Establish, implement, and actively manage (track, report on, correct) the security configuration of laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
|




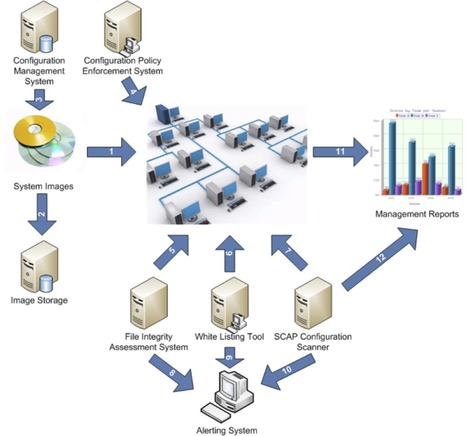






Establish, implement, and actively manage (track, report on, correct) the security configuration of laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.