehr erfahren:
.
.
Gust MEES's insight:
Zu den größten Sicherheitsrisiken aus Sicht der IT-Verantwortlichen zählen dabei Mobile Malware mit 42 Prozent, gefolgt von Phishing und Social Engineering mit 35 Prozent. Weitere 30 Prozent gaben an, dass das Fehlverhalten von Anwendern – vorsätzlich oder unabsichtlich – ein großes Risiko darstelle. Sie planen deshalb, die Mitarbeiter stärker für das Thema Mobile Security zu sensibilisieren.
Dies soll vor allem durch Trainings der Anwender und IT-Mitarbeiter sowie Richtlinien zur sicheren Nutzung mobiler Endgeräte geschehen - wobei hier die Wünsche der IT-Verantwortlichen und der User teils sehr unterschiedlich sind.
Learn more / Mehr erfahren:
- https://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
No comment yet.
Sign up to comment



 Your new post is loading...
Your new post is loading...


















![BYOD Security Issues [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/CaiNaHRcRGZDVZM2V3tufTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)







