Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account

 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Current selected tag: 'cyberhygiene'. Clear
. . Read, think, learn and share over Social Media… Security is everyone's responsibility! We are ALL responsible for Internet's future! . ===> "Nothing in life is to be feared. It is only to be...
Gust MEES's insight:
Check also my other FREE courses here:
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/2012/05/31/securite-internet-guide-pratique/
- https://gustmees.wordpress.com/
Outside of the IT department, most users think that viruses are the only threat to their computing equipment. Many believe that malware doesn't affect mobile devices at all. An educated user is a safer user.
Gust MEES's insight:
===> An educated user is a safer user. <===
Most of them apply also to schools...
A very important point, with most people don't apply BUT which is necessary, a MUST is:
Educate your users - "The second most important BYOD security defense: user awareness, ...it might be the most important non-hardware, non-software solution available. An informed user is a user who behaves more responsibly and takes fewer risks with valuable company data, including email."
- http://www.zdnet.com/the-second-most-important-byod-security-defense-user-awareness-7000011738/
Check also:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/

Gust MEES's curator insight,
March 4, 2013 4:12 PM
===> An educated user is a safer user. <===
Most of them apply also to schools...
A very important point, with most people don't apply BUT which is necessary, a MUST is:
Educate your users - "The second most important BYOD security defense: user awareness, ...it might be the most important non-hardware, non-software solution available. An informed user is a user who behaves more responsibly and takes fewer risks with valuable company data, including email."
- http://www.zdnet.com/the-second-most-important-byod-security-defense-user-awareness-7000011738/
Check also:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
FutureGov – Transforming Government | Education | Healthcare...
Singapore holds its second annual Cyber Security Awareness Day (CSAD) today, with nationwide talks, exhibitions and roadshows promoting the agenda. The call-to-action garnered support from over 634,000 individuals and organisations.
The purpose of the CSAD, according to its website, is “to reinforce the security awareness messages and as a reminder of the threats in the cyber world”.
Talks have been held at public libraries throughout the city on protecting the “digital life”, on securing mobile devices, and on raising digital natives for parents. Visitors to the facebook page can also take part in several quizzes that test the participants’ knowledge of cyber security.
Read also:
Read more:
http://www.futuregov.asia/articles/2012/jul/11/singapore-marks-cyber-security-awareness-day-over-/
|
Governments are scrambling to shore up the defences of critical infrastructure systems as the web exposes them to greater scrutiny.
"For attackers, the potential pay-off for compromising these systems is very high," said Mr Wilhoit.
Governments are turning their attention to increasingly public vulnerabilities in such critical systems.
The US Department of Homeland Security has established a computer emergency response team that deals solely with threats to industrial control systems.
In the UK, government cash has been made available to help intelligence agencies and law enforcement deal with cyberthreats. Continue reading the main story A Cabinet Office spokesman said cyber-attacks were one of the "top four" threats to the UK's national security.
"Billions of pounds are being lost to the UK economy from cybercrime each year, including from intellectual property theft and cyber-espionage," he said. "Industry is by far the biggest victim."
Gust MEES's insight:
"The threat is there," he said, "It might not be biting you yet but you had better be ready for the day it does." Learn more: - http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/ 
Gust MEES's curator insight,
May 20, 2013 6:35 AM
"The threat is there," he said, "It might not be biting you yet but you had better be ready for the day it does."
Learn more:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattacks
By understanding the threats they face, organisations can mobilise IT systems and staff to defeat all but the most expert and determined adversary Cyber security is about humans, not just IT Computers do not make mistakes by themselves, so employees remain your biggest potential vulnerability. But they are also your strongest defence, if briefed properly.
Gust MEES's insight:
Cyber security is about humans, not just IT
Computers do not make mistakes by themselves, so employees remain your biggest potential vulnerability. But they are also your strongest defence, if briefed properly.
Check also:
- http://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/

Gust MEES's curator insight,
March 7, 2013 4:28 PM
Cyber security is about humans, not just IT Computers do not make mistakes by themselves, so employees remain your biggest potential vulnerability. But they are also your strongest defence, if briefed properly.
Check also:
- http://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmeesen.wordpress.com/2012/03/16/beginners-it-security-guide/
Businesses need extreme security measures to combat extreme threats. Here are ten best practices that provide defense against the majority of all security threats.
Gust MEES's insight:
===> An educated user is a safer user. <===
Most of them apply also to schools...
A very important point, with most people don't apply BUT which is necessary, a MUST is:
Educate your users - "The second most important BYOD security defense: user awareness, ...it might be the most important non-hardware, non-software solution available. An informed user is a user who behaves more responsibly and takes fewer risks with valuable company data, including email."
- http://www.zdnet.com/the-second-most-important-byod-security-defense-user-awareness-7000011738/
Check also:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/

Gust MEES's curator insight,
March 4, 2013 4:04 PM
Most of them apply also to schools...
A very important point, with most people don't apply BUT which is necessary, a MUST is:
Educate your users - "The second most important BYOD security defense: user awareness, ...it might be the most important non-hardware, non-software solution available. An informed user is a user who behaves more responsibly and takes fewer risks with valuable company data, including email."
- http://www.zdnet.com/the-second-most-important-byod-security-defense-user-awareness-7000011738/
Check also:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmees.wordpress.com/2012/07/07/bring-your-own-device-advantages-dangers-and-risks/
|



![How to keep your business safe – the one checklist all SMBs should have [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/Sn5HIth7pKg7GHGiGeIaXzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



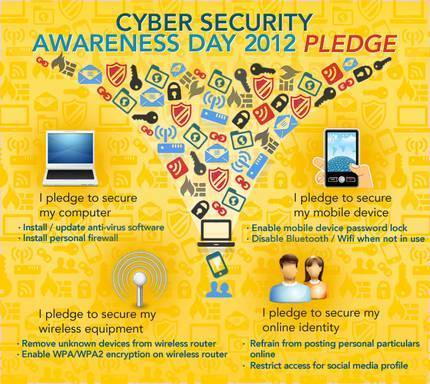







This is ALSO for EDUCATION and watch "Point 10" ===> SCREEN EMPLOYEES THOROUGHLY! <=== Conduct thorough background and reference checks before hiring new employees!!!
I said already that it is VERY IMPORTANT that students have the basics of Internet-Safety and ALSO of Cyber-Security as employers need employees who have that knowledge! Prepare THEM for the REAL-WORLD!!!
Learn more:
- http://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
- http://gustmees.wordpress.com/2013/06/02/social-media-students-take-care/
- http://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/
- http://gustmees.wordpress.com/2013/06/13/stop-theoretical-testing-and-test-for-future-skilled-and-educated-workers/
- http://gustmees.wordpress.com/2013/06/02/social-media-students-take-care/
- http://gustmees.wordpress.com/2012/12/30/why-and-how-teachers-should-start-learning-and-teaching-cyber-security/
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic