 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Data breaches are always bad news, and this one is peculiarly bad.
Gentoo, a popular distribution of Linux, has had its GitHub repository hacked.
Hacked, as in “totally pwned”, taken over, and modified; so far, no one seems to be sure quite how or why.
That’s the bad news.
Fortunately (we like to find silver linings here at Naked Security):
The Gentoo team didn’t beat around the bush, and quickly published an unequivocal statement about the breach.
The Gentoo GitHub repository is only a secondary copy of the main Gentoo source code.
The main Gentoo repository is intact.
All changes in the main Gentoo repository are digitally signed and can therefore be verified.
As far as we know, the main Gentoo signing key is safe, so the digital signatures are reliable.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Over a million fiber routers can be remotely accessed, thanks to an authentication bypass bug that's easily exploited by modifying the URL in the browser's address bar.
The bug lets anyone bypass the router's login page and access pages within -- simply by adding "?images/" to the end of the web address on any of the router's configuration pages, giving an attacker near complete access to the router. Because the ping and traceroute commands on the device's diagnostic page are running at "root" level, other commands can be remotely run on the device, too.
The findings, published Monday, say the bug is found in routers used for fiber connections. These routers are central in bringing high-speed fiber internet to people's homes.
At the time of writing, about 1.06 million routers marked were listed on Shodan, the search engine for unprotected devices and databases. Half the vulnerable routers are located on the Telmex network in Mexico, and the rest are found on in Kazakhstan and Vietnam. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Router

|
Scooped by
Gust MEES
|
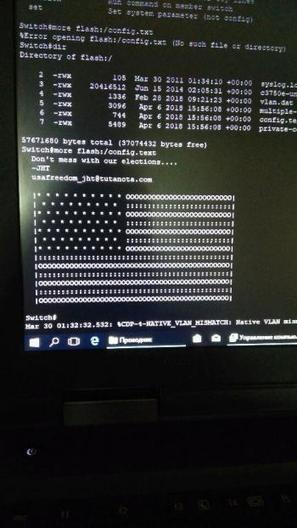
Unbekannte haben eine Sicherheitslücke in Cisco-Routern ausgenutzt und auf Systemen in Russland und Iran eine politische Botschaft hinterlassen. In westlichen Ländern hingegen schlossen sie die Lücke - behauptet zumindest eine anonyme E-Mail.
Hacker mit Sympathie für die USA nehmen für sich in Anspruch, am vergangenen Freitag zahlreiche Computersysteme in Russland und dem Iran über eine Sicherheitslücke gekapert und eine Abbildung der amerikanischen Flagge hinterlassen zu haben – zusammen mit dem Warnhinweis: "Don't mess with our elections..." (zu deutsch etwa: Mischt euch nicht in unsere Wahlen ein). Das meldet das Online-Magazin Motherboard.
"Don't mess with our elections..." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The average home now has around three connected computers and four smart mobile devices. Hardly surprising, considering that 86 per cent of us check the Internet several times a day or more, and that’s outside of work. Chatting, shopping, banking, playing games, listening to music, booking travel and managing our increasingly connected homes. The risk of cyberattack can be the furthest thing from our mind. Every year, Kaspersky Lab’s experts look at the main cyberthreats facing connected businesses over the coming 12 months, based on the trends seen during the year. For 2018, we decided to extract some top predictions that also have big implications for everyday connected life. So what could the hackers be after in 2018? Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Luxembourg, a tiny country with ONLY 590.667 inhabitants (January 2017) in the heart of Europe and one of the smallest countries in the world, WHERE MOST persons don’t even know where to find it on the map, shows up as an international country well known and recognized for its Cyber Security knowledge, as well as its skills in ICT. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/luxembourg-europe/?tag=Digital+L%C3%ABtzebuerg

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Twitter’s been combatting harassment for years. The latest effort: quelling its horde of anonymous, hostile egg accounts. But for many users, Twitter’s abuse problem has long since undermined its value as a platform for creative communication. That’s what makes Mastodon—a free, open-source, and increasingly popular six-month-old Twitter alternative—so intriguing.
Mastodon has created a diverse yet welcoming online environment by doing exactly what Twitter won’t: letting its community make the rules. The platform consists of various user-created networks, called instances, each of which determines its own laws. One instance could ban sexist jokes and Nazi logos, while another might practice radically free speech. (In this way, Mastodon is not unlike a network of discretely moderated message boards crossed with a Tweetdeck-like interface.) Users choose for themselves which instance they want to join and select from a host of privacy and anti-harassment settings. Oh, and the character limit is 500, not 140. In essence, Mastodon is an experiment in whether individually moderated communities can make a social network like Twitter more civil. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/social-media-and-its-influence/?&tag=Mastodon

|
Scooped by
Gust MEES
|
Neue Funktionen für Android und iOS von Kaspersky Safe Kids vereinfachen Cybererziehung
Kinder können blockierte Seiten und Apps von Eltern freigeben lassen; Eltern werden mit Tipps von Psychologen unterstützt
Moskau/lngolstadt, 1. Dezember 2016 - Kaspersky Lab baut seine Cyberschutzlösung Kaspersky Safe Kids [1] mit neuen Funktionen für iOS- und Android-Geräte aus. Ab sofort können Kinder ihre Eltern mobil und mit einem Klick um Zugang zu eigentlich für sie gesperrte Webseiten oder Apps anfragen. Eltern hingegen werden über Kaspersky Safe Kids mit praxisnahen Ratschlägen von Psychologen bei der Cybererziehung unterstützt.
Eine internationale Studie von Kaspersky Lab [2] zeigt, dass ein Drittel der befragten Eltern keinen Überblick über die Internetnutzung ihrer Kinder hat. . Um die Internetnutzung für den Nachwuchs sicherer zu machen, stehen Eltern technische Schutzmöglichkeiten zur Verfügung. Darüber hinaus kommt es aber insbesondere auf den Dialog mit den Kindern an [3].
Kaspersky Safe Kids integriert daher ab sofort Ratschläge von Psychologen, die Eltern zum direkten Abruf auf dem eigenen Gerät zur Verfügung stehen.
Eltern bekommen so fachgerechte Tipps mit Handlungsempfehlungen im Falle des Zugriffs der Kinder auf unpassende Webseiten und Apps, neuer (vielleicht unerwünschter) Online-Bekanntschaften, getätigter Online-Einkäufe oder exzessiver Internetnutzung ihrer Kids – in einer einfachen und übersichtlichen Oberfläche für Eltern und Kind [4].

|
Scooped by
Gust MEES
|
Who Will Own Your Data If the Tech Bubble Bursts?
Corporations, data brokers, and even criminals might buy failed companies just for their users’ personal information. Desperate companies will resort, if they can, to selling the detailed data they’ve meticulously collected about their users—whether it’s personally identifiable information, data about preferences, habits, and hobbies, or national-security files. That data, formerly walled-off and spoon-fed only to paying advertisers, would be attractive to both licit and criminal buyers. Easily searchable datasets could generate new innovations and investments—but it would be difficult to know who’s buying up sensitive datasets, and why. If contracts and privacy policies prevent a floundering company from selling user data, there’s still another way to profit. Most privacy policies that promise not to sell user data include a caveat in case of bankruptcy or sale. In fact, a New York Times analysis of the top 100 websites in the U.S. last year found that 85 of them include clauses in their privacy policies like this one from Facebook: If the ownership or control of all or part of our Services or their assets changes, we may transfer your information to the new owner.
Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Password Day is a day for "taking our passwords to the next level" - here are five traditions the crooks really don't want us to start.

|
Scooped by
Gust MEES
|
Yup, I get it: The cloud computing train has left the station and there’s no stopping it now, but it certainly won’t reach Eurostar speeds if there aren’t enough cybersecurity professionals with the right cloud computing knowledge to support this transition.
Given this imbalance, what can CISOs do to support cloud computing business initiatives AND mitigate risk appropriately? Learn more /En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Cloud-Security
|

|
Scooped by
Gust MEES
|
Hacker erlangen Zugriff auf Gentoo-Code in Github
Der Quellcode der Linux-Distribution Gentoo könnte kompromittiert sein: Das Entwicklerteam berichtet von einem Hack der gesamten Github-Organisation, in der Repositories abgelegt sind. Davon unberührt sein sollen die Backup-Dateien, die das Team auf eigener Infrastruktur hostet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
A new form of cryptocurrency mining malware uses a leaked NSA-exploit to spread itself to vulnerable Windows machines, while also disabling security software and leaving the infected computer open to future attacks.
The Python-based malicious Monero miner has been uncovered by researchers at security company Fortinet who've dubbed it PyRoMine. It first appeared this month and spreads using EternalRomance, a leaked NSA-exploit which takes advantage of what until a year ago had been an undisclosed SMB vulnerability to self-propagate through networks.
EternalRomance helped spread BadRabbit ransomware and is similar in many ways to EternalBlue, a second leaked NSA exploit which helped fuel WannaCry and NotPetya. Both exploits look for public-facing SMB ports, allowing them to deliver malware to networks.
Researchers discovered the malware was downloadable from a particular web address as a zip file, bundled with Pyinstaller, a program which packages programs written in Python into stand alone executables, meaning there's no need for Python to be installed on the compromised machine.
The malicious code behind PyRoMine appears to have been directly copied from a publicly shared EternalRomance implementation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency

|
Scooped by
Gust MEES
|
Around 20% of today's top VPN solutions are leaking the customer's IP address via a WebRTC bug known since January 2015, and which apparently some VPN providers have never heard of.
The discovery belongs to Paolo Stagno, a security researcher who goes by the pseudonym of VoidSec, and who recently audited 83 VPN apps on this old WebRTC IP leak.
Stagno says he found that 17 VPN clients were leaking the user's IP address while surfing the web via a browser.
The researcher published his results in a Google Docs spreadsheet. The audit list is incomplete because Stagno didn't have the financial resources to test all commercial VPN clients.
The researcher is now asking the community to test their own VPN clients and send him the results. For this, he set up a demo web page that users must access in their browser with their VPN client enabled. The code running on this page is also available on GitHub, if users want to test the leak locally, without exposing their IP on somebody else's server.
WebRTC leak known since 2015
Stagno's code is based on the WebRTC bug discovered in January 2015 by security researcher Daniel Roesler. Back then, Roesler found that WebRTC STUN servers, which intermediate WebRTC connections, will keep records of the user's public IP address, along with his private IP address, if the client is behind-NAT network, proxy, or VPN client.
The problem was that STUN servers would disclose this information to websites that had already negotiated an WebRTC connection with a user's browser.
Since then, many advertisers and law enforcement agencies have used this WebRTC-related bug to acquire a site's visitor's IP address. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|
Dès mai prochain, les données personnelles seront mieux protégées en Europe. L'occasion pour de nombreux services de commencer à se poser des questions sur leurs pratiques. Mais comment informer l'internaute sur la réalité des choses ? Nous avons décidé de lancer la réflexion.
Il y a un peu plus de deux ans, nous nous posions une question : et si on dépolluait Internet ? Nous notions en effet depuis plusieurs années que les sites devenaient de plus en plus impraticables du fait d'abus publicitaires et de méthodes douteuses comme la lecture automatique des vidéos ou l'auto-refresh.
Mais cette gêne visuelle en cachait une autre : la collecte massive de données, mise en place à travers les services des géants du Net (Analytics, boutons J'aime, etc.) et d'espaces publicitaires toujours plus automatisés.
Quel avenir voulons-nous pour Internet ?
On le voit aujourd'hui, chaque site peut déposer des dizaines de cookies sans le moindre consentement de l'utilisateur, le tout à travers une centaine de domaines tiers. Pour le vérifier, il n'y a qu'à utiliser des outils comme Kimetrak et regarder les données du navigateur (voir notre dossier).
Ainsi, comme on pouvait le craindre, l'Internet que l'on connaissait il y a 20 ans s'est profondément modifié sur trois points principaux : les plateformes y ont progressivement pris le pouvoir, il y est plus souvent question de commerce que de partage libre des informations et des idées, le tout alimenté par une immense collecte de données personnelles.
Comme c'est le cas dans certaines industries, il existe néanmoins des zones de « résistance ». L'information s'y veut en libre accès, elle doit permettre au plus grand nombre de réfléchir au monde d'aujourd'hui plutôt que suivre les derniers buzz, l'entraide et le travail collaboratif y sont des valeurs centrales et le financement se fait à travers des dons ou des abonnements, l'accès aux données n'étant pas considéré comme un « pétrole à exploiter ».
Malheureusement il n'existe pas vraiment d'élément distinctif fort pour ces sites et services, qui constituent une alternative au tout commercial qui nous entoure désormais dans le World Wide Web.
Un label pour l'Internet propre ?
Faudrait-il créer une sorte d'annuaire ? De label « bio » des services et autres sites en ligne ? Sans doute. Tout du moins faciliter l'accès et la reconnaissance de ces initiatives en fonction d'éléments qui peuvent être facilement vérifiés : structure économique, modèle de financement, trackers, dispositions légales à travers des outils tels que ToS;DR, etc. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/luxembourg-europe/?&tag=GDPR

|
Scooped by
Gust MEES
|
Des dizaines de sociétés s’insèrent dans des applications banales pour collecter des données, amassant des informations sur des millions de Français.
Par dizaines, ils se nichent dans des applications mobiles utilisées quotidiennement par des millions de Français. Ils capturent discrètement des données, souvent personnelles, sans que les utilisateurs n’en soient nécessairement conscients, alimentant au passage une industrie opaque et méconnue. Certains de ses acteurs disposent de données sur des millions de Français.
Il s’agit de trackers, de petits logiciels incorporés dans des applications mobiles du quotidien (réseaux sociaux, médias, banques, sites de rencontre). Chaque application en compte 2,5 en moyenne, selon une analyse de plus de 350 applications, réalisée par un groupe d’activistes, rassemblés depuis octobre en association, et publiée vendredi 24 novembre sur leur plate-forme baptisée Exodus. Rares sont les applications qui en sont dépourvues et certaines vont jusqu’à en intégrer une quinzaine. Ce paysage n’est pas exhaustif : la plate-forme ne cherche que les trackers qu’elle a préalablement identifiés, soit une quarantaine. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking

|
Scooped by
Gust MEES
|
Gefahren im Internet sind für Anwender und Unternehmen gleichermaßen gefährlich und resultieren nicht selten in Verlust von Geld oder des Rufes. Daher sollten sich Anwender bewusst sein welche Gefahren es gibt, um diese erfolgreich bekämpfen zu können. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Ever felt like you were being watched online? You know, like when you read something about New York, and the next site you visit shows you ads for New York hotels? As it turns out, on my computer, there were more than 130 companies tracking my every move (check yours here, then install this plug-in).
These companies are basically engaging in mass surveillance. Just as governments justify tracking us to prevent terrorist attacks, these companies are tracking us online, without our consent, because a marginal 0.7 percent of the population clicks on their ads.
And it’s not just online advertisers. From e-commerce websites to physical retail stores, everyone is now racing to capture more data about us. Don’t be surprised if your insurance company starts charging you more because of how it thinks you should live your life!
Don’t get me wrong, I use Facebook, Google and all those other services. I use them because I find them useful, fun or because I don’t have an alternative. But I do it knowing very well that I am partly giving away my right to privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
Anybody who walks or drives past new tracking billboards with a mobile phone in their pocket can be spied on without their knowledge or consent: a potential invasion of privacy that US Senator Charles E. Schumer wants the US Federal Trace Commission (FTC) to investigate.
Schumer, a Democrat from New York, delivered a briefing in Times Square on Sunday, electronic billboards blinking and scrolling behind him.
From his remarks:
A person’s cell phone should not become a James Bond-like personal tracking device for a corporation to gather information about consumers without their consent.
No one wants to be followed or tracked throughout their day, electronically or otherwise.
These new “spying” billboards raise serious questions about privacy, Schumer said. They should be investigated by the feds, and the companies behind them should be required to offer an opt-out option for consumers who feel that they violate their privacy. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...




























Data breaches are always bad news, and this one is peculiarly bad.
Gentoo, a popular distribution of Linux, has had its GitHub repository hacked.
Hacked, as in “totally pwned”, taken over, and modified; so far, no one seems to be sure quite how or why.
That’s the bad news.
Fortunately (we like to find silver linings here at Naked Security):
The Gentoo team didn’t beat around the bush, and quickly published an unequivocal statement about the breach.
The Gentoo GitHub repository is only a secondary copy of the main Gentoo source code.
The main Gentoo repository is intact.
All changes in the main Gentoo repository are digitally signed and can therefore be verified.
As far as we know, the main Gentoo signing key is safe, so the digital signatures are reliable.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux