"Black-box" testing uncovers several ways the NSA could tap the popular service.
As Soghoian and other critics admit, the end-to-end encryption included with iMessage may make it impossible for Apple to decrypt conversations, at least in some circumstances. But in the absence of key details that Apple has steadfastly declined to provide, customers who are especially concerned about their privacy would do well to assume otherwise.
Via Gust MEES



 Your new post is loading...
Your new post is loading...

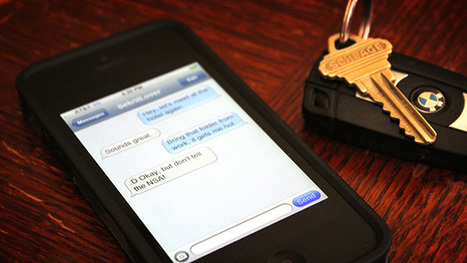






















As Soghoian and other critics admit, the end-to-end encryption included with iMessage may make it impossible for Apple to decrypt conversations, at least in some circumstances. But in the absence of key details that Apple has steadfastly declined to provide, customers who are especially concerned about their privacy would do well to assume otherwise.
===> Nobody Is Perfect!!! <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
As Soghoian and other critics admit, the end-to-end encryption included with iMessage may make it impossible for Apple to decrypt conversations, at least in some circumstances. But in the absence of key details that Apple has steadfastly declined to provide, customers who are especially concerned about their privacy would do well to assume otherwise.
===> Nobody Is Perfect!!! <===
Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security