Was haben die Netzauftritte von Fußballstar Cristiano Ronaldo und der gemeinnützigen Organisation Make-a-Wish mit indischen Behörden-Websites gemeinsam? Sie alle wurden schon einmal von Kriminellen so manipuliert, dass sie die Rechenleistung der Computer und Smartphones ihrer Besucher kaperten. Bis die Betreiber der Angebote merkten, was los war, schürften die Geräte der Website-Besucher nach der Digitalwährung Monero - immer solange, wie die Seiten im Browser geöffnet waren.
Internetsurfer werden ohne ihr Wissen Krypto-Schürfer: Diese Betrugsmasche, die auch mit anderen Digitalwährungen funktioniert, heißt Cryptojacking - kombiniert aus "Cryptocurrency" (Kryptowährung) und "Hijacking" (Entführung). Der Angriff über den Browser schadet dem Gerät in der Regel nicht unmittelbar, davon abgesehen, dass es wegen der Rechenvorgänge oft heiß oder lauter wird. Er ist aber doch ärgerlich, weil Dritte hier quasi Akkuleistung oder Strom sowie Bandbreite von ihren Opfern abgreifen.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking



 Your new post is loading...
Your new post is loading...



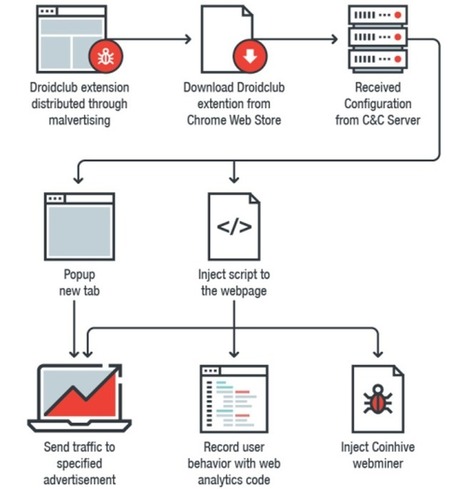












Was haben die Netzauftritte von Fußballstar Cristiano Ronaldo und der gemeinnützigen Organisation Make-a-Wish mit indischen Behörden-Websites gemeinsam? Sie alle wurden schon einmal von Kriminellen so manipuliert, dass sie die Rechenleistung der Computer und Smartphones ihrer Besucher kaperten. Bis die Betreiber der Angebote merkten, was los war, schürften die Geräte der Website-Besucher nach der Digitalwährung Monero - immer solange, wie die Seiten im Browser geöffnet waren.
Internetsurfer werden ohne ihr Wissen Krypto-Schürfer: Diese Betrugsmasche, die auch mit anderen Digitalwährungen funktioniert, heißt Cryptojacking - kombiniert aus "Cryptocurrency" (Kryptowährung) und "Hijacking" (Entführung). Der Angriff über den Browser schadet dem Gerät in der Regel nicht unmittelbar, davon abgesehen, dass es wegen der Rechenvorgänge oft heiß oder lauter wird. Er ist aber doch ärgerlich, weil Dritte hier quasi Akkuleistung oder Strom sowie Bandbreite von ihren Opfern abgreifen.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency
https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking