 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Un nouveau malware circule sur Android. Repéré par un groupe de chercheurs, il se présente sous la forme d'une mise à jour critique du système et permet à un tiers de prendre le contrôle d'un smartphone en collectant des données personnelles.
Le cabinet de sécurité Zimperium, qui avait déjà découvert la faille StageFright en 2015, explique que le malware a été intégré dans une application baptisée System Update, disponible en dehors du Play Store. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
A new Android malware strain has been uncovered, part of the Rampant Kitten threat group’s widespread surveillance campaign that targets Telegram credentials and more.
Researchers have uncovered a threat group launching surveillance campaigns that target victims’ personal device data, browser credentials and Telegram messaging application files. One notable tool in the group’s arsenal is an Android malware that collects all two-factor authentication (2FA) security codes sent to devices, sniffs out Telegram credentials and launches Google account phishing attacks.
Researchers found the threat group, dubbed Rampant Kitten, has targeted Iranian entities with surveillance campaigns for at least six years. It specifically targets Iranian minorities and anti-regime organizations, including the Association of Families of Camp Ashraf and Liberty Residents (AFALR); and the Azerbaijan National Resistance Organization.
The threat group has relied on a wide array of tools for carrying out their attacks, including four Windows info-stealer variants used for pilfering Telegram and KeePass account information; phishing pages that impersonate Telegram to steal passwords; and the aforementioned Android backdoor that extracts 2FA codes from SMS messages and records the phone’s voice surroundings. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Two-factor+authentication

|
Scooped by
Gust MEES
|
Over the past six months, a new Android malware strain has made a name for itself after popping up on the radar of several antivirus companies, and annoying users thanks to a self-reinstall mechanism that has made it near impossible to remove.
Named xHelper, this malware was first spotted back in March but slowly expanded to infect more than 32,000 devices by August (per Malwarebytes), eventually reaching a total of 45,000 infections this month (per Symantec).
The malware is on a clear upward trajectory. Symantec says the xHelper crew is making on average 131 new victims per day and around 2,400 new victims per month. Most of these infections have been spotted in India, the US, and Russia.
INSTALLED VIA THIRD-PARTY APPS
According to Malwarebytes, the source of these infections is "web redirects" that send users to web pages hosting Android apps. These sites instruct users on how to side-load unofficial Android apps from outside the Play Store. Code hidden in these apps downloads the xHelper trojan. Learn more / En savoir plus / Mehr erfahren: https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/ https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
An Android banking trojan has returned with improvements which allow it to record the screens of infected devices while also adding new techniques that help the malware remain hidden from victims.
Can Google win its battle with Android malware?
Cybercriminals are sneaking malicious apps into Google's official app store. Can they be stopped?
First detailed by cybersecurity researchers at ThreatFabric in October last year, BianLian started life as a dropper for other forms of malware, most notably the Anubis banking malware, which has stolen funds from thousands of Android users around the globe.
But the cybercriminals behind BianLian soon changed their tactics, altering the code and re-purposing the malware into a banking trojan in its own right – repeatedly bypassing protections in the official Google Play app store as a means of distributing their malicious payload. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Malware
Bürgerrechtler haben bereits vor der Silverpush-Software gewarnt, Anti-Viren-Dienstleister sie als Malware eingestuft. Das Entwickler-Kit wird inzwischen von San Francisco aus weiter verbreitet.
Die Forscher haben zudem vergleichbar funktionierende, auf den Handelsbereich ausgerichtete uBeacons von Anbietern wie Lisnr oder Shopkick ausfindig gemacht, aber in deutlich geringerer Anzahl. Ultraschall-Signale von Shopkick konnten sie etwa in vier von 35 untersuchten Läden in zwei europäischen Städten aufzeichnen. Der Unterschied zu Silverpush sei, dass der Nutzer die einschlägige Anwendung absichtlich starte, um sich etwa Einkaufsvorteile vor Ort zu verschaffen. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Android http://www.scoop.it/t/securite-pc-et-internet/?&tag=Apps http://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking

|
Scooped by
Gust MEES
|
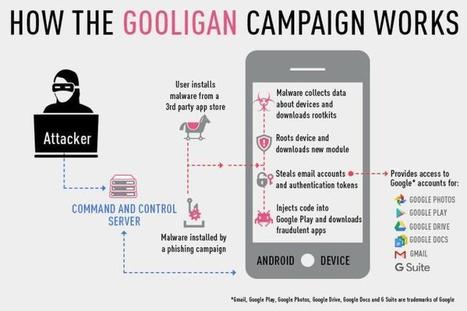
A million Google accounts have been compromised in a massive fraud campaign exploiting Android devices and Google Play.
At the heart of the campaign is a new variant of Android malware dubbed Gooligan, concealed in dozens of Android apps that exploit two unpatched flaws in Android to root infected devices.
The malware nabs email account information and authentication tokens for accessing Google accounts. The attackers use the tokens to install select apps from Google Play on an infected device to boost in-app advertising revenue. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android

|
Scooped by
Gust MEES
|
We’ve seen malware for PCs that infects mobile devices, but it turns out there’s also malware for mobile devices designed to infect PCs. Kaspersky researchers have discovered a new piece of Android malware that masquerades as a “cleaner” app meant to free memory for Google’s operating system but wreaks havoc on your smartphone in the background and on Microsoft’s operating system when it’s connected to a PC. The security firm says the malware has the most “extensive feature set” it has ever seen in one mobile app. Here’s the list: Sending SMS messages.Enabling Wi-Fi.Gathering information about the device.Opening arbitrary links in a browser.Uploading the SD card’s entire contents.Uploading an arbitrary file (or folder) to the master’s server.Uploading all SMS messages.Deleting all SMS messages.Uploading all the contacts/photos/coordinates from the device to the master.

|
Scooped by
Gust MEES
|
Recently Trusteer discovered the first Tatanga-based man in the mobile (MITMO) attack as well as new SPITMO configurations which are targeting Android mobile banking users in Germany, the Netherlands, Portugal and Spain. With nearly 60 percent of the market and a reputation for weak app security, it’s no surprise that Android has become the preferred target for financial malware. Read more: http://www.net-security.org/malware_news.php?id=2183

|
Scooped by
Gust MEES
|
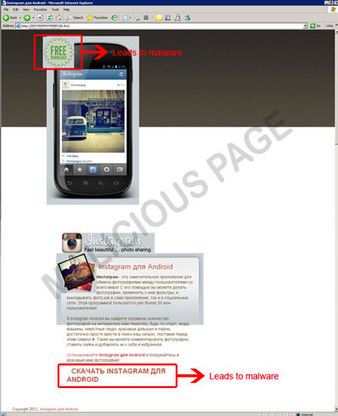
Instagram, the popular free photo sharing app for iOS devices, is now available for download for Android users on Google Play and Instagram's website. Unfortunately, a rogue malicious version of it is also being pushed onto Russian Android users, offered from a webpage that mimics the legitimate one: read more...
|

|
Scooped by
Gust MEES
|
The malicious app spreads the BlackRock malware, which steals credentials from 458 services – including Twitter, WhatsApp, Facebook and Amazon.
Researchers are warning of a fake version of the popular audio chat app Clubhouse, which delivers malware that steals login credentials for more than 450 apps.
Clubhouse has burst on the social media scene over the past few months, gaining hype through its audio-chat rooms where participants can discuss anything from politics to relationships. Despite being invite-only, and only being around for a year, the app is closing in on 13 million downloads. However, as of now the app is only available on Apple’s App Store mobile application marketplace – there’s no Android version yet (though plans are in the works to develop one).
Cybercriminals are swooping in on Android users looking to download Clubhouse by creating their own fake Android version of the app. To add a legitimacy to the scam, the fake app is delivered from a website purporting to be the real Clubhouse website – which “looks like the real deal,” said Lukas Stefanko, researcher with ESET. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Apps

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
The spyware poses as a legitimate application, spreading via SMS messages to victims’ contact lists.
An Android malware dubbed “FunkyBot” has started making the scene in Japan, operated by the same attackers responsible for the FakeSpy malware. It intercepts SMS messages sent to and from infected devices.
According to FortiGuard Labs, the malware (named after logging strings found in the persistence mechanism of the payload) masquerades as a legitimate Android application. The payload thus consists of two .dex files: One is a copy of the original legitimate application that the malware is impersonating, and the other is malicious code.
As for the kill chain, a packer first determines which version of Android the phone is running on, in order to generate the proper payload. After that, the payload is started by calling the method `runCode` class through Java reflection. This starts a class called KeepAliceMain, which is used as persistence mechanism by the malware. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Two companies have discovered that someone had covertly installed malware on 38 devices used by their employees. According to security firm Check Point, the installation of the malicious apps took place somewhere along the supply chain, after phones left the manufacturer's factory and before they arrived at the two companies. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=Mobile-Security

|
Scooped by
Gust MEES
|
Ein Android-Updater der eher unbekannten Firma Ragentek ist nicht nur extrem unsicher, er verhält sich auch wie ein Rootkit. Das Programm steckt in etlichen Smartphone-Modellen chinesischer Hersteller, welche auch auf dem hiesigen Markt vertreten sind.
Über 2,8 Millionen Geräte kontaktierten die falschen Update-Server. Die Forscher versuchten, die Gerätemodelle zu identifizieren und Herstellern zuzuordnen.
Bild: AnubisNetworks In zahlreichen Android-Smartphone chinesischer Hersteller steckt eine Backdoor, durch die der Hersteller – oder ein Angreifer – beliebige Befehle mit Root-Rechten ausführen kann. Für das Security-Debakel ist offenbar ein Update-Prozess verantwortlich, der gewährleisten soll, dass die Geräte-Software auf dem aktuellen Stand ist.
Sie stammt von Ragentek und kommt nicht nur auf Android-Geräten dieses Herstellers zum Einsatz sondern auch bei BLU, Infinix Mobility, Beeline, Doogee, IKO Mobile, Leagoo und XOLO.
2,8 Millionen Geräte kontaktieren falschen Update-Server!!! Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=Android

|
Scooped by
Gust MEES
|
The fact that Android malware is an escalating issue comes as no surprise, but a recent analysis of its sheer 'market share' of the mobile malware universe is noteworthy.

|
Scooped by
Gust MEES
|
L’éditeur Trend Micro anticipe une importante croissance des malwares sur Android et avertit que la situation pourrait devenir pandémique d’ici à la fin de l’année. L’éditeur japonais affirme que le nombre d’applications malicieuses sur plates-formes Android est passé de 10 000 à 20 000 en seulement un mois et que des centaines de milliers de périphériques ont été infectés par des applications que l’on peut trouver sur la plate-forme GooglePlay. L’éditeur indique que 17 applications contenant un malware ont été téléchargées à plus de 700 000 reprises avant d’être supprimées par Google. Durant les trois premiers mois de l’année, plus de 5000 applications destinées à infecter les téléphones Android ont été découvertes, soit une multiplication par quatre et les chiffres continuent à augmenter. Pour le troisième trimestre, le nombre pourrait atteindre 38 000 malwares et … 130 000 au cours du 4ème trimestre, ce qui permet de qualifier la situation de pandémie. $$$$$$$$$$$$$$$$$$$$$$$$$$$ En savoir plus : http://www.linformaticien.com/actualites/id/25524/malwares-android-vers-la-pandemie.aspx?utm_source=twitterfeed&utm_medium=twitter
|



 Your new post is loading...
Your new post is loading...





















Un nouveau malware circule sur Android. Repéré par un groupe de chercheurs, il se présente sous la forme d'une mise à jour critique du système et permet à un tiers de prendre le contrôle d'un smartphone en collectant des données personnelles.
Le cabinet de sécurité Zimperium, qui avait déjà découvert la faille StageFright en 2015, explique que le malware a été intégré dans une application baptisée System Update, disponible en dehors du Play Store.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android