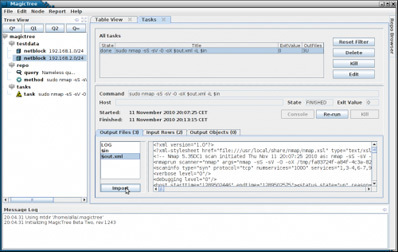
Have you ever spent ages trying to find the results of a particular portscan you were sure you did? Or grepping through a bunch of files looking for data for a particular host or service? Or copy-pasting bits of output from a bunch of typescripts into a report?
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
A collection of best ICT Security Tools + tutorials how to use them...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|
|