Multi-platform threat exploits old Java flaw, gains persistence.
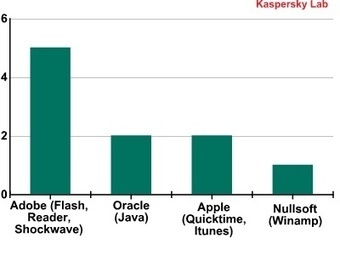
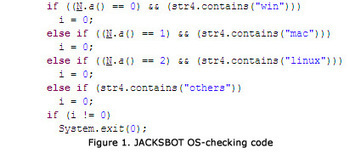
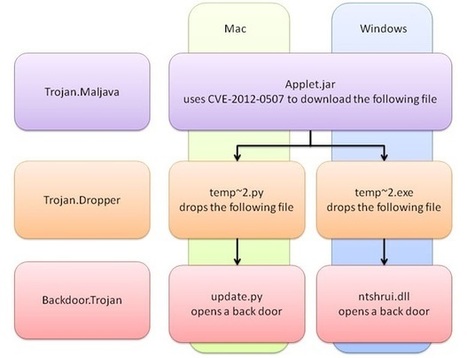
Researchers have uncovered a piece of botnet malware that is capable of infecting computers running Windows, Mac OS X, and Linux that have Oracle's Java software framework installed.
The cross-platform HEUR:Backdoor.Java.Agent.a, as reported in a blog post published Tuesday by Kaspersky Lab, takes hold of computers by exploiting CVE-2013-2465, a critical Java vulnerability that Oracle patched in June. The security bug is present on Java 7 u21 and earlier. Once the bot has infected a computer, it copies itself to the autostart directory of its respective platform to ensure it runs whenever the machine is turned on.
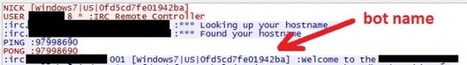
Compromised computers then report to an Internet relay chat channel that acts as a command and control server.
Via Gust MEES



 Your new post is loading...
Your new post is loading...













Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux