Die Ergebnisse des Cisco Annual Security Report 2015 zeigen allerdings auch einen Wandel bei den Angriffsmethoden der Cyberkriminellen.
Ihr Primärziel sind nicht mehr Server und Betriebssysteme, ===> sondern einzelne Nutzer. <===
.
Im Vergleich zum Vorjahr nahmen dabei betrügerische Mails und Malvertising-Attacken um satte 250 Prozent zu. Und: Vor allem Anwender in hochgefährdeten Branchen fallen laut Cisco doppelt so häufig auf betrügerische Links und Adware herein.
.
Learn more:
.
- https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
.
.



 Your new post is loading...
Your new post is loading...



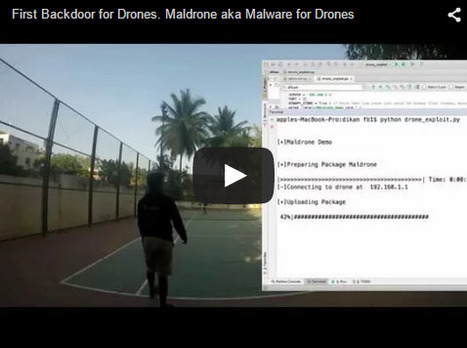




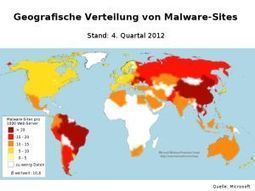







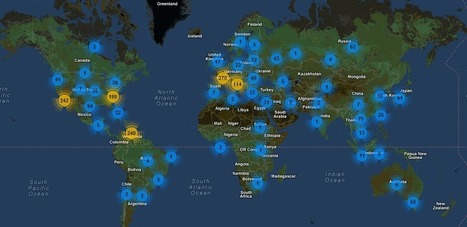

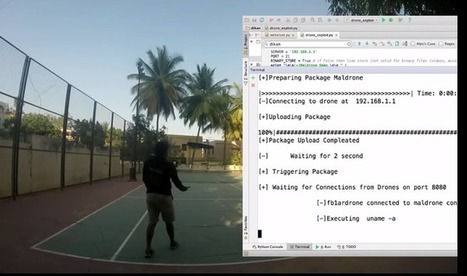




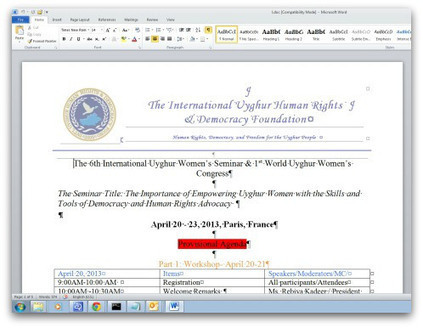









Die Ergebnisse des Cisco Annual Security Report 2015 zeigen allerdings auch einen Wandel bei den Angriffsmethoden der Cyberkriminellen.
Ihr Primärziel sind nicht mehr Server und Betriebssysteme, ===> sondern einzelne Nutzer. <===
.
Im Vergleich zum Vorjahr nahmen dabei betrügerische Mails und Malvertising-Attacken um satte 250 Prozent zu. Und: Vor allem Anwender in hochgefährdeten Branchen fallen laut Cisco doppelt so häufig auf betrügerische Links und Adware herein.
Learn more:
- https://gustmees.wordpress.com/2012/10/11/learning-basics-of-cyber-security-by-easy-to-follow-steps/
- https://gustmees.wordpress.com/2012/11/29/cyber-hygiene-ict-hygiene-for-population-education-and-business/
- https://gustmees.wordpress.com/2014/11/18/why-cybersecurity-starts-at-home-and-is-concerning-all-of-us/