 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
The team behind Exim revealed that a bug in its email server software is currently exposing millions of email servers around the world to potential attacks. Exim is a mail transfer agent (MTA) that runs in the background of email servers. It aids in the sending and receiving of email messages and helps servers act as relays for other users’ emails. All versions of Exim up to and including version 4.92.1 are affected.
The Exim team said in a recent advisory that anyone who is currently running Exim over TLS connections is vulnerable. According to the developers, the bug is unrelated to the TLS libraries (usually a source of similar bugs), so all Exim email servers are impacted, regardless of the TLS library they use.
If the server uses TLS, then an attacker could send a Server Name Identification (SNI) ending in a backslash-null sequence during the initial TLS handshake. This would allow both local or remote attackers to run malicious code with root privileges. Exim vulnerability lets attackers run commands as root on remote email servers. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Exim https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Vulnerabilities

|
Scooped by
Gust MEES
|
Ein Buffer Overflow ermöglicht es Hackern, eine in Infrastrukturanlagen viel genutzte Software anzugreifen - per Ddos oder Fremdcode. Die Lücken seien auch bereits ausgenutzt worden. Mittlerweile soll ein Patch zur Verfügung stehen.
Die Software im Kraftwerk anzugreifen, kann große Schäden verursachen.
IT-Security-Forscher des Unternehmens Tenable Security haben eine Sicherheitslücke entdeckt, die in essentieller Infrastruktursoftware auftritt. Über einen Buffer Overflow könnten Angreifer Zugriff auf ein Netzwerk erhalten, eine Denial-of-Sevice-Attacke starten oder böswilligen Code ausführen. Betroffen sind die Programme Indusoft Web Studio und Intouch Machine Edition vom Entwickler Schneider Electric. Beide werden beispielsweise in Wasserwerken, Gaskraftwerken oder Ölraffinerien eingesetzt, um die dortige Maschinerie zu verwalten und zu steuern - kritische Anlagen, bei denen Fehlfunktionen große Schäden anrichten können. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=GRID

|
Scooped by
Gust MEES
|
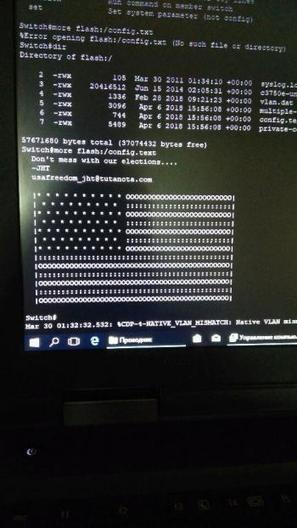
Unbekannte haben eine Sicherheitslücke in Cisco-Routern ausgenutzt und auf Systemen in Russland und Iran eine politische Botschaft hinterlassen. In westlichen Ländern hingegen schlossen sie die Lücke - behauptet zumindest eine anonyme E-Mail.
Hacker mit Sympathie für die USA nehmen für sich in Anspruch, am vergangenen Freitag zahlreiche Computersysteme in Russland und dem Iran über eine Sicherheitslücke gekapert und eine Abbildung der amerikanischen Flagge hinterlassen zu haben – zusammen mit dem Warnhinweis: "Don't mess with our elections..." (zu deutsch etwa: Mischt euch nicht in unsere Wahlen ein). Das meldet das Online-Magazin Motherboard.
"Don't mess with our elections..." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Palant commented: "Turns out that the corresponding NSS bug has been sitting around for the past nine years. That’s also at least how long software to crack password manager protection has been available to anybody interested.
So, is this issue so hard to address? Not really according to Palant: "NSS library implements PBKDF2 algorithm, which would slow down brute-forcing attacks considerably if used with at least 100,000 iterations. Of course, it would be nice to see NSS implement a more resilient algorithm like Argon2, but that’s wishful thinking seeing a fundamental bug that didn’t find an owner in nine years."
It is not clear whether the bug has been fixed by Mozilla. Infosecurity Magazine has contacted the company for comment. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Firefox... https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Les applications Hotspot Shield, PureVPN et ZenMate exhibent des vulnérabilités
Qui laissent les adresses IP des utilisateurs filtrer
Le 14 mars 2018, par Patrick Ruiz, Chroniqueur Actualités
Des services VPN populaires exhibent des failles de sécurité qui permettent la divulgation des informations sensibles de leurs utilisateurs. L’information est de vpnMentor, un site qui a vocation à les classer ; ce dernier pointe Hotspot Shield, PureVPN et ZenMate du doigt. Le site dit s’être appuyé sur l’expertise de trois chercheurs en sécurité spécialisés en la matière. Dans le détail technique publié par ces derniers, on peut d’ores et déjà dire que les vulnérabilités sont liées à des soucis avec des scripts de configuration de proxy.
Le rapport des chercheurs crédite Hotspot Shield de trois entrées dans la base de données du projet Common Vulnerabilities and Exposures (CVE). La faille référencée CVE-2018-7880 illustre clairement le propos des chercheurs. Une analyse du script de configuration de proxy (d’une version non corrigée du plugin Chrome de Hotspot Shield) a révélé qu’il suffit qu’une URL contienne une interface logique de réseau (un hôte local) pour contourner le VPN.
Dit autrement, il suffit qu’un attaquant amène un internaute à visiter une adresse du type localhost.test.com pour que le VPN cesse de le protéger. Dans ce cas, le navigateur se connecte directement à la cible sans suivre les règles inscrites dans le fichier de configuration de proxy. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|
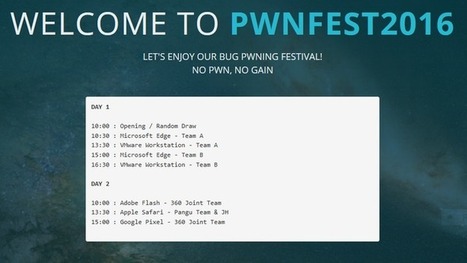
Zwei Tage lang demonstrierten Hacker in Seoul auf dem "PwnFest" diverse Schwachstellen verbreiteter Software, darunter der Browser Edge und Safari. Auch VMWare Workstations und das Google Pixel wurden geknackt.
Im Rahmen des Hacker-Events "PwnFest 2016" haben Teilnehmer am vergangenen Donnerstag jeweils gleich zweimal Sicherheitsprobleme bei Microsoft Edge unter Windows 10 (Red Stone 1) und von VMWare Workstation 12.5.1 demonstriert. Am Freitag knackte ein chinesisches Hacker-Team dann auch Googles Smartphone Pixel mit Android 7/Nougat und zeigten Sicherheitslücken in Apples Browser Safari unter macOS Sierra auf. Das zweitägige Hackerfestival PwnFest fand im Rahmen der "Power of Community"-Sicherheitskonferenz in Seoul statt. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
An attacker with access to security-sensitive information about the Firefox web browser went unnoticed for up to two years, putting hundreds of millions of users at risk.
The attacker was able to spy on highly sensitive information by gaining access to a privileged account on Bugzilla@Mozilla, the bug tracking software the Mozilla corporation uses to store information about flaws in its software.
The company behind the popular web browser has revealed details of the breach in an FAQ document. It explains that the attacker gained access to information about 185 non-public bugs, of which 53 were classed as severe vulnerabilities.
Ten of those severe vulnerabilities were not fixed when the attacker became aware of them, meaning that they could have been used to attack Firefox, and at least one of them was used in-the-wild.
The window of opportunity to successfully exploit that bug was less than 36 days, but three of the bugs were known to the attacker and un-patched for far longer; two for more than 130 days and one for almost a year.
In the face of such an open window of opportunity, Mozilla's boilerplate assurance that "there is no indication that any of the other bugs the attacker accessed have been exploited" isn't very reassuring - absence of evidence is not evidence of absence after all.
Mozilla's bug tracking system appears to have been infiltrated because of password reuse by one of its privileged users.
Learn more / Mehr erfahren:
https://gustmees.wordpress.com/2012/05/02/get-smart-with-5-minutes-tutorialsit-securitypart-1-browsers/
https://gustmeesde.wordpress.com/2014/12/16/browser-sind-das-einfallstor-fur-malware-sind-eure-browser-up-to-date/

|
Scooped by
Gust MEES
|
Une vulnérabilité, permettant l'exécution de code malicieux, a été découverte dans Microsoft Word. Cette vulnérabilité est déjà exploitée activement dans des pièces jointes au format RTF (Rich text files) de courriers électroniques indésirables. Références Classification Orange (niveau 4/5) Systèmes vulnérables Toutes les versions de Microsoft Office Word sont vulnérables (même sur Mac). Mesures à prendre : - n'ouvrez pas les fichiers au format RTF avec Word ;
- appliquez la solution de contournement de Microsoft en attendant une mise à jour ;
- réglez word pour que les fichiers RTF soient bloqués ;
- installez l'outil de protection contre l'exploitation de vos logiciels, EMET ;
- observez les réflexes BEE SECURE/CASES de sécurité.

|
Scooped by
Gust MEES
|
Exploit broker Vupen won four cash prizes for zero-day exploits of Internet Explorer 11, Firefox, Adobe Reader and Flash at the Pwn2Own contest.
iPhones and iPads will be vulnerable until they get the iOS 7 update, which is scheduled for release later this year. Until then, you might want to avoid plugging into sleazy charging stations, tho...
Via Gust MEES

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Adobe hat seine multimedialen Browser Plug-ins Flash Player und Shockwave Player aktualisiert. In beiden Programmen haben die Entwickler eine Reihe als kritisch eingestufter Sicherheitslücken beseitigt.
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Over a million fiber routers can be remotely accessed, thanks to an authentication bypass bug that's easily exploited by modifying the URL in the browser's address bar.
The bug lets anyone bypass the router's login page and access pages within -- simply by adding "?images/" to the end of the web address on any of the router's configuration pages, giving an attacker near complete access to the router. Because the ping and traceroute commands on the device's diagnostic page are running at "root" level, other commands can be remotely run on the device, too.
The findings, published Monday, say the bug is found in routers used for fiber connections. These routers are central in bringing high-speed fiber internet to people's homes.
At the time of writing, about 1.06 million routers marked were listed on Shodan, the search engine for unprotected devices and databases. Half the vulnerable routers are located on the Telmex network in Mexico, and the rest are found on in Kazakhstan and Vietnam. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Router

|
Scooped by
Gust MEES
|
Ein Sicherheitsforscher warnt erneut: In Firefox und Thunderbird gespeicherte Passwörter sind nicht effektiv vor Datendiebstahl geschützt.
Angreifer könnten mit vergleichsweise wenig Aufwand das Master-Kennwort des Passwort-Tresors in Mozillas Firefox und Thunderbird erraten. Wer das kennt, kann die im Mail-Client und Webbrowser gespeicherten Passwörter für Onlinedienste im Klartext einsehen.
Davor warnt nun erneut ein Sicherheitsforscher. Bereits vor neun Jahren gab es Hinweise auf diesen Missstand. Daran hat sich offensichtlich bis jetzt nichts geändert.
Schutz knackbar
Die beiden Anwendungen schützen das Master-Passwort zwar, dafür kommt jedoch das längst als geknackt geltende Hash-Verfahren SHA-1 zum Einsatz. Eine Zufallszahl (Salt) verfremdet den Hash, damit gleiche Passwörter nicht den gleichen Hash bekommen. Das erschwert ein Erraten. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Firefox... https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Dieses Jahr haben die Pwn2Own-Veranstalter ein Preisgeld von zwei Millionen US-Dollar ausgerufen. Trotz einiger Hack-Erfolge blieb ein Großteil der Prämie jedoch im Topf.
An zwei Tagen haben sich Hacker aus vielen Teilen der Welt über verschiedene Anwendungen, Browser, virtuelle Maschinen und Windows hergemacht und einige Erfolge erzielt. Auf dem jährlich stattfindenden Wettbewerb Pwn2Own nutzen Hacker für den guten Zweck Zero-Day-Sicherheitslücken unter Zeitdruck aus. Klappt das, streichen die Teilnehmer Prämien ein. Die Entwickler der geknackten Software haben dann 90 Tage Zeit, die Lücken zu schließen.
Dieses Jahr war der Topf mit zwei Millionen US-Dollar prall gefüllt. Der Veranstalter Trend Micro schüttete aber "nur" 267.000 US-Dollar aus. Das könnte unter anderem dran liegen, dass die chinesische Regierung Sicherheitsforschern aus dem eigenen Land seit Neuestem die Teilnahme an Hacking-Wettbewerben verbietet. In der Vergangenheit haben chinesische Sicherheitsforscher den Wettbewerb oft dominiert.
Jacke als Auszeichnung
Gewonnen hat dieses Jahr mit Abstand der Sicherheitsforscher Richard Zhu. Er hat Microsofts Edge und Mozillas Firefox erfolgreich attackiert und übernommen. Dafür hat Zhu 120.000 US-Dollar eingestrichen. Klappt ein Hack, kann der Teilnehmer das gehackte Gerät behalten. Der Hauptgewinner darf sich zudem mit der Master-of-Pwn-Jacke schmücken.
Insgesamt nutzten die diesjährigen Pwn2Own-Hacker fünf Apple-Bugs, vier Microsoft-Lücken, zwei Oracle-Schwachstellen und einen Mozilla-Bug erfolgreich aus. Mit 250.000 US-Dollar war das höchste Preisgeld für einen Ausbruch aus der Sandbox von Microsofts Virtualisierungslösung Hyper-V ausgeschrieben. Das hat dieses Jahr jedoch nicht geklappt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pwn20wn

|
Scooped by
Gust MEES
|
Zyklon, a fully featured backdoor, is making the rounds using recently patched vulnerabilities in Microsoft Office.
The dismally named code has been around since early 2016; it’s an HTTP malware with a wide range of capabilities, including keylogging, password harvesting, downloading and executing additional plugins, conducting distributed denial-of-service (DDoS) attacks and self-updating and self-removing. FireEye researchers, who uncovered this latest wave of attacks, said that it also can download several plugins from browsers and email software, some of which include features such as cryptocurrency mining and password recovery. Additionally, Zyklon has a mechanism to monitor the spread and impact of its activities and uses the Tor anonymity network to communicate with its command-and-control (C2) server.
In an analysis, FireEye found that Zyklon is being delivered primarily through spam emails with an attached malicious Word document, targeting telecommunications, insurance and financial services. It’s using two Microsoft vulnerabilities: CVE-2017-8759, which was discovered by FireEye in September 2017, and CVE-2017-11882, a remote code execution bug.
CVE-2017-8759 is a .NET framework issue patched by Microsoft in October. An exploit allows attackers to install programs, manipulate data and create new privileged accounts. The second vulnerability was patched in November – though it was found to have existed for 17 years.
The threat actors are banking on administrators taking their time patching – a common tactic. Users should, of course, update their systems as soon as possible, given Zyklon’s virulent abilities. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
Ce bulletin a été rédigé par Vigil@nce : https://vigilance.fr/offre SYNTHÈSE DE LA VULNÉRABILITÉ Un attaquant peut employer plusieurs vulnérabilités de Moodle. Produits concernés : Fedora. Gravité : 2/4.

|
Scooped by
Gust MEES
|
Une étude menée aux Etats-Unis par la division sécurité d’IBM révèle que 60% des applications mobiles de rencontres les plus populaires sont potentiellement vulnérables à différentes cyber-attaques, ce qui fait courir un risque aux données personnelles des utilisateurs et aux données sensibles de l’entreprise.
L’étude IBM révèle que nombre de ces applications de rencontres permettent un accès à des fonctionnalités supplémentaires sur les appareils mobiles (tels que l’appareil photo, le microphone, le stockage, la localisation GPS et les informations de facturation du portefeuille mobile) qui, associées aux vulnérabilités, peuvent être exploitées par les pirates. IBM a également révélé que près de 50% des entreprises comptent au moins une application de rencontres connue, installée par un employé sur son appareil mobile qu’il utilise pour accéder à des informations confidentielles de l’entreprise.

|
Scooped by
Gust MEES
|
Despite huge leaps in secure code, nothing is immune when hackers are motivated.
The first day of this year's Pwn2Own 2014and the companion contest that ran concurrently stuck with much the same theme, with successful hacks of the Internet Explorer, Firefox, and Safari browsers and Adobe's Flash and Reader applications.
But as long as there's a strong enough incentive—say, in the form of financial gain or the ability to acquire valuable national security or industry intelligence—exploits like the ones delivered at Pwn2Own won't just be possible. They'll be inevitable.

|
Scooped by
Gust MEES
|
Vupen Security, une entreprise française controversée, a réalisé plusieurs hacks de bon niveau qui lui ont valu quatre récompenses. Elle promet un 0-day ravageur pour Chrome.
A security vulnerability in the WP Banners Lite plugin for WordPress sites allows an attacker to inject malicious html or javascript code.
Via Gust MEES

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Adobe hat vier Security Bulletins veröffentlicht, die kritische Lücken im Shockwave Player sowie in Photoshop, Illustrator und Flash Pro behandeln. Doch Gratis-Updates gibt es nur für den Shockwave Player, ===> Benutzer der Premium-Produkte sollen zahlen. <=== Weiter lesen...
|



 Your new post is loading...
Your new post is loading...





























The team behind Exim revealed that a bug in its email server software is currently exposing millions of email servers around the world to potential attacks. Exim is a mail transfer agent (MTA) that runs in the background of email servers. It aids in the sending and receiving of email messages and helps servers act as relays for other users’ emails. All versions of Exim up to and including version 4.92.1 are affected.
The Exim team said in a recent advisory that anyone who is currently running Exim over TLS connections is vulnerable. According to the developers, the bug is unrelated to the TLS libraries (usually a source of similar bugs), so all Exim email servers are impacted, regardless of the TLS library they use.
If the server uses TLS, then an attacker could send a Server Name Identification (SNI) ending in a backslash-null sequence during the initial TLS handshake. This would allow both local or remote attackers to run malicious code with root privileges.
Exim vulnerability lets attackers run commands as root on remote email servers.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Exim
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Vulnerabilities