Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Security researchers have discovered a new type of "Man-in-the-Middle" (MitM) attack in the wild targeting smartphone and tablets users on devices running either iOS or Android around the world.
The MitM attack, dubbed DoubleDirect, enables an attacker to redirect a victim’s traffic of major websites such as Google, Facebook and Twitter to a device controlled by the attacker. Once done, cyber crooks can steal victims’ valuable personal data, such as email IDs, login credentials and banking information as well as can deliver malware to the targeted mobile device.
San Francisco-based mobile security firm Zimperium detailed the threat in a Thursday blog post, revealing that the DoubleDirect technique is being used by attackers in the wild in attacks against the users of web giants including Google, Facebook, Hotmail, Live.com and Twitter, across 31 countries, including the U.S., the U.K. and Canada.

|
Scooped by
Gust MEES
|
Researchers have pointed out an interesting aspect of the iOS malware. The threat contains binary code for 32-bit ARMv7, 32-bit ARMv7s, and 64-bit ARM64 architectures. This makes WireLurker the first iOS malware that targets the ARM64 architecture.
The Maiyadi App Store on which the initially discovered variants were hosted seems to be linked to the creators of the malware, Palo Alto said. One piece of evidence is the bundle identifier named "com.maiyadi.installer" in the OS X samples. The samples also include copyright information referencing Maiyadi.
The C&C servers user by WireLurker are currently inactive, and Apple has taken steps to ensure that its users are protected, including the revocation of the stolen code signing certificates used by the malware creators to run the malicious iOS apps on non-jailbroken devices.
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security?q=wirelurker

|
Scooped by
Gust MEES
|
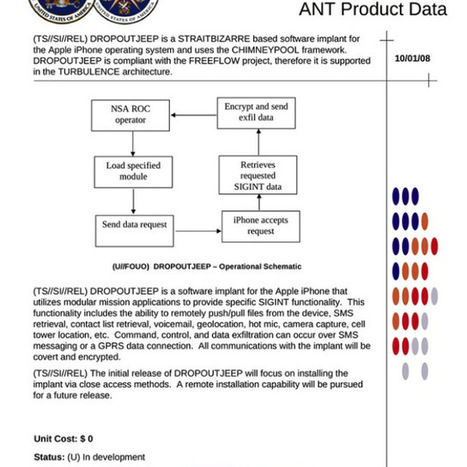
Apple has contacted TechCrunch with a statement about the DROPOUTJEEP NSA program that detailed a system by which the organization claimed it could snoop on..

|
Scooped by
Gust MEES
|
AdaptiveMobile today sheds light on the extent of a new global SMS spam threat. According to Ongoing Threat Analysis (OTA) which examines mobile security threats from around the world, consumers should to be on the lookout for fraudulent spam texts informing them they have won a free Apple product such an iPad, iPhone or MacBook.
The texts frequently include a web address that looks like it is from Apple but upon closer inspection is not a legitimate Apple website and are sent from US mobiles numbers (+1-XXX-XXX-XXXX).
“Congratulations! You are Australia’s WINNER OF THE DAY! Go to http://www.apple.au.[redacted].com to claim your prize. Must claim within 24 hrs.”
“Your phone was randomly chosen as Apple’s Over-Stock iWinner. Go to http://ie.appleoverstock.[redacted] & type code 2872 to win your Free Gift-Card now!”

|
Scooped by
Gust MEES
|
Following yesterday's claim made by AnitSec hackers that they have gotten ahold of a document containing a list of over 12 million Apple iOS devices - including Unique Device Identifiers (UDID), user names, name of device, type of device, Apple Push Notification Service tokens, ZIP codes, cellphone numbers, addresses, and more - after breaking into a computer used by an FBI agent, the agency has issued a resounding denial via Twitter: Read more: http://www.net-security.org/secworld.php?id=13528
According to Wired, Amazon no longer allows people to call Amazon and change account settings such as email addresses and credit cards, and Apple has temporarily suspended the option of asking for an AppleID password reset over the phone. Read more: http://www.net-security.org/secworld.php?id=13392
|

|
Scooped by
Gust MEES
|
L’iPhone 5S a été mis à mal par une équipe de Corée du Sud, qui a réussi à profiter d'une combinaison de deux bugs dans Safari pour en prendre le contrôle. Le Samsung Galaxy S5 non plus n'a pas réisté aux assauts des hackers. Deux équipes ont profité de failles dans la gestion du protocole NFC pour en prendre le contrôle. le Nexus 5 a lui aussi été piraté via NFC, grâce à une technique étonnante, qui a consisté à forcer un appairage Bluetooth entre deux appareils.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
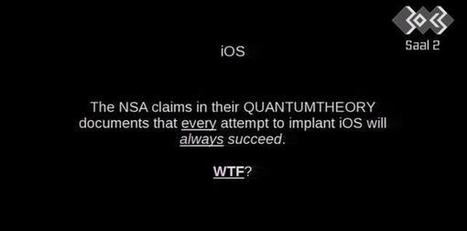
Breathless headlines suggest that the NSA can snoop on everyone's iPhone, turn on your phone's camera and read all your messages.
But the story isn't quite as simple as that.
The malware threat on Macs is real, and should not be underestimated. SophosLabs, is a new variant of the OSX/Imuler Trojan horse. In the past, earlier variants of the OSX/Imuler malware has been spread via topless photos of a Russian supermodel or embedded deep inside boobytrapped PDF files. If your Mac was successfully infected by malware like this, you have effectively given remote control of your computer and your data to an invisible and unknown party. ===> They could steal files from your Mac, spy on your emails, and plant further malware onto your systems. <=== Read more, a MUST: http://nakedsecurity.sophos.com/2012/11/13/new-mac-trojan/
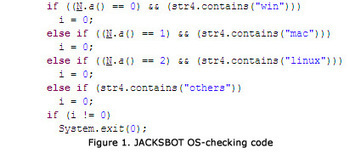
Two weeks ago, Mac security software company Intego discovered malware which it classified as "a new Java backdoor trojan called Java/Jacksbot.A.” New threats are discovered all the time, but Intego later concluded that even though Jacksbot is a variant of the Java remote access tool (RAT) created by the jailbreaking group Redpois0n, it can target multiple platforms. The malware writers behind JACKSBOT may just be testing the waters for a successful multiplatform malware; however for now they appear to be unwilling to invest the time and resources to develop the code more completely. ===> It’s likely that the authors will continue to improve the code to fully support infection for OS X and Linux. <=== Read more, a MUST: http://thenextweb.com/2012/10/31/jacksbot-java-malware-can-take-control-of-windows-mac-and-linux-systems/?utm_source=dlvr.it&amp;utm_medium=twitter

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Il semble bien que le mythe du Mac infaillible soit en train de tomber. Après l'épisode Flashback (un malware ciblant exclusivement les ... La maturité pour Apple ? Lorsque l'on regarde l'ancienne version de la page, le discours passé d'Apple fait sourire. Il était temps que l'entreprise redescende sur terre, et reconnaisse enfin la vulnérabilité de son OS aux menaces des cybercriminels. L'épisode Flashback y est certainement pour quelque chose. L'entreprise à la pomme a sûrement pris conscience de quelque chose. On espère que cela la poussera à se focaliser davantage sur la sécurité, de même que ses consommateurs (qui se croient encore trop souvent hors d'atteinte). En savoir plus : http://www.linformaticien.com/actualites/id/25390/apple-l-admet-il-y-a-des-virus-sur-mac.aspx
|




 Your new post is loading...
Your new post is loading...