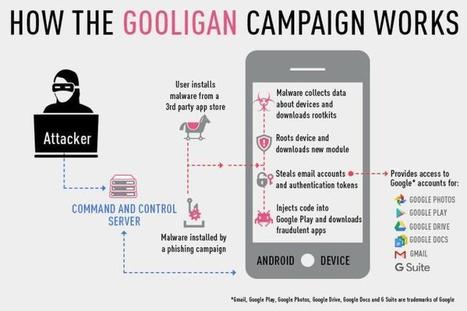
The malicious app spreads the BlackRock malware, which steals credentials from 458 services – including Twitter, WhatsApp, Facebook and Amazon.
Researchers are warning of a fake version of the popular audio chat app Clubhouse, which delivers malware that steals login credentials for more than 450 apps.
Clubhouse has burst on the social media scene over the past few months, gaining hype through its audio-chat rooms where participants can discuss anything from politics to relationships. Despite being invite-only, and only being around for a year, the app is closing in on 13 million downloads. However, as of now the app is only available on Apple’s App Store mobile application marketplace – there’s no Android version yet (though plans are in the works to develop one).
Cybercriminals are swooping in on Android users looking to download Clubhouse by creating their own fake Android version of the app. To add a legitimacy to the scam, the fake app is delivered from a website purporting to be the real Clubhouse website – which “looks like the real deal,” said Lukas Stefanko, researcher with ESET.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Apps



 Your new post is loading...
Your new post is loading...















The malicious app spreads the BlackRock malware, which steals credentials from 458 services – including Twitter, WhatsApp, Facebook and Amazon.
Researchers are warning of a fake version of the popular audio chat app Clubhouse, which delivers malware that steals login credentials for more than 450 apps.
Clubhouse has burst on the social media scene over the past few months, gaining hype through its audio-chat rooms where participants can discuss anything from politics to relationships. Despite being invite-only, and only being around for a year, the app is closing in on 13 million downloads. However, as of now the app is only available on Apple’s App Store mobile application marketplace – there’s no Android version yet (though plans are in the works to develop one).
Cybercriminals are swooping in on Android users looking to download Clubhouse by creating their own fake Android version of the app. To add a legitimacy to the scam, the fake app is delivered from a website purporting to be the real Clubhouse website – which “looks like the real deal,” said Lukas Stefanko, researcher with ESET.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android
https://www.scoop.it/topic/securite-pc-et-internet/?&tag=Apps