The latest figures from the APWG show a decline in phishing reports. Verizon, on the other hand, implies that almost all incidents of cyber espionage reported in the last year included some phishing...
An academic study into human susceptibility to phishing has found that 92% of people misclassify phishing emails, despite efforts to educate people about the dangers.
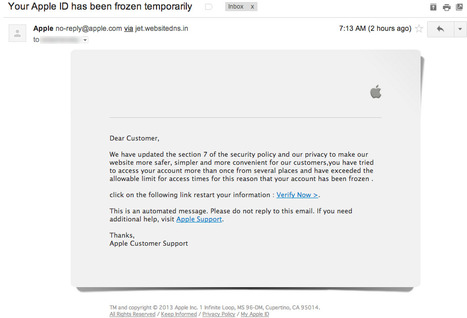
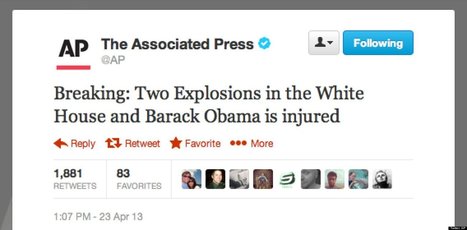
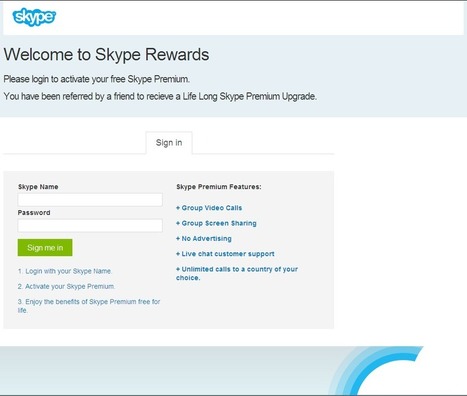
Educating users to keep a wary eye out for phishing attempts has been a major focus for security admins and providers, but it seems like the bad guys are managing to keep ahead of the curve.



 Your new post is loading...
Your new post is loading...












![L'hameçonnage : combien de personnes en sont victimes? [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/OXS9mYQx_J1s-8GXqYb4Gjl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)

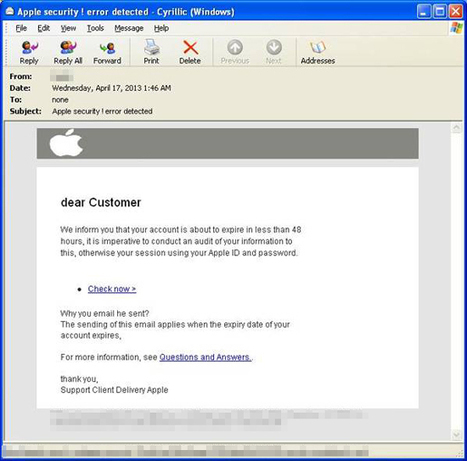









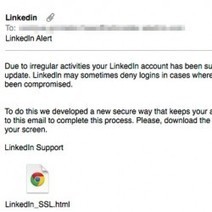
L'éditeur de sécurité Symantec a lancé une alerte à propos de mails de phishing ciblant les utilisateurs du réseau social LinkedIn. Ce mail frauduleux contient une pièce jointe à ne surtout pas ouvrir.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Phishing