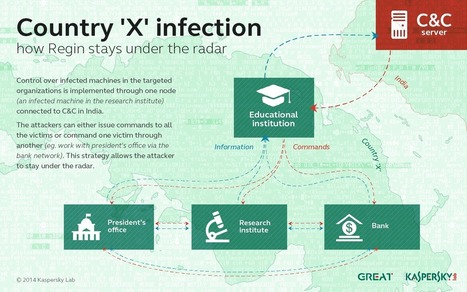
A sophisticated group known as Regin has targeted high-profile entities around the world. Regin is one of the most sophisticated attack platforms we have ever analysed. The ability to penetrate and...
For more than a decade, a sophisticated group known as Regin has targeted high-profile entities around the world with an advanced malware platform. As far as we can tell, the operation is still active, although the malware may have been upgraded to more sophisticated versions. The most recent sample we've seen was from a 64-bit infection. This infection was still active in the spring of 2014.
The name Regin is apparently a reversed "In Reg", short for "In Registry", as the malware can store its modules in the registry. This name and detections first appeared in anti-malware products around March 2011.
From some points of view, the platform reminds us of another sophisticated malware: Turla. Some similarities include the use of virtual file systems and the deployment of communication drones to bridge networks together. Yet through their implementation, coding methods, plugins, hiding techniques and flexibility, Regin surpasses Turla as one of the most sophisticated attack platforms we have ever analysed.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=REGIN
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Warriorpride
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Quantum
- http://www.scoop.it/t/securite-pc-et-internet/?tag=cyberwar
- http://www.scoop.it/t/securite-pc-et-internet/?tag=NSA
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TAO
- https://gustmees.wordpress.com/2012/05/21/visual-it-securitypart2-your-computer-as-a-possible-cyber-weapon/



 Your new post is loading...
Your new post is loading...








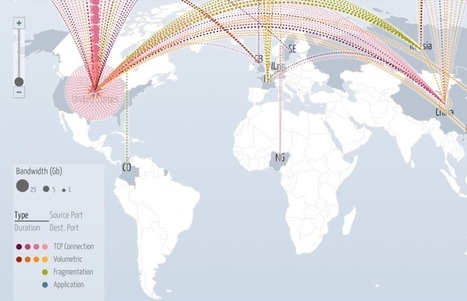











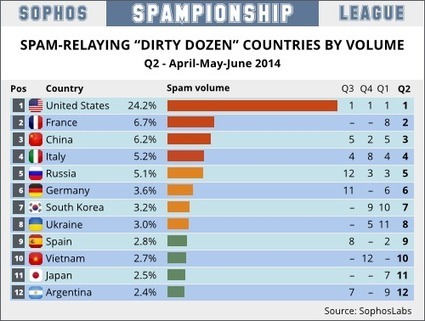
![China Is The World's Top Source Of Internet Attack Traffic [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/kL-Wk5gX_zZn5UwtR_HnNTl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)







Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress