 Your new post is loading...
 Your new post is loading...
A major security flaw in Dell’s firmware updating and operating recovery software, BIOSConnect, potentially exposes tens of millions of devices that Dell preinstalled it on.
BleepingComputer reported on Thursday that researchers with security firm Eclypsium discovered a flaw in BIOSConnect, which is part of Dell’s standard SupportAssist software and updates the firmware on a computer’s system board, that could allow attackers to remotely execute malicious code. In a report, the researchers wrote that the vulnerability was so severe it could “enable adversaries to control the device’s boot process and subvert the operating system and higher-layer security controls,” which would give them control “over the most privileged code on the device.”
There are four separate vulnerabilities, one of which involves insecure connections between a BIOS being updated and Dell’s servers that allow an attacker to redirect the machine to a maliciously modified update package. The remaining three are classified as overflow vulnerabilities. Eclypsium rated the bugs as severe security threats. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet
Via Gust MEES
On pourrait croire que depuis les scandales liés à Superfish et Edellroot, les fabricants d’ordinateurs ont renforcé les contrôles sur les logiciels préinstallés vendus avec leurs machines. Mais si l’on croit les chercheurs des équipes de Duo Security, la lutte contre les bloatwares n’est pas prête de se terminer.
Rappelons que les constructeurs proposent effet tous leurs machines avec des logiciels préinstallés, généralement qualifiés de bloatware ou crapware. Ces utilitaires à l’utilité parfois relative permettent généralement de contrôler l’état de la machine ou proposent certains services annexes à l’utilisateur.
L’étude menée par Duo Security porte sur une dizaine de machines achetées dans le commerce auprès de différents constructeurs : Lenovo, Dell, HP ainsi que Acer et Asus. Toutes sont livrées avec des logiciels préinstallés, que les chercheurs ont analysés afin de déterminer lesquels pouvaient présenter des failles de sécurité.
La conclusion est sans appel « Tous les constructeurs livraient leurs machines avec un logiciel présentant au moins une faille de sécurité permettant à une attaque de type man in the middle d’exécuter du code sur la machine avec un haut niveau de privilège » expliquent ainsi les chercheurs dans un post de blog. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Bloatware
Via Gust MEES
La CNPD prévient d’une fuite de données d’une grande envergure au départ des jouets VTech, en raison d’une faille de sécurité. 9.204 profils sont touchés pour le Grand-Duché. Mode d’emploi pour les parents concernés.
La protection des données et, à l’inverse, les fuites possibles en cas de lacune des installations informatiques peuvent prendre des proportions importantes. La Commission nationale de protection des données (CNPD) indique en effet mercredi soir, dans un communiqué commun avec Securitymadein.lu, qu’une importante fuite de données a été détectée auprès de la société VTech.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Vtech
http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES
Via Gust MEES
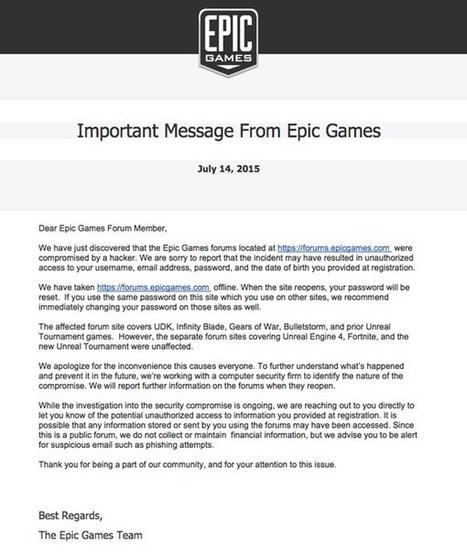
If you're an avid video gamer, chances are that you know of Epic Games. They're the developers of popular games such as Infinity Blade, Gears of War, Unreal Tournament… and – if you’re as old as me – you might even remember their founder Tim Sweeney’s classic DOS era shareware gameZZT.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Phishing
Via Gust MEES
OPSWAT’s latest market share report ranks Avast as the top vendor and finds that 90% of devices haven’t updated their antivirus definitions in the last seven days.
Via Gust MEES
Security researchers have released a report examining a social engineering operation designed to trick admins into installing backdoor malware called CrytoPHP by way of of tainted CMS plugins and themes for WordPress, Joomla and Drupal.
The attackers lure targets into publishing the pirated themes and plugins by providing them for free, offerings that usually incur a fee for use.
“After being installed on a webserver the backdoor has several options of being controlled which include command and control server communication, mail communication as well as manual control,” the researchers revealed.
Via Gust MEES
Recently, a report has emerged on the fact that certain applications available on Android are vulnerable to the Heartbleed Bug, and it seems that more... Moreover, the team claims that the issue is present even on handsets and tablets that do not run under the affected platform iteration itself.
They note that 273 applications in Google Play were found to be bundled with the standalone affected OpenSSL library, thus being vulnerable on any device on which they are installed.
“In this list, we see last year’s most popular games, some VPN clients, a security app, a popular video player, an instant message app, a VOIP phone app and many others,” the TrendLabs notes in the aforementioned blog post.
Learn more:
Via Gust MEES
|
Tous les appareils utilisant la norme Bluetooth 4.0 à 5.0 sont vulnérables. Les correctifs ne sont pas disponibles pour l'heure.
Les organisations à l'origine de la technologie sans fil Bluetooth viennent de publier des conseils sur la manière dont les vendeurs d'appareils peuvent atténuer une nouvelle attaque contre les appareils compatibles Bluetooth. Nommée BLURtooth, il s'agit d'une vulnérabilité dans un composant de la norme Bluetooth nommé Cross-Transport Key Derivation (CTKD).
Ce composant est utilisé pour configurer les clés d'authentification lors de l'appairage de deux appareils compatibles Bluetooth. Ce composant fonctionne en établissant deux jeux de clés d'authentification différents pour la norme Bluetooth Low Energy (BLE) et la norme Basic Rate/Enhanced Data Rate (BR/EDR). Le rôle du CTKD est de préparer les clés et de laisser les appareils jumelés décider quelle version de la norme Bluetooth ils veulent utiliser. La fonction "bi-mode" de Bluetooth est la principale utilité de ce système.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Bluetooth https://www.scoop.it/topic/securite-pc-et-internet/?&tag=BLURtooth
Via Gust MEES
Des chercheurs de Check Point ont identifié de nouvelles vulnérabilités dans les dispositifs Android. Certifi-gate permet à des hackers de prendre le contrôle d'un appareil.
«Certifi-gate», tel est le nom donné à un vulnérabilité découverte par des chercheurs de Check Point au sein du système d'exploitation Android. Elle permet à des applications pour offrir aux pirates un accès sans restriction à l'appareil et ainsi, selon Check Point, «dérober des données personnelles, localiser les appareils, activer le microphone pour enregistrer des conversations, et plus encore».
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Certifi-gate
http://www.scoop.it/t/securite-pc-et-internet/?tag=Android
Via Gust MEES
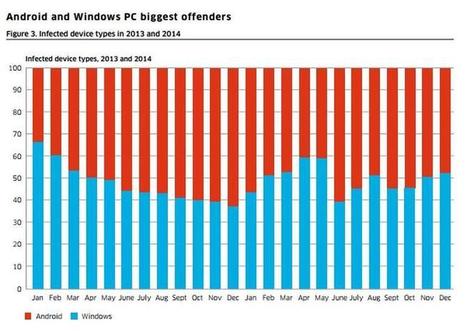
Around 16 million mobile devices worldwide was hit by malware as at the end of 2014, while attacks on communications networks rose during the year, according to new research by Alcatel-Lucent. . Less than 1 percent of infections came from iPhone and Blackberry smartphones. Although, new vulnerabilities, such as the 'Find My iPhone' exploit discovered last year, have emerged in the past 12 months, showing that they are not immune from malware threats.
Via Gust MEES
A new year begins at midnight and Threatpost highlights seven things you're bound to contend with in 2015.
===> Forewarned is Forearmed!!! <===
Via Gust MEES
Security researchers have discovered a new type of "Man-in-the-Middle" (MitM) attack in the wild targeting smartphone and tablets users on devices running either iOS or Android around the world.
The MitM attack, dubbed DoubleDirect, enables an attacker to redirect a victim’s traffic of major websites such as Google, Facebook and Twitter to a device controlled by the attacker. Once done, cyber crooks can steal victims’ valuable personal data, such as email IDs, login credentials and banking information as well as can deliver malware to the targeted mobile device.
San Francisco-based mobile security firm Zimperium detailed the threat in a Thursday blog post, revealing that the DoubleDirect technique is being used by attackers in the wild in attacks against the users of web giants including Google, Facebook, Hotmail, Live.com and Twitter, across 31 countries, including the U.S., the U.K. and Canada.
Via Gust MEES
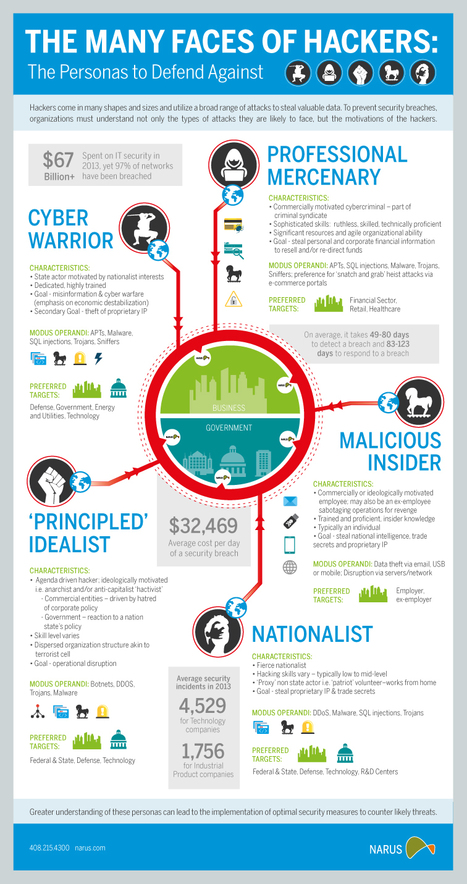
How many of these hacker personas are you dueling with in your organization?
Via Gust MEES
Des chercheurs américains ont développé une méthode d’analyse inédite pour protéger les objets connectés des failles de sécurité.
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...





























A major security flaw in Dell’s firmware updating and operating recovery software, BIOSConnect, potentially exposes tens of millions of devices that Dell preinstalled it on.
BleepingComputer reported on Thursday that researchers with security firm Eclypsium discovered a flaw in BIOSConnect, which is part of Dell’s standard SupportAssist software and updates the firmware on a computer’s system board, that could allow attackers to remotely execute malicious code. In a report, the researchers wrote that the vulnerability was so severe it could “enable adversaries to control the device’s boot process and subvert the operating system and higher-layer security controls,” which would give them control “over the most privileged code on the device.”
There are four separate vulnerabilities, one of which involves insecure connections between a BIOS being updated and Dell’s servers that allow an attacker to redirect the machine to a maliciously modified update package. The remaining three are classified as overflow vulnerabilities. Eclypsium rated the bugs as severe security threats.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet