 Your new post is loading...
 Your new post is loading...
Our colleagues at SophosLabs pointed us at a interesting item of malware the other day, namely a data-stealing Trojan aimed at Mac users.
Paul Ducklin looks at how the attack unfolds...
The Oslo Freedom Forum is an annual event "exploring how best to challenge authoritarianism and promote free and open societies." This year's conference (which took place May 13-15) had a workshop for freedom of speech activists on how to secure their devices against government monitoring. During the workshop, Jacob Appelbaum actually discovered a new and previously unknown backdoor on an African activist's Mac.
Our Mac analyst (Brod) is currently investigating the sample.
It's signed with an Apple Developer ID.

|
Scooped by
Gust MEES
|
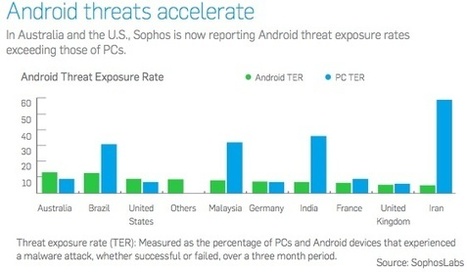
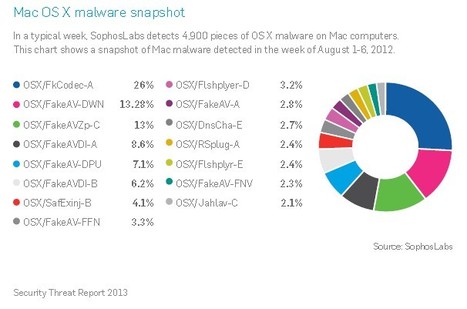
Attackers have expanded their attacks beyond the Windows platform to include Mac OS X and Android. 27 Percent of All Cybercrime Linked to the ‘Blackhole’ Exploit Kit, Sophos said. Even though the overall market share for Mac OS X remains small compared to other platforms, the number of Mac threats are growing as more users switch. Flashback, the malware that reportedly infected hundreds of thousands of Apple systems in April was the largest mass attack this year, but it's not the only Mac malware out there. In a typical week, SophosLabs detects 4,900 pieces of OS X malware on Mac computers. ===> In a snapshot of Mac malware detected over a one-week period in August, SophosLab detected various variants of fake antivirus, codecs and Flash player. <=== Read more, a MUST: http://www.securityweek.com/sophos-blackhole-will-get-more-complex-android-and-mac-os-are-prime-attack-targets

|
Scooped by
Gust MEES
|
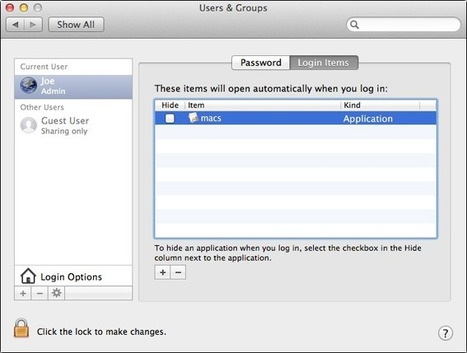
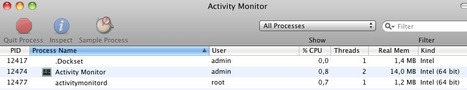
A sample of a new Mac spyware called OSX/Dockster.A was found today on Virus Total. This trojan is currently considered low risk as it is not known to have infected users. It has backdoor functiona...

|
Scooped by
Gust MEES
|
The malware threat on Macs is real, and should not be underestimated. SophosLabs, is a new variant of the OSX/Imuler Trojan horse. In the past, earlier variants of the OSX/Imuler malware has been spread via topless photos of a Russian supermodel or embedded deep inside boobytrapped PDF files. If your Mac was successfully infected by malware like this, you have effectively given remote control of your computer and your data to an invisible and unknown party. ===> They could steal files from your Mac, spy on your emails, and plant further malware onto your systems. <=== Read more, a MUST: http://nakedsecurity.sophos.com/2012/11/13/new-mac-trojan/

|
Scooped by
Gust MEES
|
Crisis malware lets attackers install without an administrator password and intercept email, IM, and other communications. Mac users, beware new malware targeting Apple OS X systems that's disguised as an Adobe Flash Player installer.
That warning comes via antivirus software vendor Kaspersky Lab, which said it first spotted the Crisis malware--also known as Morcut--last week. While not widespread, the malware's ability to intercept email and IM, among other features, demonstrates that malicious applications written to target Macs can be just as powerful as malware that comes gunning for PCs. Read more, a MUST...: http://www.informationweek.com/news/security/attacks/240004583?cid=RSSfeed_IWK_security

|
Scooped by
Gust MEES
|
A new Trojan known as “Sabpab” could hurt Mac users who run Java and Microsoft Word. Security researchers are warning users to make sure their computers ===> have the latest software updates from both Apple and Microsoft, <=== and to use anti-virus software. In some cases, manual removal of Sabpab may be needed. Word about Sabpab comes on the heels of another nasty piece of malware, Flashback, that infected up to as many as 600,000 Macs, security experts said, by exploiting a vulnerability in Java software. Apple last week issued a software-base removal tool for that malware, which can be used by criminals to steal personal information, including passwords. Read more...

|
Scooped by
Gust MEES
|
D'autres chevaux de Troie, moins graves que Flashback, ont visé Mac OS X - Malware - Après avoir découvert le Cheval de Troie Flashback sur Mac, les...

|
Scooped by
Gust MEES
|
Découvert par Kaspersky, ce nouveau malware qui cible les Mac exploite une faille de sécurité Java. Le répit aura été de courte durée. À peine Apple avait-il publié une mise à jour de Java contenant un logiciel de suppression du malware Flashback qu’un nouveau fléau était découvert. Baptisé SabPub, il a été découvert par l’éditeur Kaspersky qui en a repéré deux variantes. Comme Flashback, SabPub passe par une faille de sécurité de Java au moyen d’un document Word piégé. Le Mac infecté va ensuite se connecter à un site web depuis lequel sont envoyées des commandes. Un pirate peut notamment obtenir des captures d’écran du Mac de la victime. Cependant, le mode de diffusion de ce malware via des documents Word piégés rend sa propagation moins puissante que celle de Flashback qui a touché 600 000 machines de par le monde.

|
Scooped by
Gust MEES
|
A week after the Flashback Trojan began running rampant on Macintosh computers, the malware appears to be in remission.
The explosion in development and adoption of smartphones and tablets for both personal and business use in the past two years is both a blessing and a curse to IT departments globally. Known as the Bring Your Own Device (BYOD) phenomenon, on one hand, there is an opportunity for greatly increased productivity and decreased costs. ===> On the other, there are increased security risks, management issues and even data and device ownership and governance issues. <===
Via Gust MEES

|
Scooped by
Gust MEES
|
More than half a million Macs are infected with the data-stealing Flashback Trojan, according to new analysis.
In the face of new threats aimed at OS X, a security expert has warned that Mac users may be even more vulnerable than Windows users. Because Windows users are more likely to be running up-to-date anti-virus programs, Graham Cluley of Sophos says that many Mac users are missing a "valuable safety net". In the face of several new threats targeting Mac OS X that have been discovered in recent weeks, Mac users should make sure that they have some form of protection, Cluley said. However, keeping your computer safe from cybercriminals isn't just a case of having anti-virus programs installed - it's about making sensible choices as well. As we have seen on the Windows platform, the majority of the attacks do not exploit any weakness in the operating system but instead take advantage of the bug in people's brains. ===> Mac users can be just as easily duped as their Windows cousins into making poor choices, and could end up infected as a result, Cluley told Macworld. <=== Use antivirus programs!
|

|
Scooped by
Gust MEES
|
Right-to-left override (RLO) is a special character used in bi-directional text encoding system to mark the start of text that are to be displayed from right to left. It is commonly used by Windows malware such as Bredolab and the high-profile Mahdi trojan from last year to hide the real extension of executable files. Check out this Krebs on Security post for more details on the trick.
We've spotted a malware for Mac using the RLO trick. It was submitted to VirusTotal last Friday.

|
Scooped by
Gust MEES
|
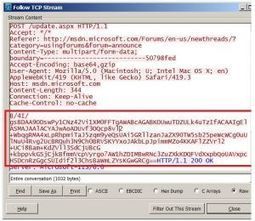
Backdoor took screenshots, sent them to attackers.
Read about the latest cyber security trends in the Sophos Security Threat Report 2013. Most malware developers have found it more profitable to attack Windows than to learn new skills needed to target the smaller OS X user community. ===> But Macs are finding a new home in thousands of businesses and government agencies, and malware authors are paying attention. <===
Forrester Research analyst Frank Gillette recently reported that “almost half of enterprises (1,000 employees or more) are issuing Macs to at least some employees—and they plan a 52% increase in the number of Macs they issue in 2012.”
===> Even more Macs are arriving unofficially through bring your own device arrangements, where they are often an executive’s device of choice for accessing web or cloud applications. <=== ===> Growing Mac usage means many IT organizations must objectively assess, mitigate, and anticipate Mac-related malware threats for the first time. And the risks are clearly increasing! <=== ============================================= Gust MEES Check also my Curation about it: - http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
=============================================
Read more, a MUST: http://www.sophos.com/en-us/medialibrary/PDFs/other/sophossecuritythreatreport2013.pdf?id=ee65b697-1d30-4971-b240-ce96b5e529aa&amp;amp;amp;dl=true
McAfee publie son rapport trimestriel sur les menaces informatiques, qui analyse notamment les techniques du cybercrime et l’évolution mondiale des cyberattaques. Le rapport dévoile de nouveaux détails sur l’opération « High Roller », ainsi que des chiffres en matière de logiciels malveillants visant les mobiles, qui ont quasiment doublé par rapport au trimestre précédent, et la hausse sans précédent des violations des bases de données. McAfee Labs a également constaté une hausse importante de certaines catégories de logiciels malveillants, dont les logiciels de demande de rançons ou ransomware et les fichiers binaires signés. ===> Les rootkits et les logiciels malveillants ciblant les Mac continuent eux aussi d’augmenter, à l’instar des chevaux de Troie voleurs de mots de passe et des logiciels malveillants autoexécutables, qui ont enregistré une hausse considérable. <=== En savoir plus : http://www.globalsecuritymag.fr/Rapport-trimestriel-McAfee,20121114,33708.html

|
Scooped by
Gust MEES
|
Kate Bevan: For too long Mac users have been complacent about malware – it's time they woke up to the threat from trojans like Flashback... ===> Mac users should 'become responsible members of the wider computing community.' <=== Read more...

|
Scooped by
Gust MEES
|
Java update is no protection against new SabPub Mac Trojan! SabPub Mac Trojan is spreading via Word documents, using an ancient vulnerability... Read more...

|
Scooped by
Gust MEES
|
Given the attention that the Flashback Mac malware has received since the discovery of the 600K strong botnet of computers infected with it and the number of tools that various security firms and Apple issued for its removal, it's somewhat disheartening to hear that===> the botnet still counts around 140,000 zombies. <=== Read more...

|
Scooped by
Gust MEES
|
Alors qu'Apple et plusieurs éditeurs en sécurité viennent de publier des correctifs pour venir à bout du cheval de Troie Flashback, un nouveau malware s'invite actuellement sur Mac OS X. Son nom : Backdoor.OSX.SabPub.a.

|
Scooped by
Gust MEES
|
we can confirm yet another Mac malware in the wild - Backdoor.OSX.SabPub.a being spread through Java exploits. This new threat is a custom OS X backdoor, which appears to have been designed for use in targeted attacks.

|
Scooped by
Gust MEES
|
Der kürzlich entdeckte Trojaner hat binnen weniger Tage über 550.000 Mac-Rechner infiziert und zu Mitgliedern eines mittlerweile stillgelegten Botnetz gemacht.

|
Scooped by
Gust MEES
|
Doctor Web exposes 550 000 strong Mac botnet
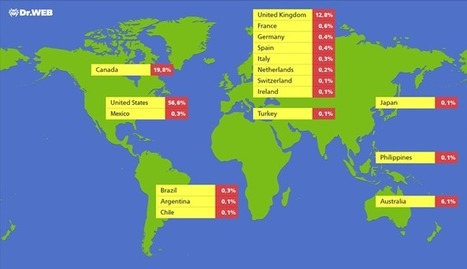
April 4, 2012 Doctor Web—the Russian anti-virus vendor—conducted a research to determine the scale of spreading of Trojan BackDoor.Flashback that infects computers running Mac OS X. Now BackDoor.Flashback botnet encompasses more than 550 000 infected machines, most of which are located in the United States and Canada. This once again refutes claims by some experts that there are no cyber-threats to Mac OS X. Systems get infected with BackDoor.Flashback.39 after a user is redirected to a bogus site from a compromised resource or via a traffic distribution system. JavaScript code is used to load a Java-applet containing an exploit. Doctor Web's virus analysts discovered a large number of web-sites containing the code.
|
 Your new post is loading...
Your new post is loading...
 Your new post is loading...
Your new post is loading...































Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security