Did we learn nothing from Arthur C. Clarke's 1968 sci-fi epic, 2001: A Space Odyssey?
In the film, astronauts on a mission to Jupiter discover that the HAL 9000 artificial intelligence computer that controls and automates all functions on the spacecraft starts seriously glitching. The astronauts get worried, HAL gets paranoid -- yada, yada, yada -- HAL kills everyone on the ship.
Windows as a Service: What's it mean?
Microsoft's decision to unveil a subscription licensing model for Windows 10 for enterprises could be a
READ NOW
The moral of the story is that when lives depend on fully automated systems, it's a good idea to keep an eye on those systems anyway. (And if that's not the moral of the story, it should have been.)
How do you use something that's fully automatic, anyway? What is the responsibility of the "user"? Can we just hand over control to the bots?
Recent events in the news suggest that when it comes to using our automatic products and features, some people are doing it wrong.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Artificial+Intelligence
http://www.scoop.it/t/securite-pc-et-internet?q=iot



 Your new post is loading...
Your new post is loading...



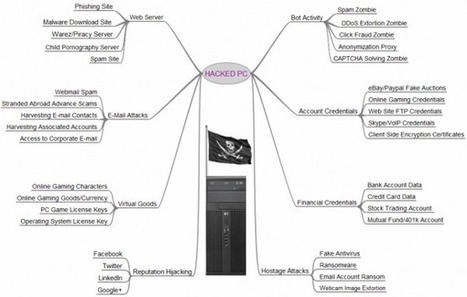


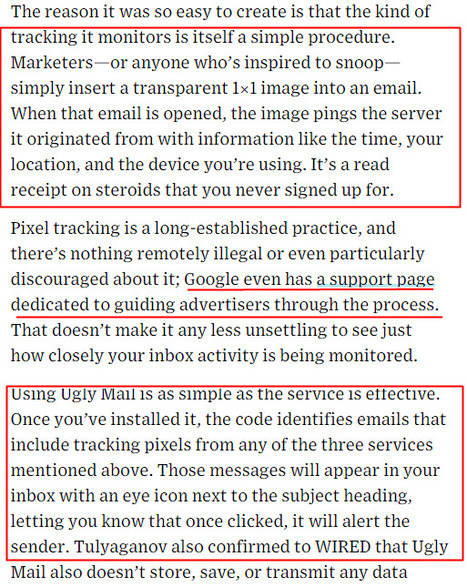





Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=Artificial+Intelligence
http://www.scoop.it/t/securite-pc-et-internet?q=iot