 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Für die Absicherung von iPhone und iPad ist seit dem iPhone 5s ein spezieller Co-Prozessor zuständig, auch Secure Enclave genannt. Nach Berichten soll es allerdings jetzt dem für Jailbreaks bekannten Team Pangu gelungen sein, diesen Sicherheitschip zu knacken. Das sollte eigentlich nicht möglich sein und wäre für Apples Sicherheitskonzept ein schwerer Schlag. Der Chip ist vom System abgeschottet, speichert sensibelste Daten wie Fingerabdruckdaten, FaceID-Daten, Verschlüsselungs-Keys und verspricht Datensicherheit und sicheres Apple Pay. Offensichtlich ist durch diesen Fehler aber der Zugriff auf die Secure Enclave möglich, was sogar ein Entschlüsseln eines iOS-Gerätes ermöglichen würde.
Was die Entdeckung besonders brisant macht: Der Fehler soll den so genannten ROM der Secure Enclave betreffen, einen Nur-Lese-Speicher, den Apple nicht aktualisieren kann. Durch ein Update kann man den Fehler wohl nicht beheben, allenfalls durch das Austauschen des Chips. Auch die Sicherheitschips der Macs sollen betroffen sein. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
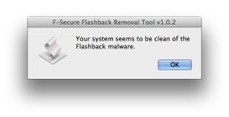
Apple has delivered - or so it says - on its promise to provide a Flashback malware removal tool, wrapped in another Java update.

|
Scooped by
Gust MEES
|
This Java security update removes the most common variants of the Flashback malware. ...

|
Scooped by
Gust MEES
|
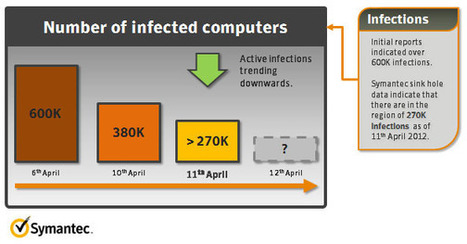
News that nearly two percent of all Mac users have had their computers infected by the Flashback malware which roped them into a 600K strong botnet has hit the Mac community with the realization that ===> their machines are not as secure as they believed and hoped they are. <=== Meanwhile, the Flashback botnet has shrunk in the last few days and as of yesterday, counts less than 270k infected machines. According to Symantec, part of the reason for this dramatic decrease is the fact that a number of security firms have executed sinkholing operations against the botnet, but the biggest reason likely lies in the fact that many Mac users have heard the news and proceeded to scan and disinfect their machines.

|
Scooped by
Gust MEES
|
Dr.Web Light Scanner for Mac OS X
Dr.Web Light for Mac OS X is a reliable way to protect your Mac from a variety of threats.
The scanner is based on the latest virus detection and removal technologies. You can use it to scan your system whenever you like. The scanner virus databases are automatically updated with signatures of actual threats on a regular basis. To make protection against unknown viruses even stronger, a heuristic analyzer is implemented.

|
Scooped by
Gust MEES
|
Fünf Jahre alte Samba-Lücke bedroht Mac OS X und Linux
Ein Angreifer kann über die Schwachstelle Schadcode einschleusen und ausführen. Die Open-Source-Software, die anderen Betriebssystemen die Nutzung von freigegebenen Windows-Dateien und -Druckern ermöglicht, ist in vielen Linux-Distributionen und ===> Apples Mac OS X Server <=== enthalten.
Problem: Betroffene Netzwerkdrucker und -speicher lassen sich möglicherweise aktualisieren.

|
Scooped by
Gust MEES
|
The new free tool adds to the growing community effort to help affected Mac users remove the malware from their systems. Read this blog post by Topher Kessler on MacFixIt. This new tool by F-Secure is another advancement by the Mac community against this threat that accompanies not only manual instructions and help from community members, but also swiftly updated definitions for Sophos, ClamXav, VirusBarrier, and other malware scanners for detecting the malware. On Apple's end, even though the extent of this infection stemmed largely from Apple's delay in issuing a patch for known Java vulnerabilities, the company finally released the patch and has further announced its own Flashback removal tool is in the works.
It's hope that these, and the continuing efforts by the Apple community, will reduce the prevalence of this infection to a minimum.

|
Scooped by
Gust MEES
|
Nobody is safe, but you can stop the spread before it overtakes your precious. Mac fans recently got a little taste of what it's like to be a Windows user. That's right, a virus targeting Mac OS X is making the rounds. The latest stats from security companies tracking the virus put the number of infected Macs at well over half a million. That's nowhere near the level of some Windows viruses, but it's widespread enough to be a concern for Mac users.
The virus is known as Flashback and it can hijack your Mac without so much as an administrative password. It manages to pull off its attack by exploiting a vulnerability in Java. Oracle, which makes Java, quickly issued a fix for the problem back in February. Unfortunately, because Apple ships its own version of Java (and therefore must provide its own patches), Mac users had to wait on Apple's fix, which didn't arrive until last week.
===> The slow fix from Apple gave Flashback time to propagate and led to well over half a million infected machines — one of which could be yours. <===

|
Scooped by
Gust MEES
|
A look at what the Mac Flashback Trojan could do to infected computers. So what is the worst it could do? Although the Trojan is now only conducting click fraud scam by hijacking people’s search engine results inside their web browsers, it has the potential to do greater damage, such as stealing banking or login credential. If the botnet remains connected to computers, cybercriminals could send new malware to their systems that cause bigger problems.

|
Scooped by
Gust MEES
|
Nach der Enttarnung des Flashback-Trojaners hat Apple nun die Sicherheitslücke geschlossen und arbeitet mit Hochdruck an einem Entfernungs-Tool.
The explosion in development and adoption of smartphones and tablets for both personal and business use in the past two years is both a blessing and a curse to IT departments globally. Known as the Bring Your Own Device (BYOD) phenomenon, on one hand, there is an opportunity for greatly increased productivity and decreased costs. ===> On the other, there are increased security risks, management issues and even data and device ownership and governance issues. <===
Via Gust MEES

|
Scooped by
Gust MEES
|
Kaspersky Lab -- which is offering the free tool -- counted up to 670,000 infected OS X machines in the botnet last week; today has seen just 227,493 so far, up from 208,301 yesterday. Over the weekend, Kaspersky saw a major dip in the number of active infected Macs, from a head count on Friday, April 6, of 650,748, to 248,723 on Saturday, and then 237,103 on Sunday.

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
Apple has released a fresh Java update, designed to remove the Flashback Trojan malware that exposed Macs to a botnet.

|
Scooped by
Gust MEES
|
As promised, Apple has released a tool to remove Flashback from infected Macs.

|
Scooped by
Gust MEES
|
There are millions of Mac users who are running vulnerable old versions of Java, which are being exploited by the Flashback malware. ===> "50% of all visitors of our Online #FlashbackChecker http://flashbackcheck.com are running a vulnerable version of Java," Aleks Gostev, chief security expert at Kaspersky said on Twitter Wednesday. <===

|
Scooped by
Gust MEES
|
Rund 800 Schweizer Mac-Rechner sind gemäss Switch mit dem Flashback-Trojaner verseucht. ==> Deren Besitzer werden nun via Internetprovider informiert. <=== Gust MEES: so sollte es überall auf der Welt sein! Kunden sollten informiert werden!

|
Scooped by
Gust MEES
|
F-Secure Security Labs brings you the latest online security news from around the world. Ensure that you are up-to-date with the latest online threats to guarantee your online wellbeing. We have created a free tool that automates the detection and removal of the widespread Flashback Mac OS X malware.

|
Scooped by
Gust MEES
|
La firme de Cupertino a publié une page spéciale Flashback sur son site de support et indique préparer son propre patch. Apple aurait aussi contacté des FAI et des bureaux d'enregistrements pour tenter d'éradiquer le botnet. Apple sort enfin de son silence. Quelques jours après avoir poussé, sans faire référence à Flashback, une mise à jour de sécurité pour Java sur Mac (voir notre article sur le botnet Flashback), Apple hausse un peu le ton. Et publie sur son site de support une page spécifique au fameux malware qui, d’après Dr.Web, infecterait désormais quelque 655 700 machines. agrandir la photo
===> Une drôle de page tout de même qui n’explique pas comment faire pour savoir si l’on a été effectivement infecté par Flashback, ni comment supprimer le virus de sa machine ! <===

|
Scooped by
Gust MEES
|
Windows has been the target of malware for decades. This has resulted in a more hardened system and a better user awareness.
On the other hand, OS X has not really needed to go through all the troubles of crime fighting until recently.
===> Now, with its growing market share and lower user awareness, it is clear that OS X is becoming more and more attractive to malware authors. <===

|
Scooped by
Gust MEES
|
OSX.Flashback initially arrived on the scene in late 2011. It has come a long way from its humble beginnings as a social-engineering scam trying to pass off as a fake Flash update using digital certificates purporting to come from Apple.

|
Scooped by
Gust MEES
|
In response to the recent discovery of the Flashfake botnet, Kaspersky Lab has announced the availability of its free Flashfake Removal Tool.

|
Scooped by
Gust MEES
|
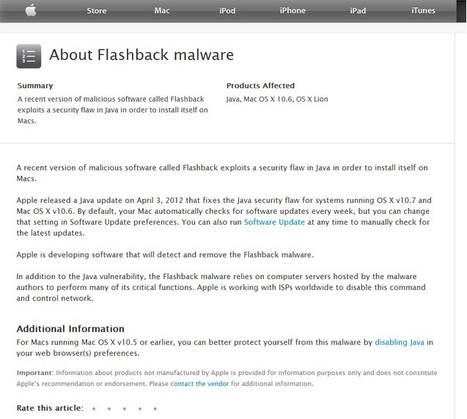
Apple said Tuesday it's developing a solution to combat the Flashback malware that experts say has infected around 600,000 Mac computers around the world.

|
Scooped by
Gust MEES
|
Apple is developing a tool to "detect and remove" a Trojan that is believed to have infected around 650,000 Macintosh computers. It said it is working with internet service providers (ISPs) to disrupt the command network being used by hackers to exploit the malware. Trojans are infections that can expose computers to control by hackers. It is Apple's first statement on the threat. It issued patches to prevent the malware's installation last week. The two security updates were released ===> eight weeks after Java's developer Oracle issued a fix for other computer systems. <===

|
Scooped by
Gust MEES
|
Apple a indiqué discrètement qu’il mettra bientôt à la disposition des utilisateurs Mac un outil de détection ...
|



 Your new post is loading...
Your new post is loading...


























Für die Absicherung von iPhone und iPad ist seit dem iPhone 5s ein spezieller Co-Prozessor zuständig, auch Secure Enclave genannt. Nach Berichten soll es allerdings jetzt dem für Jailbreaks bekannten Team Pangu gelungen sein, diesen Sicherheitschip zu knacken. Das sollte eigentlich nicht möglich sein und wäre für Apples Sicherheitskonzept ein schwerer Schlag. Der Chip ist vom System abgeschottet, speichert sensibelste Daten wie Fingerabdruckdaten, FaceID-Daten, Verschlüsselungs-Keys und verspricht Datensicherheit und sicheres Apple Pay. Offensichtlich ist durch diesen Fehler aber der Zugriff auf die Secure Enclave möglich, was sogar ein Entschlüsseln eines iOS-Gerätes ermöglichen würde.
Was die Entdeckung besonders brisant macht: Der Fehler soll den so genannten ROM der Secure Enclave betreffen, einen Nur-Lese-Speicher, den Apple nicht aktualisieren kann. Durch ein Update kann man den Fehler wohl nicht beheben, allenfalls durch das Austauschen des Chips. Auch die Sicherheitschips der Macs sollen betroffen sein.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security