New research has shown that the vast majority of businesses are exposing sensitive corporate data to cyber criminals by failing to implement effective BYOD strategies.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Related articles to 21st Century Learning and Teaching as also tools...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|

Gust MEES's curator insight,
May 14, 2013 5:11 PM
Read the full article to understand really...
Learn more:
- http://gustmees.wordpress.com/2013/05/13/visual-cyber-security-see-attacks-on-real-time/

asma jmari 's comment,
May 20, 2013 6:34 AM
believe it or not they do and hacking is more like a hobby some do it for fun and some just dedicate themselves to it and make it a job
|






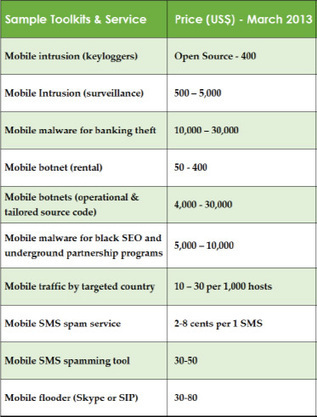






Meanwhile, nearly 80 per cent of respondents said they haven’t educated staff on the risks of BYOD.
Learn more:
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/