Based on daily monitoring of security for more than 4,000 clients, IBM has determined that DDoS attacks are on the rise
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
May 1, 2013 11:52 AM
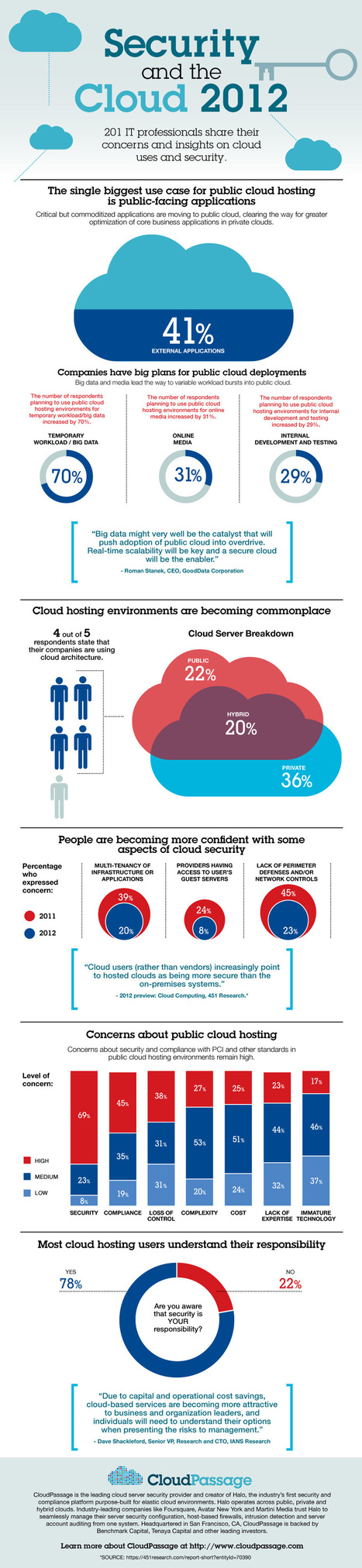
There has been a lot of talk both in the U.S. and internationally about a shortage in skilled IT professionals - with a predicted 864,000 IT vacancies in Europe alone by 2015.
What are these skills that organizations are looking for? This infographic by via resource highlights the top skills that make a successful information security professional and skills the future workforce will need to tackle emerging threats.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic
- http://www.scoop.it/t/21st-century-learning-and-teaching?tag=Infographi
- http://www.scoop.it/t/ict-security-tools
Check also:
- https://gustmees.wordpress.com/
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/
|

Gust MEES's curator insight,
June 23, 2013 10:28 AM
"This malware was found to have used a number of advanced techniques, which makes it interesting. The malware leverages Google Docs to perform redirection to evade callback detection." 
Jason Toy's curator insight,
June 23, 2013 11:04 AM
Interesting read. Looks like FireEye's sandboxing techniques paid off in this regard.

Gust MEES's curator insight,
March 4, 2013 12:29 PM
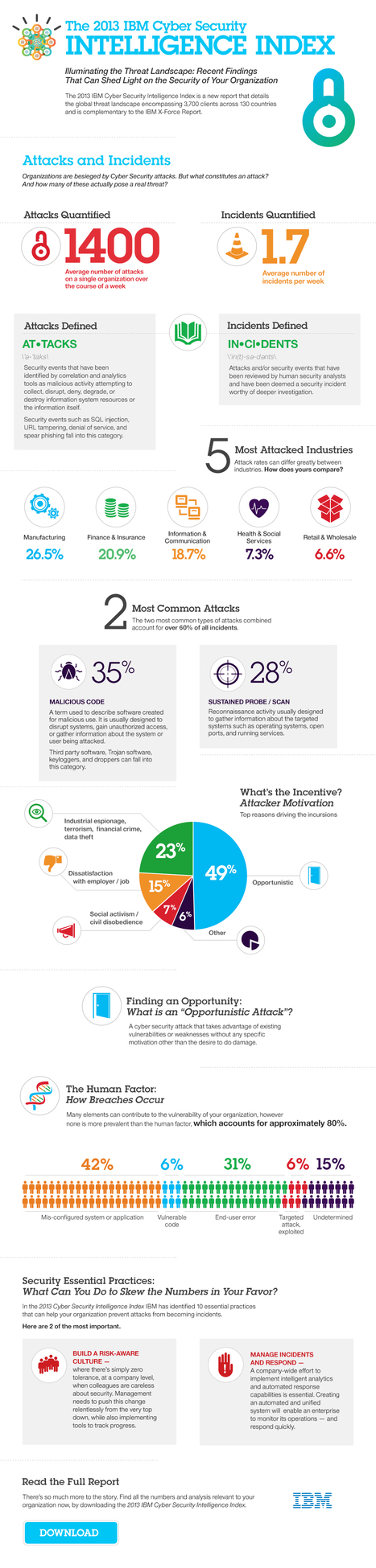
===> The weakest link in a security chain ist still and will still be the human!!! <=== |












Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic