 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
What about malware on Linux?
Here's how the argument might go if you were to ask that question:
Malware is impossible on Linux because Linux is secure by design, unlike Windows.
Even if Linux malware were possible, users would have to agree to run it, so that wouldn't count.
Even if users agreed to run it, they wouldn't be root, so that wouldn't count.
Even if they were root, who cares? There isn't any malware for Linux, so there.
The simple truth, of course, is that Linux is much more similar to Windows – in design, implementation and real-world security – than it is different.
As a result: there is malware for Linux; it can do plenty of harm even if you aren't root; and it may be able to infect without you realising.
Just like on Windows.
For all that, the "malware scene" on Linux simply never unfolded like it did on Windows, because the vast
Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
The Jellyfish proof-of-concept rootkit uses the processing power of graphics cards and runs in their dedicated memory
A team of developers has created a rootkit for Linux systems that uses the processing power and memory of graphics cards instead of CPUs in order to remain hidden.
The rootkit, called Jellyfish, is a proof of concept designed to demonstrate that completely running malware on GPUs (graphics processing units) is a viable option. This is possible because dedicated graphics cards have their own processors and RAM.
Such threats could be more sinister than traditional malware programs, according to the Jellyfish developers. For one, there are no tools to analyze GPU malware, they said.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
A malware program designed for Linux systems, including embedded devices with ARM architecture, uses a sophisticated kernel rootkit that’s custom built for each infection.
The malware, known as XOR.DDoS, was first spotted in September by security research outfit Malware Must Die. However, it has since evolved and new versions were seen in the wild as recently as Jan. 20, according to a new report Thursday from security firm FireEye, which analyzed the threat in detail.
XOR.DDoS is installed on targeted systems via SSH (Secure Shell) brute-force attacks launched primarily from Internet Protocol (IP) addresses registered to a Hong Kong-based company called Hee Thai Limited.
The attacks attempt to guess the password for the root account by using different dictionary-based techniques and password lists from past data breaches. FireEye observed well over 20,000 SSH login attempts per targeted server within a 24-hour period and more than 1 million per server between mid-November and end of January.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Backdoor tied to espionage campaign that has targeted governments in 45 countries.
Researchers have uncovered an extremely stealthy trojan for Linux systems that attackers have been using to siphon sensitive data from governments and pharmaceutical companies around the world. The previously undiscovered malware represents a missing puzzle piece tied to "Turla," a so-called advanced persistent threat (APT) disclosed in August by Kaspersky Lab and Symantec. For at least four years, the campaign targeted government institutions, embassies, military, education, research, and pharmaceutical companies in more than 45 countries. The unknown attackers—who are probably backed by a nation-state, according to Symantec—were known to have infected several hundred Windows-based computers by exploiting a variety of vulnerabilities, at least two of which were zero-day bugs. The malware was notable for its use of a rootkit that made it extremely hard to detect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
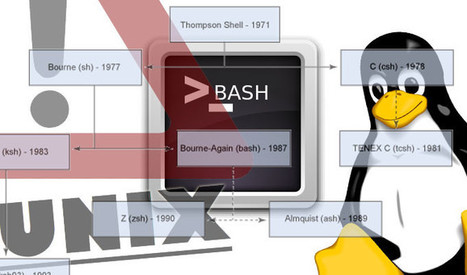
A critical vulnerability in the Bourne again shell, simply known as Bash and which is present in most Linux and UNIX distributions and Apple’s Mac OS X, has been discovered and administrators are being urged to patch immediately.
The flaw allows an attacker to remotely attach a malicious executable to a variable that is executed when Bash is invoked.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Bash+Command+Flaw

|
Scooped by
Gust MEES
|
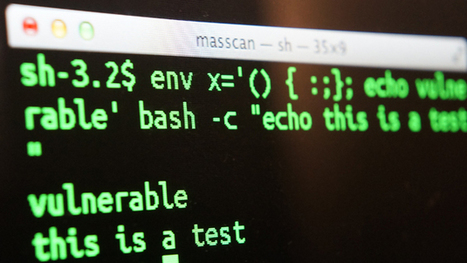
Security researchers have found the first malware using the new Bash bug.
Security researchers have found proof of concept code that attempts to exploit the serious bug discovered this week in Bourne-Again Shell, also known as Bash, which according to US CERT affects both Linux and Mac OS X.
The good news yesterday that some Linux distributions shipped patches for the bug yesterday has already been tempered by the discovery that those patches only partially dealt with potential attacks. In an update overnight, Red Hatsaid that it was developing a new patch, however, it is still advising users to apply the incomplete one for now. At the same time as security experts have been racing to develop fixes for the bug and patch systems, it appears hackers have been working on tools to attack vulnerable systems.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Bash+Command+Flaw

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A Pakistani hacker named ‘H4x0r HuSsY’ has successfully compromised the official Forum of the popular Linux OS openSUSE accessing to the database.
Via GianniPintonello

|
Scooped by
Gust MEES
|
Symantec has discovered a new Linux worm that appears to be engineered to target the “Internet of things”. The worm is capable of attacking a range of small, Internet-enabled devices in addition to traditional computers.

|
Scooped by
Gust MEES
|
During an investigation into how a breach occurred at a large internet hosting provider, researchers found a Linux backdoor capable of stealing login credentials from secure shell connections.
===> The Fokirtor Trojan targets users of the Linux operating system. <===

|
Scooped by
Gust MEES
|
Ubuntu Forums has been hacked.
As well as leaving behind an AK-waving penguin, the hackers also took away millions of usernames, email addresses and password hashes.
|

|
Scooped by
Gust MEES
|
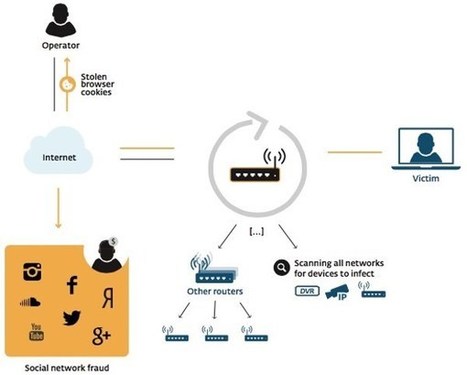
ESET researchers have issued a technical paper today, analysing a new worm that is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The malware, dubbed Linux/Moose by researchers Olivier Bilodeau and Thomas Dupuy, infects Linux-based routers and other Linux-based devices, eradicating existing malware infections it might find competing for the router’s limited resources, and automatically finding other routers to infect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Router

|
Scooped by
Gust MEES
|
Security researchers with Russian anti-virus company Doctor Web have examined a complex, multi-purpose backdoor for Linux. This malicious program can execute various commands issued by intruders such as to mount DDoS attacks and to perform a wide range of other malicious tasks.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Mitarbeiter des russischen Security-Software-Anbieters Doctor Web haben einen Linux-Trojaner entdeckt, der Denial-of-Service-Attacken in größerem Ausmaß starten kann. Den Schädling benannten sie mit Linux.BackDoor.Fgt.1.
Sobald er auf einem befallenen Gerät startet, prüft er erst einmal, ob es eine Internetverbindung gibt, indem er auf einen der Google-Server zugreift. Findet er keine, bleibt er ruhig, um nicht von verhaltensbasierenden Systemen erkannt zu werden. Ist die Verbindung erfolgreich, erfasst die Malware IP- und MAC-Adresse des infizierten Systems. Danach versucht sie, diese Informationen und Daten über die eigene Version an einen Steuer-Server zu senden.
Schließlich wartet Linux.BackDoor.Fgt.1 auf einen Datenblock, der einen auszuführenden Befehl enthält. Wenn vom Verwaltungsserver ein Ping-Befehl eintrifft, antwortet der Trojaner mit Pong und fährt mit seiner Mission fort. Beim Befehl DUP schließt er seine Arbeit ab.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
This GnuTLS bug is worse than the big Apple "goto fail" bug patched last week.

|
Scooped by
Gust MEES
|
A blended DDoS botnet consisting of both Windows and Linux machines has been detected by researchers working with the Polish CERT.
The botnet is exclusively dedicated to mounting DDoS attacks, mainly DNS amplification attacks.

|
Scooped by
Gust MEES
|
Le ver Java.Tomdep a été spécialement créé pour cibler les serveurs Tomcat et infecte déjà une dizaine de pays.

|
Scooped by
Gust MEES
|
In May of this year, sophisticated attackers breached a large Internet hosting provider and gained access to internal administrative systems. The attackers appear to have been after customer record information such as usernames, emails, and passwords.
While these internal administrative systems had access to customer records, discovery of the attack and certain security implementations mitigated the scope of the breach. Customer passwords were accessible, but these passwords were hashed and salted making mass password cracking difficult. Customer financial information was also accessible, but encrypted. Unfortunately, access to the encryption key cannot be ruled out.
While breaches of organizations and mass customer record dumps are posted almost daily, this particular attack was more sophisticated than we have seen in the past.
|



 Your new post is loading...
Your new post is loading...
















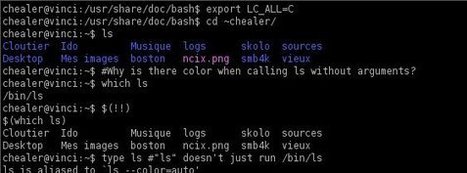
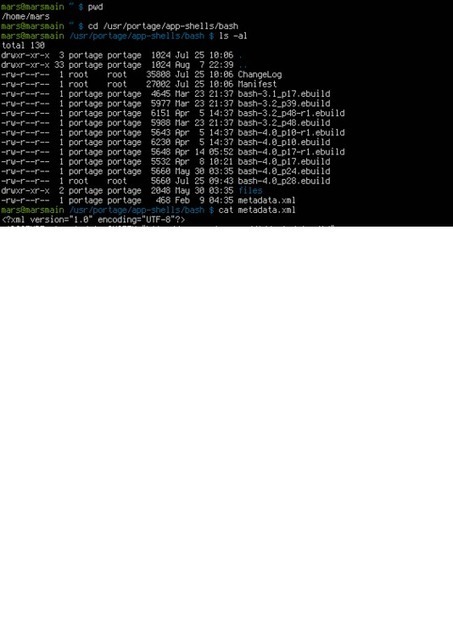
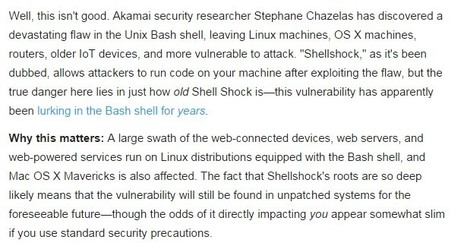








Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux