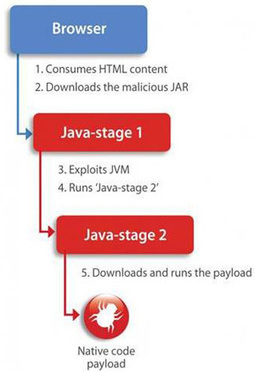
Most drive-by exploit kits use a minimal exploit shellcode that downloads and runs the final payload. This is akin to a two-stage ICBM (Inte...
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|










Learn more:
- http://www.scoop.it/t/securite-pc-et-internet?tag=Infographic
- http://www.scoop.it/t/21st-century-learning-and-teaching?tag=Infographi
- http://www.scoop.it/t/ict-security-tools
Check also:
- https://gustmees.wordpress.com/
- https://gustmeesen.wordpress.com/
- https://gustmeesfr.wordpress.com/