Your new post is loading...
 Your new post is loading...
What is professional development? It is pretty much anything that helps one develop professionally. At the heart, professional development is about growth and learning. In the field of education, it seems like many quickly think of educational opportunities that mimic what they see in their schools. As a result, they turn professional learning and education into schooling. The problem with that is that schooling is too limiting. In this age, there are many other exciting and high-impact learning opportunities for teachers that extend beyond traditional notions of schooling. When we hear the phrase “professional development,” certain practices likely come to mind, things like in-services and conferences. In the digital age, there are countless other opportunities for professional development and restricting one’s thoughts to just a few options limits our insight into what is possible for our students. With that in mind, here is a brainstorm of 20 options available to educators today. This is far from an exhaustive list, but it is enough to start exploring the possibilities. Feel free to suggest others in a comment to this post. Learn more: Professional Development: WHY EDUcators And TEACHers Can’t Catch UP THAT Quickly AND How-To Change It LEARNing To LEARN For MY Professional Development | I Did It MY Way
Via Gust MEES, John Evans
Des pirates s’appuient sur des fausses pubs pour diffuser à des millions d'internautes un malware particulièrement sophistiqué, qui s’appuie sur de multiples techniques de dissimulation. Voilà encore une preuve que les cybercriminels deviennent de plus en plus malins. Les chercheurs en sécurité d'Eset viennent de mettre la main sur un malware qui exploite des failles dans Internet Explorer et Flash Player, et dont le code est caché directement dans les pixels d'une image de publicité. C’est pourquoi il a été baptisé « Stegano », en référence à la stéganographie, l’art de dissimuler des messages secrets dans des choses en apparence anodines, comme ici une pub en ligne. L’impact de ce malware, en revanche, est loin d’être anodin. Selon Eset, la publicité vérolée a été diffusée entre autres sur des sites d’actualités très populaires, lui permettant d’être affichée par « plus d’un million d’internautes », explique Robert Lipovsky, l’un des chercheurs d’Eset, dans une note de blog. L’attaque se déroule de façon totalement automatique, la victime n’a pas même pas besoin de cliquer sur la publicité. D’après les chercheurs, Stegano a été utilisé par les cybercriminels pour installer sur les machines des victimes des chevaux de Trois bancaires, des portes dérobées et des logiciels espions. Mais en théorie, il n’y a pas vraiment de limite. « Les victimes pourraient également être confrontées à de méchantes attaques de ransomware », souligne Robert Lipovsky. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Steganography
Via Gust MEES
The tech world, Burger explained, was moving into a new orbit. In the future, a few giant Internet companies would operate a few giant Internet services so complex and so different from what came before that these companies would have to build a whole new architecture to run them. They would create not just the software driving these services, but the hardware, including servers and networking gear. Project Catapult would equip all of Microsoft’s servers—millions of them—with specialized chips that the company could reprogram for particular tasks.
Via Gust MEES
In response to the disclosure of vulnerabilities in Tor's design, researchers at MIT have created Riffle, a system that allegedly provides better security and uses bandwidth more efficiently.
Via Gust MEES
Some U.S. government agencies are using IT systems running Windows 3.1, the decades-old COBOL and Fortran programming languages, or computers from the 1970s.
A backup nuclear control messaging system at the U.S. Department of Defense runs on an IBM Series 1 computer, first introduced in 1976, and uses eight-inch floppy disks, while the Internal Revenue Service's master file of taxpayer data is written in assembly language code that's more than five decades old, according to a new report from the Government Accountability Office.
Some agencies are still running Windows 3.1, first released in 1992, as well as the newer but unsupported Windows XP, Representative Jason Chaffetz, a Utah Republican, noted during a Wednesday hearing on outdated government IT systems.
The government is spending more than US$80 billion a year on IT, and "it largely doesn't work," Chaffetz said during a House of Representatives Oversight and Government Reform Committee hearing. "The federal government is years, and sometimes decades, behind the private sector."
Via Gust MEES
Cryptolunch.lu, la cybersécurité à la portée des citoyens
Cryptolunch.lu est un évènement gratuit, organisé au Luxembourg, dédié à l'information des citoyens européens à la protection de la vie privée et la sécurité en ligne.
L'utilisation massive des Technologies de l'Information et de l'Information a fait évoluer les limites entre vie privée et vie publique. Alors que nous sommes toujours plus connectés, une masse exponentielle de données personnelles nous concernant est échangée, tant en ligne que hors ligne. La vie privée est pourtant un droit qu'il est important de défendre.
Organisé en partenariat entre la maison de l'Europe et Securitymadein.lu, la finalité des cryptolunch est de mettre à disposition un lieu de rencontre où les citoyens européens auront l'opportunité de s'entretenir avec des experts en sécurité afin d'obtenir des informations sur des sujets tels que la vie privée et la sécurité numérique.
Créé afin de permettre à un public non spécialisé d'obtenir des réponses claires et simples à ses questions, ce rassemblement est idéal pour répondre aux attentes de profils très variées en termes de sécurité sur Internet. Learn more: http://www.scoop.it/t/securite-pc-et-internet/?tag=ENCRYPTION
Via Gust MEES
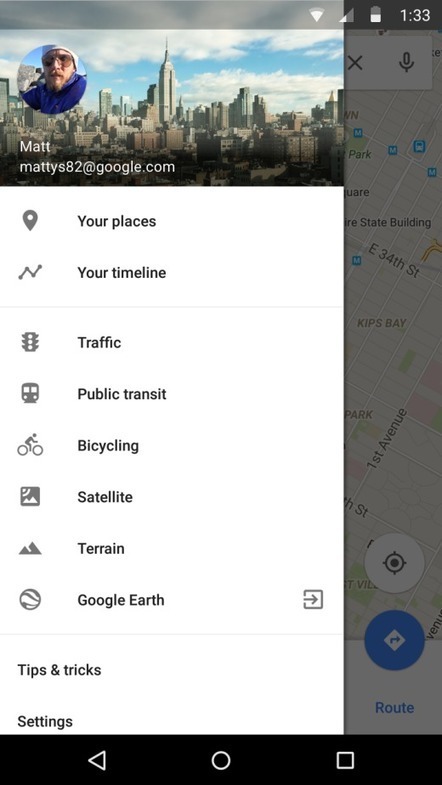
It’s inspiring — in a crazy sort of way — to consider how efficient Google can be in keeping track of information about you. Today, Google announced the launch of “Your Timeline,” a tool in Google Maps that shares with you all the places you have been. It works if you chose to store your Location History with Google.
Product manager Gerard Sanz detailed the feature in blog post, as the company gradually rolls out the timeline for Maps users.
It could definitely serve as a convenience. What with our busy lives, sometimes it’s hard to remember all the stops along the way. Google sees Your Timeline as a way to quickly recall, and even view your past whereabouts.
Via Gust MEES
The Internet has become a major part of most people’s days and nights. It’s often the thing people check first thing in the morning, and the thing people do last with their smartphones before bedtime.
Via Gust MEES
|
Russian hackers are stealing between $3 million to $5 million per day from US brands and media companies in one of the most lucrative botnet operations ever discovered.
On December 20, researchers from White Ops said the scheme, dubbed "Methbot," is a Russian operation set up to watch up to 300 million video-based adverts automatically every day.
These adverts, displayed on legitimate domains owned by companies including the Huffington Post, Economist, Fortune, ESPN, Vogue, CBS Sports, and Fox News, are used to generate additional revenue through advertising sponsors which help keep these businesses afloat.
However, White Ops says Methbot capitalizes on this revenue generation by targeting the most expensive advertising on the web -- such as full-blown video adverts on branded websites -- and is programmed to show signs of "engagement" to fool ad providers into thinking the content is being watched legitimately.
Faked clicks, mouse movements, social network login information, and typical "working hours" are all methods to keep the operation under wraps. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=cybercrime
Via Gust MEES
The web design platform Weebly was hacked in February, according to the data breach notification site LeakedSource. Usernames and passwords for more than 43 million accounts were taken in the breach, although the passwords are secured with the strong hashing algorithm bcrypt.
Weebly said in an email to customers that user IP addresses were also taken in the breach.
“We do not believe that any customer website has been improperly accessed,” Weebly said in the notice to users.” The company also said that it does not store credit card information, making fraudulent charges unlikely.
LeakedSource said it received the Weebly database from an anonymous source and notified Weebly of the breach. In addition to the customer notification emails, LeakedSource claims that password resets are being issued — but, if you’re a Weebly user and you don’t receive a password reset, you probably want to change your password anyway. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=DATA-BREACHES
Via Gust MEES
What is professional development? It is pretty much anything that helps one develop professionally. At the heart, professional development is about growth and learning. In the field of education, it seems like many quickly think of educational opportunities that mimic what they see in their schools. As a result, they turn professional learning and education into schooling. The problem with that is that schooling is too limiting. In this age, there are many other exciting and high-impact learning opportunities for teachers that extend beyond traditional notions of schooling. When we hear the phrase “professional development,” certain practices likely come to mind, things like in-services and conferences. In the digital age, there are countless other opportunities for professional development and restricting one’s thoughts to just a few options limits our insight into what is possible for our students. With that in mind, here is a brainstorm of 20 options available to educators today. This is far from an exhaustive list, but it is enough to start exploring the possibilities. Feel free to suggest others in a comment to this post. Learn more: Professional Development: WHY EDUcators And TEACHers Can’t Catch UP THAT Quickly AND How-To Change It LEARNing To LEARN For MY Professional Development | I Did It MY Way
Via Gust MEES
If your organisation does business within the European Union or collects data on European citizens you’ve likely been told about the newly approved EU General Data Protection Regulation (GDPR), which will come into force in spring 2018.
The GDPR will increase privacy for individuals and give regulatory authorities greater powers to take action against businesses that breach the law.
Are you prepared to take the steps necessary for compliance? Here’s a brief overview of everything you need to know about the new Regulation and what it means for your business. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/
Via Gust MEES
|



 Your new post is loading...
Your new post is loading...















![Where In the World Is the Internet? [Infographic] | information analyst | Scoop.it](https://img.scoop.it/Dgz2raLDEIdG3-9USccJOjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)