 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Anwender von Dropbox, OneDrive & Co. sollten angesichts konkreter Bedrohungen diese Nutzung überdenken.
Missbrauch von Zugriffsschlüsseln Der so genannte "Man in the cloud"-Angriff wurde auf der BlackHat-Konferenz in Las Vegas im August detailliert dargestellt. Sicherheitsexperten von Imperva belegten hierbei die Bedrohung über eine Vielzahl von Diensten (OneDrive, Google Drive, Box undDropbox) hinweg. Die nachgewiesene Lücke beruht insbesondere auf der konzeptionellen Ermöglichung eines bequemen und transparenten Einsatzes des Synchronisations- und Speicherdienstes. Die kontinuierliche Nutzung eines Programmes, das mit dem jeweiligen Serverdienst kommunizieren kann, setzt die einmalige Authentifizierung und Autorisierung des jeweiligen Programmes und der sie ausführenden Instanz voraus. Dies kann über proprietäre Protokolle erfolgen oder über das mittlerweile weitverbreitete OAuth2 -Verfahren. Hat sich der Anwender gegenüber den Dienst erfolgreich authentifiziert und der Nutzung durch das jeweilige Programm zugestimmt, das durchaus auch der native Client zur Synchronisation sein kann, erhält die Applikation einen dauerhaften nutzbaren,wieder verwendbaren Access Token . Mit diesem weist sich das jeweilige Programm in Zukunft gegenüber dem Dienst aus. Ein erneutes Login durch den Anwender ist üblicherweise nicht mehr notwendig, der Token wird hierfür lokal gespeichert und kontinuierlich wiederverwendet. Selbst ein Passwortwechsel erfordert üblicherweise nicht die Erneuerung des Tokens, da dieser nach Erstellung unabhängig von dem Passwort agiert.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Just days after Microsoft released its latest operating system, hackers have begun targeting soon-to-be Windows 10 users with an emerging kind of malware.
Cisco security researchers are warning users against opening email attachments purporting to be from the software giant. The "ransomware" malware, which encrypts files until a ransom is paid, is being sent as part of an email spam campaign.
Stop trying to control everything. Learners know best.
The learners know more than you do about what learning experiences are right for them. I don’t think we should necessarily build our own versions of YouTube, Pinterest, Twitter etc either, we just need to be the champions of these tools for learning. In someways, L&D’s job should be much easier than we’re making it and in other ways, with the entrenched spoon-feeding learners have come to expect from corporate training, it’s much harder then it seems. What I’d hope you take away from this post is that there is a new way, and it’s your job (if you work in learning) to explain this to decision-makers who don’t know any better. . Learn more: . .
Via juandoming

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
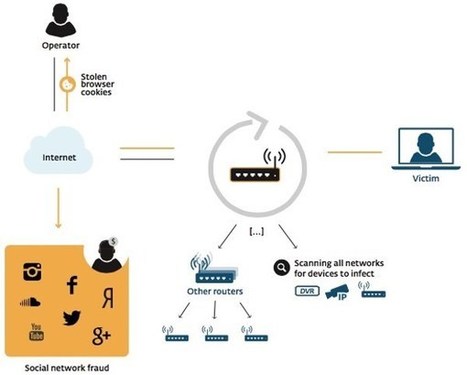
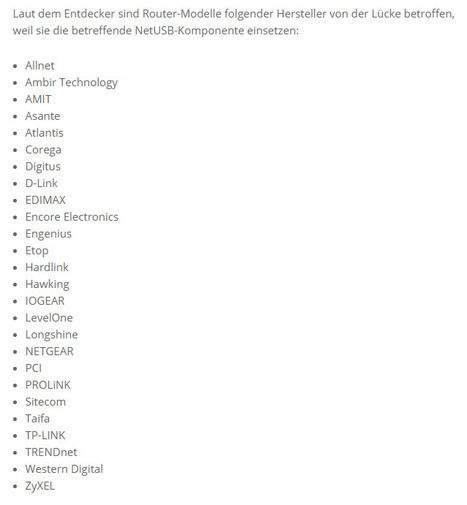
ESET researchers have issued a technical paper today, analysing a new worm that is infecting routers in order to commit social networking fraud, hijacking victims’ internet connections in order to “like” posts and pages, “view” videos and “follow” other accounts.
The malware, dubbed Linux/Moose by researchers Olivier Bilodeau and Thomas Dupuy, infects Linux-based routers and other Linux-based devices, eradicating existing malware infections it might find competing for the router’s limited resources, and automatically finding other routers to infect.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Router
The Simda botnet, believed to have infected more than 770,000 computers worldwide, has been targeted in a global operation.
In a series of simultaneous actions around the world, on Thursday 9 April, 10 command and control servers were seized in the Netherlands, with additional servers taken down in the US, Russia, Luxembourg and Poland.
The operation involved officers from the Dutch National High Tech Crime Unit (NHTCU) in the Netherlands, the Federal Bureau of Investigation (FBI) in the US, the Police Grand-Ducale Section Nouvelles Technologies in Luxembourg, and the Russian Ministry of the Interior’s Cybercrime Department “K” supported by the INTERPOL National Central Bureau in Moscow.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Botnet

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Lenovo simply can't catch a break. After the massive negative attention it received for their ill-advised decision to ship some of its notebooks with pre-installed adware that also uses MITM SSL certificates, for a short time on Wednesday their main domain - Lenovo.com - has been hijacked and effectively defaced by the hacker collective Lizard Squad.
The defaced page showed a slideshow of photos of two youngsters - according to Brian Krebs, they are Ryan King (aka “Starfall”) and Rory Andrew Godfrey (“KMS”), two former members of the hacker collective Hack The Planet - accompanied with music. The reason for the defacement is purportedly Lenovo's Superfish blunder.
The defaced page pointed to Lizard Squad's Twitter feed and served as an advertisement for its LizardStresser DoS service.
The hackers didn't compromise Lenovo's servers. Instead, they (apparently) compromised those of Web Commerce Communications (Webnic.cc), a popular Malaysia-based Internet registrar with whom the Lenovo domain is registered.
Learn more:
- http://www.scoop.it/t/21st-century-learning-and-teaching/?tag=LENOVO
- http://www.scoop.it/t/securite-pc-et-internet/?tag=LENOVO

|
Scooped by
Gust MEES
|
This report was prepared by INSS and CSFI to create better cyber situational awareness of the nature and scope of threats to national security worldwide in the domains of cyberspace and open source intelligence. It is provided to Federal, State, Local, Tribal, Territorial and private sector officials to aid in the identification and development of appropriate actions, priorities and follow-up measures.
|

|
Scooped by
Gust MEES
|
Intel has fixed a major security vulnerability in a driver utility tool that could allow an attacker to remotely install malware.
The company has advised those who use the Intel Driver Update Utility to download an updated version of the software, which mitigates a vulnerability in how the software requests new drivers from Intel's servers.
In a security advisory, the chipmaker confirmed that versions 2.0 to 2.3 put PCs at risk because they check Intel's servers over an unencrypted connection. An attacker could conduct a man-in-the-middle on the affected software. which could trick the software into downloading malware or other malicious files.

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
LinuxCon 2015 Security guru Bruce Schneier says there's a kind of cold war now being waged in cyberspace, only the trouble is we don't always know who we're waging it against.
Schneier appeared onscreen via Google Hangouts at the LinuxCon/CloudOpen/Containercon conference in Seattle on Tuesday to warn attendees that the modern security landscape is becoming increasingly complex and dangerous.
"We know, on the internet today, that attackers have the advantage," Schneier said. "A sufficiently funded, skilled, motivated adversary will get in. And we have figure out how to deal with that."
Using the example of last November's crippling online attack against Sony Pictures, Schneier said it was clear that many of these new attacks were the work of well-funded nation-states.
"Many of us, including myself, were skeptical for several months. By now it does seem obvious that it was North Korea, as amazing as that sounds," he said.
But what's troubling about many of these new attacks, he added, is that they can be hard to spot when they don't come in the form that security experts typically expect.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Cyberattack
http://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
What about malware on Linux?
Here's how the argument might go if you were to ask that question:
Malware is impossible on Linux because Linux is secure by design, unlike Windows.
Even if Linux malware were possible, users would have to agree to run it, so that wouldn't count.
Even if users agreed to run it, they wouldn't be root, so that wouldn't count.
Even if they were root, who cares? There isn't any malware for Linux, so there.
The simple truth, of course, is that Linux is much more similar to Windows – in design, implementation and real-world security – than it is different.
As a result: there is malware for Linux; it can do plenty of harm even if you aren't root; and it may be able to infect without you realising.
Just like on Windows.
For all that, the "malware scene" on Linux simply never unfolded like it did on Windows, because the vast
Learn more:
http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
Often times it's not the fact that your business has been hacked that will lose your customers' confidence, but the way your company responds.
Kaspersky isn't the first anti-virus company to have suffered at the hands of hackers, and it certainly won't be the last. And it shows that even the most security-conscious organisations can fall victim to determined hackers.
The truth is that most companies have probably been hacked to some extent or another - although most of the time they won't have been specifically targeted like Kaspersky probably was.
What's important is for companies to consider testing their own defences, and put effort into hacking themselves, finding vulnerabilities and weaknesses *before* the bad guys strike.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security

|
Scooped by
Gust MEES
|
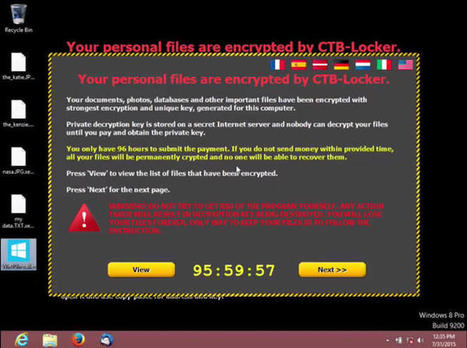
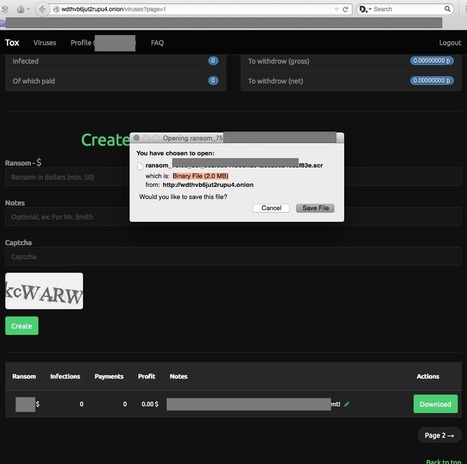
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
Die Einstiegshürde für angehende Online-Erpresser ist erneut gesunken: Ein Dienst im Tor-Netz erstellt nach wenigen Klicks den individuellen Erpressungs-Trojaner. Falls ein Opfer das geforderte Lösegeld zahlt, verdienen die Betreiber mit.
- http://www.scoop.it/t/securite-pc-et-internet/?tag=TOR

|
Scooped by
Gust MEES
|
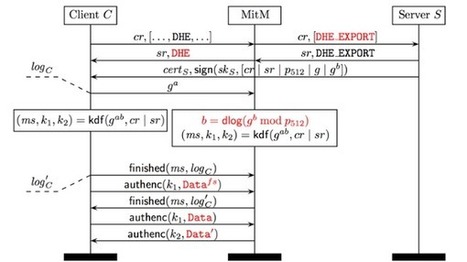
Unzählige Web-, Mail-, SSH- und VPN-Server sind durch einen neuen Angriff auf den Diffie-Hellmann-Schlüsseltausch verwundbar. Angreifer können so die Verschlüsselung aufbrechen. Vermeintlich vertrauenswürdig übertragene Daten wären dann nicht mehr sicher.

|
Scooped by
Gust MEES
|
The Jellyfish proof-of-concept rootkit uses the processing power of graphics cards and runs in their dedicated memory
A team of developers has created a rootkit for Linux systems that uses the processing power and memory of graphics cards instead of CPUs in order to remain hidden.
The rootkit, called Jellyfish, is a proof of concept designed to demonstrate that completely running malware on GPUs (graphics processing units) is a viable option. This is possible because dedicated graphics cards have their own processors and RAM.
Such threats could be more sinister than traditional malware programs, according to the Jellyfish developers. For one, there are no tools to analyze GPU malware, they said.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux

|
Scooped by
Gust MEES
|
Ein Rootkit, das unabhängig vom Betriebssystem operiert, sämtlichen Speicher auslesen kann und durch den Tausch der Festplatte im System nicht gestoppt wird – was klingt wie eine IT-Gruselgeschichte haben zwei Forscher nun öffentlich präsentiert.

|
Scooped by
Gust MEES
|
Die Bürgerrechtsorganisation American Civil Liberties Union (ACLU) hat im Namen der Wikimedia Foundation und weiteren US-Organisationen Klage gegen die NSA eingereicht. Die Bürgerrechtler bezweifeln, dass die massenhafte Speicherung von Kommunikationsdaten verfassungskonform ist.

|
Scooped by
Gust MEES
|
3 million strong RAMNIT botnet taken down
Posted on 25.02.2015
The National Crime Agency’s National Cyber Crime Unit (NCCU) worked with law enforcement colleagues in the Netherlands, Italy and Germany, co-ordinated through Europol’s European Cybercrime Centre (EC3), to shut down command and control servers used by the RAMNIT botnet.
RAMNIT spread malware via seemingly trustworthy links sent out on phishing emails or social networking websites. If users running Windows clicked on the links, the malware would be installed, infecting the computer. Infected computers would then be under the control of criminals, enabling them to access personal or banking information, steal passwords and disable antivirus protection.
Investigators believe that RAMNIT may have infected over three million computers worldwide, with around 33,000 of those being in the UK. It has so far largely been used to attempt to take money from bank accounts. Analysis is now taking place on the servers and an investigation is ongoing.
|



 Your new post is loading...
Your new post is loading...



























Dieses Dokument stellt neben einer kurzen Darstellung der Bedrohungslage konkrete Hilfen für die Prävention und die Reaktion im Schadensfall bereit.
Learn more / En savoir plus / Mehr erfahren:
http://www.scoop.it/t/ict-security-tools/?tag=Ransomware