 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
According to security researchers, a new IoT botnet has quietly hijacked more than 100,000 routers, readying them for paralysing distributed denial-of-service attacks against websites.
The botnet, which some researchers have dubbed “Satori” (a name given to supernatural mind-reading monsters in Japanese folklore), has increased its activity in recent days – propagating very quickly via a zero-day remote code execution vulnerability in Huawei Home Gateway or Huawei’s Echolife Home Gateway devices, and an already documented vulnerability in Realtek routers.
The exploitation of vulnerabilities allows the botnet to infect routers even when they have been secured with strong passwords.
Through the attack, an army of hundreds of thousands of routers are thought to have been commandeered into the botnet. Some commentators have even suggested that over 280,000 IP addresses have been compromised by the attack in just 12 hours.
Like the Reaper IoT botnet before it, Satori is built on the foundations of the notorious Mirai botnet which knocked major websites offline last year, and whose source code was released onto the internet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Satori+botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
INTERNET OF THINGS:
Bricker Bot soll 2 Millionen IoT-Geräte zerstört haben
Wie weit darf der Kampf gegen unsichere IoT-Geräte gehen? Diese Frage wird spätestens seit Aufkommen der Bricker-Bot-Software diskutiert. Der mutmaßliche Entwickler sagt: Ich habe 2 Millionen unsichere Geräte aus dem Netz entfernt.
Der Kampf gegen unsichere IoT-Geräte im Netz geht weiter: Sicherheitsforscher haben in den vergangenen Tagen erneut Aktivitäten des sogenannten Bricker Bots beobachtet - eine umstrittene Software, die unsicher konfigurierte Internet-of-Things-Geräte im Netz aufspürt und unschädlich machen soll, damit diese nicht in Botnetzen wie Mirai eingesetzt werden können.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Amnesia&tag=BrickerBot

|
Scooped by
Gust MEES
|
Hacker zerstören das Internet of Insecure Things
Unbekannte versuchen zurzeit, sich in ungesicherte IoT-Geräte zu hacken und diese aktiv zu zerstören. Offenbar ein Versuch, die Geräte unschädlich zu machen, bevor sie Teil von Botnetzen wie Mirai werden.
Die IT-Sicherheitsfirma Radware hat auf ihren Honeypots einige bemerkenswerte Angriffsversuche beobachtet. Mit Hilfe von bekannten Standardpasswörtern versuchen die Angreifer, sich per SSH in ungesicherte Geräte einzuloggen. Anschließend führen sie verschiedene Kommandos aus, die dazu führen, dass die entsprechenden Geräte nicht mehr funktionieren. Die Vermutung:
Hier versucht jemand, das Internet of Things von unsicheren Geräten zu befreien. Radware taufte die Angriffe, die in zwei Wellen erfolgten, BrickerBot.1 und BrickerBot.2. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Amnesia&tag=BrickerBot

|
Scooped by
Gust MEES
|
Researchers have uncovered a rash of ongoing attacks designed to damage routers and other Internet-connected appliances so badly that they become effectively inoperable.
PDoS attack bots (short for "permanent denial-of-service") scan the Internet for Linux-based routers, bridges, or similar Internet-connected devices that require only factory-default passwords to grant remote administrator access. Once the bots find a vulnerable target, they run a series of highly debilitating commands that wipe all the files stored on the device, corrupt the device's storage, and sever its Internet connection. Given the cost and time required to repair the damage, the device is effectively destroyed, or bricked, from the perspective of the typical consumer.
Over a four-day span last month, researchers from security firm Radware detected roughly 2,250 PDoS attempts on devices they made available in a specially constructed honeypot. The attacks came from two separate botnets—dubbed BrickerBot.1 and BrickerBot.2—with nodes for the first located all around the world. BrickerBot.1 eventually went silent, but even now the more destructive BrickerBot.2 attempts a log-on to one of the Radware-operated honeypot devices roughly once every two hours. The bots brick real-world devices that have the telnet protocol enabled and are protected by default passwords, with no clear sign to the owner of what happened or why. Learn more / En savoir plus / Mehr erfahren:

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Mirai n’a pas dit son dernier mot. Les éditeurs d’antivirus Dr Web et Kaspersky communiquent ainsi sur une nouvelle version du fameux malware, visant cette fois-ci des machines sous Windows. Dr. Web a été le premier à tirer la sonnette d’alarme au début du mois de février, suivi de près par Kaspersky.
Baptisé trojan.mirai1 par Dr Web, ce malware infecte les machines sous Windows en utilisant des vecteurs classiques, type pièce jointe malveillante ou macro Office. Une fois la machine infectée par le trojan, celui-ci va scanner le réseau local à la recherche d’objets connectés fonctionnant sous Linux. Puis il va utiliser ceux-ci afin de les infecter avec une variante de Mirai, et ceux-ci seront ajoutés au botnet des cybercriminels qui peuvent alors les utiliser pour lancer des attaques DDoS. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|
The Trojan tries to authenticate over different protocols with factory default credentials and, if successful, deploys the Mirai bot. Attackers have started to use Windows and Android malware to hack into embedded devices, dispelling the widely held belief that if such devices are not directly exposed to the Internet they're less vulnerable. This new Trojan found by Doctor Web, dubbed Trojan.Mirai.1, shows that attackers can also use compromised computers to target IoT devices that are not directly accessible from the internet. Infected smartphones can be used in a similar way. Researchers from Kaspersky Lab have already found an Android app designed to perform brute-force password guessing attacks against routers over the local network.

|
Scooped by
Gust MEES
|
Am Tag nach dem mutmaßlichen Anschlag auf einen Berliner Weihnachtsmarkt ist das Hinweisportal des Bundeskriminalamts mehr als zwei Stunden durch einen DDoS-Angriff lahmgelegt worden. Inzwischen ist es wieder erreichbar. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=BKA
|

|
Scooped by
Gust MEES
|
Hacker groups in Asia have weaponized the networking and pentesting tools in a series of attacks first identified in March 2018, as well as the high-profile SingHealth attack.
Hackers are leveraging Termite and EarthWorm, packet relay tools written by an employee of Beijing-based security research firm 360Netlab, to create a botnet of Internet of Things (IoT) devices, according to a report by AT&T Cybersecurity (formerly AlienVault).
Termite is capable of functioning as a SOCKS proxy, as well as a simple backdoor for file transfer and executing shell commands. Termite is capable of running on a wide variety of architectures, including x86, x86-64, ARM, MIPS(EL), SH-4, PowerPC, SPARC, and M68k, making it a particularly versatile tool for attackers to deploy on low-power IoT devices. Likewise, the small size (200-600 KB) makes it ideal for deployment on these devices, which often have meager internal storage.
Weaponization of these, which were intended as networking and penetration testing utilities, is a recent phenomenon. Kaspersky Lab noted briefly last year that Earthworm, the predecessor to Termite, was used as part of an attack involving the theft of a driver signing certificate of a Chinese IT company. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Botnet

|
Scooped by
Gust MEES
|
Why go to all the bother of writing ransomware that demands victims pay a Bitcoin ransom? If all you want is cryptocurrency, why not use the infected computers to mine the crypto coins themselves?
That way you don’t have to rely on a human victim buying some Bitcoin, and nervously making their way onto the dark web to make their ransom payment.
According to security researchers at Proofpoint, that’s exactly the reasoning shown by online criminals who are moving from regular ransomware to cryptomining.
A Monero-mining botnet called Smominru is said to have infected 526,000 Windows PCs since May 2017 – mostly in Russia, India, and Taiwan – and is earning millions of dollars for its operators. In fact, the biggest clue that most users will have that their computers may be affected by a cryptominer is if they found the PC is slowing down, its battery running out at a quicker rate, or the fan blowing at full blast. Don’t make the mistake of thinking that this is a victimless crime. If your computers get recruited into a cryptomining botnet like Smominru, it’s your electricity and computer power that is being stolen. Keep your computers up-to-date with security patches, defended with layered security solutions, and your wits about you. Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
A new massive IoT (Internet of Things) botnet dubbed Satori has emerged, which security researchers fear, can launch crippling attacks at any time. The botnet has reportedly already infected over 280,000 IP addresses in just 12 hours, enslaving hundreds of thousands of home routers by exploiting a recently discovered zero-day vulnerability.
Satori, which reportedly means "awakening" in Japanese, is actually the infamous Mirai botnet's successor. Since Mirai's authors made the botnet's source code public last year, cybercriminals have been pushing out new variants of Mirai. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A cryptocurrency-mining malware began exploiting a leaked NSA vulnerability several weeks before WannaCry sank its teeth into it.
The researchers expected to see the ransom message above when they looked at a lab machine vulnerable to EternalBlue. Instead they found a subtler threat: Adylkuzz. This malware relies on virtual private servers scanning the Internet on TCP port 445 for distribution. If infection proves successful, it enlists victims in a cryptocurrency-mining botnet. But Adylkuzz isn't interested in sharing an affected computer that's capable of communicating over Microsoft's Microsoft Server Message Block (SMB). Security researcher Kafeine elaborates on that point: "Upon successful exploitation via EternalBlue, machines are infected with DoublePulsar. The DoublePulsar backdoor then downloads and runs Adylkuzz from another host. Once running, Adylkuzz will first stop any potential instances of itself already running and block SMB communication to avoid further infection. It then determines the public IP address of the victim and download the mining instructions, cryptominer, and cleanup tools."
In that sense, Adylkuzz blocks other threats like WannaCry from leveraging ExternalBlue to infect vulnerable computers. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Adylkuzz http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=Phishing http://www.scoop.it/t/securite-pc-et-internet/?&tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
In its 2017 malware forecast, SophosLabs warned that attackers would increasingly target devices connected to the Internet of Things (IoT) – everything from webcams to internet-connecting household appliances. Late last week, we saw another example of how the trend is playing out.
Security vendor Radware warned that malware called BrickerBot is in the wild, designed to brick IoT devices by damaging their storage capability and scrambling kernel parameters. The company detected two versions of the malware in its honeypot servers – BrickerBot.1 and BrickerBot.2. The first attacks were detected March 20, targeting Linux-based IoT devices running the BusyBox toolkit. The honeypot recorded 1,895 PDoS (Permanent Denial of Service) attempts by BrickerBot from several locations around the world over four days.
To block the attack, Radware recommended users:
Change the device’s factory default credentials.
Disable Telnet access to the device.
Network Behavioral Analysis can detect anomalies in traffic and combine with automatic signature generation for protection.
User/Entity behavioral analysis (UEBA) to spot granular anomalies in traffic early.
An IPS should block Telnet default credentials or reset telnet connections. Use a signature to detect the provided command sequences. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Internet+of+things

|
Scooped by
Gust MEES
|
Malware Amnesia bildet IoT/Linux-Botnet
Die Schadsoftware erkennt und löscht virtuelle Maschinen, um Entdeckung und Analyse durch Sicherheitsforscher zu vermeiden. Zuerst entdeckt wurde sie auf digitalen Videorekordern. Sicherheitsforscher befürchten ähnlich umfangreiche DDoS-Attacken wie durch Mirai-Botnets.
von Bernd Kling am 7. April 2017 , 18:14 Uhr
Die Malware Amnesia setzt eine neue Technik ein, um einer Entdeckung zu entgehen. Die Sicherheitsfirma Palo Alto Networks sieht sie als erste Linux-Malware, die virtuelle Maschinen erkennen und löschen kann. Das soll sich gegen von Sicherheitsforschern eingerichtete Sandboxes mit Analysewerkzeugen richten. Die Malware löscht sich außerdem selbst, um keine weiteren Spuren zu hinterlassen.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Amnesia http://www.scoop.it/t/securite-pc-et-internet/?&tag=Amnesia&tag=BrickerBot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...

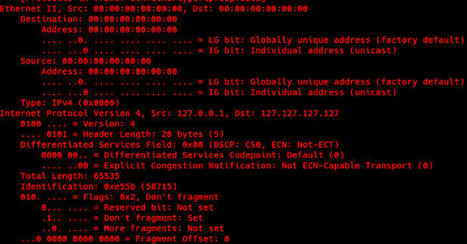










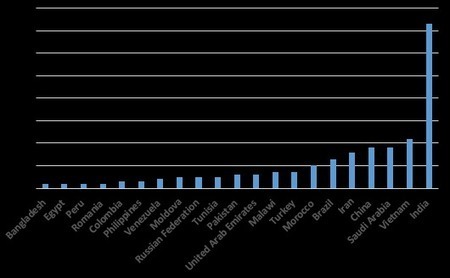




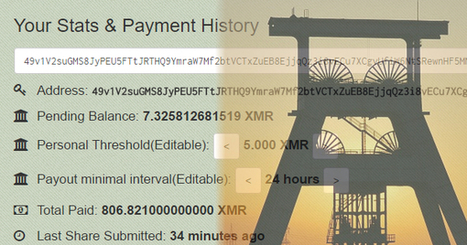











A new Golang-based botnet dubbed HinataBot has been observed to leverage known flaws to compromise routers and servers and use them to stage distributed denial-of-service (DDoS) attacks.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet