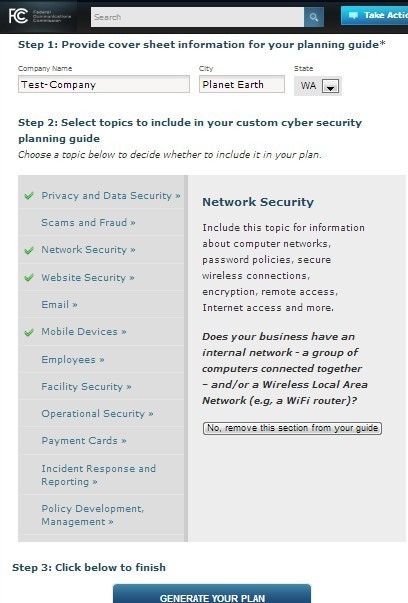
Information technology and high-speed Internet are great enablers of small business success, but with the benefits comes the need to guard against growing cyber threats. As larger companies take steps to secure their systems, less secure small businesses are easier targets for cyber criminals. In October 2012, the FCC re-launched Small Biz Cyber Planner 2.0, an online resource to help small businesses create customized cybersecurity plans. Use this tool to create and save a custom cyber security plan for your company, choosing from a menu of expert advice to address your specific business needs and concerns.
==================================================
Gust MEES
A MUST for Education and Business! Especially for "Bring Your Own Device" (BYOD)
==================================================



 Your new post is loading...
Your new post is loading...















![Why You Should Care About Mobile Security [INFOGRAPHIC] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/bCDzCBQu4qMgWJAbygdm2jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)















A MUST also for Education, very easy to generate and which gives YOU the necessary knowledge to have a good Cyber-Security, please read it and test it!