 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
If you've been experiencing Tor network connectivity and performance issues lately, you're not the only one since many others have had problems with onion and i2p sites loading slower or not loading at all.
Tor Project's Executive Director Isabela Dias Fernandes revealed on Tuesday that a wave of distributed denial-of-service (DDoS) attacks has been targeting the network since at least July 2022.
"At some points, the attacks impacted the network severely enough that users could not load pages or access onion services," Fernandes said on Tuesday. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/topic/securite-pc-et-internet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Wer im Internet surft, ist Freiwild. Von allen Seiten wird Ihr Browser angezapft: sei es von der Werbeindustrie, von Dienstanbietern, Geheimdiensten und Hackern. Das Tor-Netzwerk ist zwar in den letzten Jahren etwas in Verruf geraten, bietet aber immer noch mehr Anonymität als alle anderen Maßnahmen. Außerdem kommen Sie über den Tor-Browser in das sonst geheime Darknet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
Mac and Linux versions of the Tor anonymity browser just received a temporary fix for a critical vulnerability that leaks users' IP addresses when they visit certain types of addresses.
TorMoil, as the flaw has been dubbed by its discoverer, is triggered when users click on links that begin with file:// rather than the more common https:// and http:// address prefixes. When the Tor browser for macOS and Linux is in the process of opening such an address, "the operating system may directly connect to the remote host, bypassing Tor Browser," according to a brief blog post published Tuesday by We Are Segment, the security firm that privately reported the bug to Tor developers.
On Friday, members of the Tor Project issued a temporary work-around that plugs that IP leak. Until the final fix is in place, updated versions of the browser may not behave properly when navigating to file:// addresses. They said both the Windows versions of Tor, Tails, and the sandboxed Tor browser that's in alpha testing aren't vulnerable.
"The fix we deployed is just a workaround stopping the leak," Tor officials wrote in a post announcing Friday's release. "As a result of that navigating file:// URLs in the browser might not work as expected anymore. In particular entering file:// URLs in the URL bar and clicking on resulting links is broken. Opening those in a new tab or new window does not work either. A workaround for those issues is dragging the link into the URL bar or on a tab instead. We track this follow-up regression in bug 24136." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
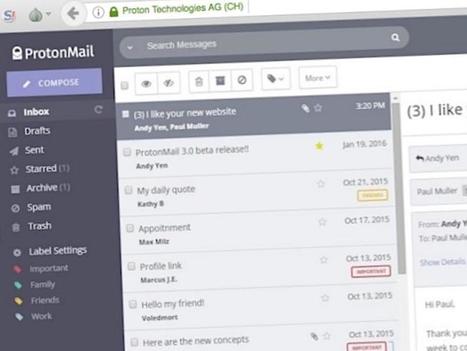
ProtonMail now has a home on the dark web. The encrypted email provider announced Thursday it will allow its users to access the site through the Tor anonymity service. The aim is to allow its more than 2 million users access the provider by taking "active measures to defend against state-sponsored censorship," such as government-mandated blocks at the internet provider level. Users of the Tor Browser can now access the site at https://protonirockerxow.onion. ProtonMail's co-founder Andy Yen said that while censorship in some parts of the world is "inevitable," the company worked with the Tor Project to help users bypass it Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Tor, or “The Onion Router” as it was originally known, is used around the world as an anonymity network. It provides a private method of communication for journalists, those living under authoritarian governments, and people who are just up to some shady stuff. While Tor is still the most robust form of online anonymity we have, it’s not bulletproof as the repeated takedown of The Silk Road and other law enforcement actions have shown. Now, two computer scientists say they’ve uncovered snoops inside the Tor network that may be listening in on what you’re doing. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet?q=tor

|
Scooped by
Gust MEES
|
In seiner Standard-Konfiguration liefert der beliebte Web-Server-Dienst Informationen, die die Anonymitäts-Versprechen eines Tor Hidden Services gefährden. Diese anonymen Tor-Dienste sind der Kern des oft zitierten "Dark Net".
Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A security researcher conducted an experiment to demonstrate that someone is sniffing passing traffic from Tor network exit nodes.
When talking about Tor network, normally everyone assumes that you have an end-to-end security, but someone believes it may be wrong as it was discovered by the security researcher Chloe.
Tor network is free and it is the safest way to be anonymous since it hides your original IP from the destination server, to do that Tor uses relays to redirect traffic, but now the security researcher Chloe concludes that traffic is being sniffed in the exit nodes.

|
Scooped by
Gust MEES
|
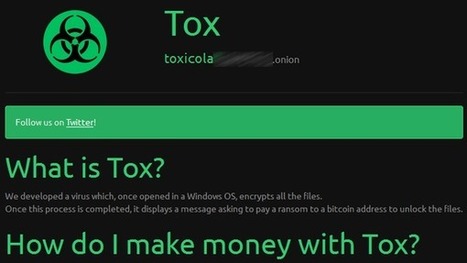
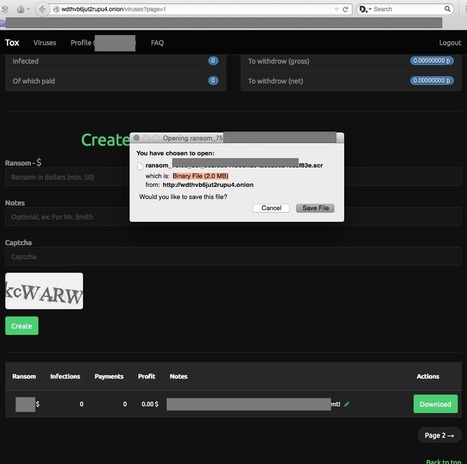
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|
Das Tor-Netzwerk: Dort tummeln sich Whistleblower, Aktivisten, politisch Verfolgte, aber auch Drogenhändler oder Pädophile. Alle wollen dort aus unterschiedlichen Motiven ihre Anonymität bewahren. Es gibt aber Zweifel an der Effektivität der Anonymisierung.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
The malware also mines Monero & Ethereum cryptocurrency on targeted devices.
We’re seeing new variants of malware being deployed every day. just yesterday we covered a skimmer funneling funds through Telegram and today we’re back with a new report by WeLiveSecurity.
Shedding light on a new malware family named KryptoCibule; the researchers report on 3 main tasks that it seeks to perform:
Mining Monero and Ethereum cryptocurrencies using a CPU and GPU respectively
Stealing funds by replacing legitimate wallet addresses with attacker-controlled ones with the help of the clipboard
Steal and extract cryptocurrency-related files
See: Best legal, safe & free online streaming sites – 2020
Alongside this, a remote administration tool (RAT) is also used to maintain access to the victim’s machine in order to control it. Furthermore, both the TOR Network and BitTorrent protocol is used for transmitting data and communication in general. This is yet another example of how legitimate services can be used by attackers for their own nefarious motives. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/topic/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
Hackers have breached SyTech, a contractor for FSB, Russia's national intelligence service, from where they stole information about internal projects the company was working on behalf of the agency -- including one for deanonymizing Tor traffic.
The breach took place last weekend, on July 13, when a group of hackers going by the name of 0v1ru$ hacked into SyTech's Active Directory server from where they gained access to the company's entire IT network, including a JIRA instance.
Hackers stole 7.5TB of data from the contractor's network, and they defaced the company's website with a "yoba face," an emoji popular with Russian users that stands for "trolling."
Hackers posted screenshots of the company's servers on Twitter and later shared the stolen data with Digital Revolution, another hacking group who last year breached Quantum, another FSB contractor.
This second hacker group shared the stolen files in greater detail on their Twitter account, on Thursday, July 18, and with Russian journalists afterward. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
Eine Sicherheitslücke im Tor-Browser ist geschlossen worden. (Bild: David Bates/Golem.de)
LINUX UND MAC:
Tor-Browser-Exploit verrät IP-Adresse einiger Nutzer
Unter bestimmten Voraussetzungen verrät der Tor-Browser die unverschleierte IP-Adresse der Nutzer. Betroffen sind nur Mac und Linux-Versionen des Firefox-Bundles, in der täglichen Nutzung dürfte der Fehler nur wenige Personen betreffen.
Das Tor-Projekt hat ein Notfallupdate für die Linux- und Mac-Versionen des Tor-Browser-Bundles veröffentlicht. Unter bestimmten Umständen verraten die beiden betroffenen Versionen die reale IP-Adresse der Nutzer und machen somit die angestrebte Anonymität kaputt. Die Windows-Version des Tor-Browsers, die Tails-Distribution und der im Alpha-Test befindliche Tor-Browser mit Sandboxing sollen nicht betroffen sein. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=TOR

|
Scooped by
Gust MEES
|
Ein Server (Bild: Dean Mouhtaropoulos/Getty Images) WANNA CRY:
Mehrere Tor-Server in Frankreich beschlagnahmt
Nach den Wanna-Cry-Angriffen ermitteln Behörden weltweit, um die Täter zu finden. In Frankreich wurden dabei offenbar zahlreiche Tor-Server bei verschiedenen Hostern beschlagnahmt.
In Frankreich wurden offenbar bei mehrere Hostern Tor-Server von der Polizei beschlagnahmt. Die Aktion steht in Zusammenhang mit der Wanna-Cry-Ransomware-Attacke, wie Golem.de aus Tor-Unterstützerkreisen erfahren hat. Die Beschlagnahmungen erfolgten am vergangenen Wochenende, kurz nach Ausbruch der Angriffe. Die Wanna-Cry-Ransomware nutzt einen Command-und-Control-Server (C2), der über das Tor-Netzwerk mit den Clients kommuniziert.
Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE http://www.scoop.it/t/securite-pc-et-internet/?&tag=WannaCry+ransomware

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Nutzer des Tor-Browsers werden mit Javascript angegriffen
Wer den Tor-Browsers nutzt, will meist vor allem eins: Anonymität. Eine aktuelle Schwachstelle im Firefox-Browser führt aber dazu, dass Nutzer identifiziert werden können. Das Problem betrifft auch Nutzer des regulären Firefox - ein Patch ist in Arbeit.
Nutzer des Tor-Browsers werden derzeit aktiv mit einer 0-Day-Lücke angegriffen, die einen Fehler im Speichermanagement des verwendeten Firefox-Browsers ausnutzt. Möglicherweise sind auch Nutzer von Firefox ohne Tor-Bundle betroffen. Die Sicherheitslücke soll es Angreifern ermöglichen, Code auf dem Rechner der Tor-Nutzer auszuführen. Mozilla arbeitet noch an einem Patch. Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|
Nach dem Weggang von Jacob Appelbaum erneuert das Torprojekt alle Direktoren. Unter anderen ersetzt der renommierte Kryptologe und Sicherheitsforscher Bruce Schneier zwei... Learn more / En savoir plus / Mehr erfahren: http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|
Eight years ago researcher Dan Egerstad demonstrated how useful having your own Tor exit nodes can be if you want to spy on people by setting up five of his own.
He used them to harvest thousands of emails and messages from embassies in Australia, Japan, Iran, India and Russia, as well as the Iranian Foreign Ministry and the Indian Ministry of Defence.
He was running exit nodes rather than entry guards but his conclusion applies to both - he was convinced (although he provided no proof of it) that governments would surely be running or spying on Tor relays too:
I am absolutely positive that I am not the only one to figure this out ... I'm pretty sure there are governments doing the exact same thing. There's probably a reason why people are volunteering to set up a node.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Last week, user Virgil Griffith went onto the Tor-talk mailing list and announced Onion City, a Dark Web search engine that allows regular web users to delve into the Dark Web.
The search engine delves into the anonymous Tor network, finds .onion sites and makes them available to regular users on the ordinary World Wide Web.
Up to now the best way to search for .onion sites has been to get on the Tor network using something like the Tor browser, but Onion City effectively does that bit for you so you can search from the comfort of your favourite, insecure web browser.

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...

























If you've been experiencing Tor network connectivity and performance issues lately, you're not the only one since many others have had problems with onion and i2p sites loading slower or not loading at all.
Tor Project's Executive Director Isabela Dias Fernandes revealed on Tuesday that a wave of distributed denial-of-service (DDoS) attacks has been targeting the network since at least July 2022.
"At some points, the attacks impacted the network severely enough that users could not load pages or access onion services," Fernandes said on Tuesday.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/topic/securite-pc-et-internet