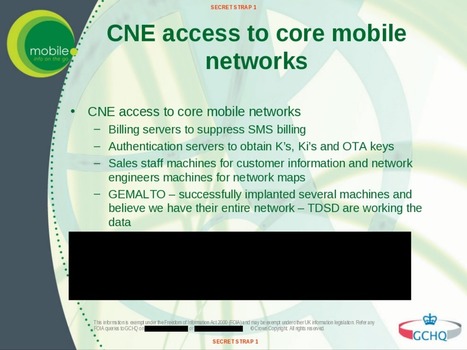
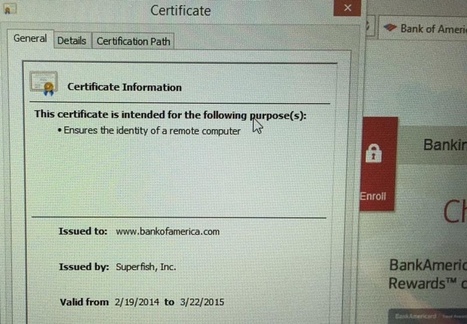
Lenovo simply can't catch a break. After the massive negative attention it received for their ill-advised decision to ship some of its notebooks with pre-installed adware that also uses MITM SSL certificates, for a short time on Wednesday their main domain - Lenovo.com - has been hijacked and effectively defaced by the hacker collective Lizard Squad.
The defaced page showed a slideshow of photos of two youngsters - according to Brian Krebs, they are Ryan King (aka “Starfall”) and Rory Andrew Godfrey (“KMS”), two former members of the hacker collective Hack The Planet - accompanied with music. The reason for the defacement is purportedly Lenovo's Superfish blunder.
The defaced page pointed to Lizard Squad's Twitter feed and served as an advertisement for its LizardStresser DoS service.
The hackers didn't compromise Lenovo's servers. Instead, they (apparently) compromised those of Web Commerce Communications (Webnic.cc), a popular Malaysia-based Internet registrar with whom the Lenovo domain is registered.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=LENOVO
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LENOVO



 Your new post is loading...
Your new post is loading...

























Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=LENOVO
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LENOVO