Avec 250 inscrits en provenance de 41 pays, la convention Hack.lu s’impose comme référence en tant que conférence sur la cyber-sécurité.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
May 13, 2013 12:10 PM
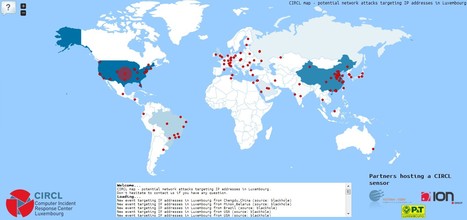
Learn more with also other REAL TIME ATTACKS global maps here:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Real-time+Web+Monitor

Gust MEES's curator insight,
May 13, 2013 12:14 PM
Learn more with also other REAL TIME ATTACKS global maps here:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Real-time+Web+Monitor

Gust MEES's curator insight,
January 17, 2013 12:26 PM
De bonnes infrastructures et des mesures proactives aident à contrer des attaques...
===> Proactive Thinking! <===
|

Philip Verghese 'Ariel's curator insight,
January 18, 2013 1:31 AM
Overview Red October is a malware family, also named Sputnik, which was detected in October 2012 by Kaspersky. It was active since 2007, installations have been spotted around the globe and targets were diplomatic and governmental agencies. The malware usually was sent by email to selected people in the respective organizations. |














Elle pourrait même accueillir le plus grand challenge Capture The Flag au monde…
En savoir plus :
- www.hack.lu