Fiches de sécurité informatique
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login

ICT Security-Sécurité PC et Internet
87.1K views |
+0 today
Follow
| Tags |
|---|
ICT Security + Privacy + Piracy + Data Protection - Censorship - Des cours et infos gratuites sur la"Sécurité PC et Internet" pour usage non-commercial... (FR, EN+DE)...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...
Military to gain a new range of offensive options to defend critical installations around the country from cyber attacks...
Apple’s security reality is changing right before our eyes and the company’s response will be telling.
WHY (SHOULD I BE WORRIED)?
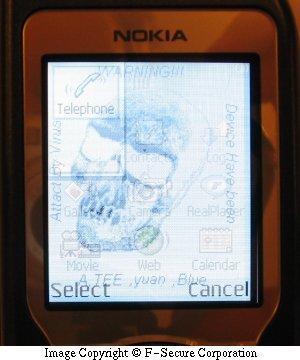
Worm:iOS/Ikee.A changed the phone's wallpaper Last week I gave a brief summary of the kinds of threats a user might encounter on the smartphones of today. This week’s article is supposed to cover the reasons why a user would worry about mobile malware, so let me give the short answer now: Usually, mobile malware attacks are motivated by: Bragging rights; money; stealing personal information that can be sold for money. For the user that gets hit by the malware, it means: Losing control over your phone; losing your money; someone else might be using your personal details for who-knows-what.
Apple finally responded to the Mac Defender outbreak, with a technical note containing removal instructions and the promise of a removal tool.
Un chercheur italien a démontré comment dérober à distance des informations de connexion stockées dans des cookies par IE. La technique est complexe et n’inquiète pas Microsoft, à ce stade.
Die neueste Version des mobilen Betriebssystems iOS schließt eine kritische Sicherheitslücke und deaktiviert den Jailbreak auf iPhone, iPad und iPod Touch.
Yes, I realize that’s an ambitious title for a blog post about staying secure online, but there are a handful of basic security principles that — if followed religiously — can blunt the majority of malicious threats out there today.
I can’t believe that we’re still having a discussion over whether or not the bad guys have begun targeting Mac users. I’ve one word to describe these people who choose to ignore the real problems facing the modern Mac user and instead choose to live in the past - Dinosaurs.
Times have changed. The old-guard, fervor-filled dinosaurs of the past who for some reason (ego, self esteem, ignorance …) want to frantically and fanatically cheer lead have been replaced by the modern Mac user who sees the Mac as a tool rather than an idol. What is a modern Mac user? Well, for starters I see them as someone who started using a Mac since its transition from the PowerPC architecture to Intel architecture, a move which began in mid-2006. Much of the zealotry and nonsense spouted today dates back to the PowerPC years when owning a Mac was seen by many as a deviant pastime. Times have changed. The modern Mac user also uses their machine in a very different way to the dinosaurs of old. People nowadays surf a lot more, social media has in many ways replaced email as the preferred method of communication. Multimedia on the web has exploded. More people doing more things in ways that we couldn’t really have dreamed possible a decade ago.
« Hacker » est un terme utilisé depuis des années pour désigner de nombreuses personnes et qui est assez bien accepté comme nom générique pour les (...)...
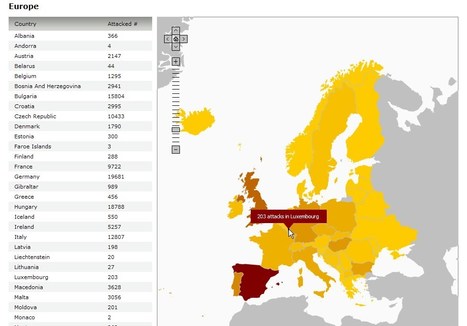
L'insécurité sur Internet, les ordinateurs (PC et Mac) et les smartphones (exemples STUXNET et ZEUS) progresse tellement vite...
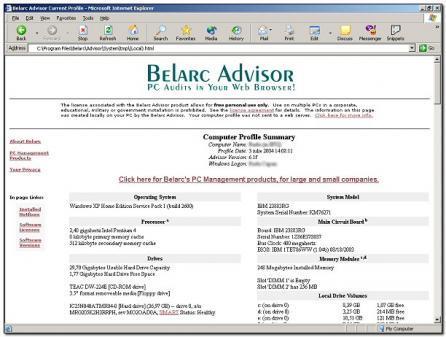
Secure your PC by easy to follow steps. A knol about a series of Knol-Tutorials who will show you how to secure your PC and...
|
From late 2010 to the first few months of 2011, there’s been a fair bit of buzz in the tech media about how mobile malware may be the big IT security issue for 2011. (To be fair, I also said something similar in a previous post.)
Even though PC threats are still hugely more prevalent, mobile malware tends to get more press because they’re like the up-and-coming starlets of tech threats – they’re fresh, new, interesting, and frankly, just a little sexier than plain ol’ Windows malware.
This is the third and final article in this series on mobile malware.
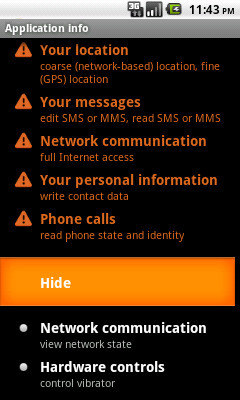
HOW (CAN I PROTECT MYSELF)? Permissions request list from Trojan:Android/AdSMS In my previous articles, I’ve covered what kind of mobile threats have emerged in the first half of 2011 and why these malicious programs may cause concern for smartphone users. Now, let’s assume you’re a cautious smartphone user who wants to make sure you don’t get hit by a malware infection on your smartphone. What can you do?
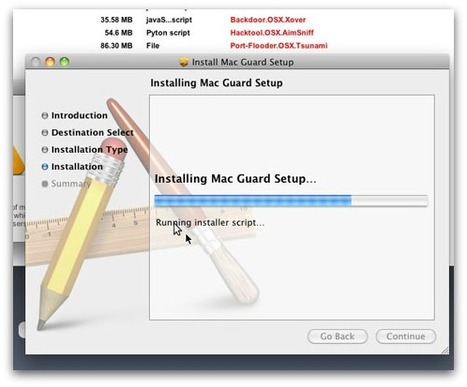
A new variant of the fake security software for OS X was discovered today and it no longer requires administrators to enter their passwords. We take a brief look at the advancement of malware on the Mac over the last month.
SECURITE - Apple publie un guide pour se débarrasser du malware Mac Defender, en attendant une mise à jour de son OS...
Apple will deliver a Mac OS X update “in coming days” that will put its Mac Defender malware headaches to rest...
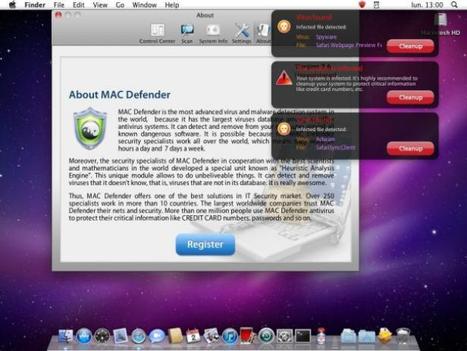
A recent phishing scam has targeted Mac users by redirecting them from legitimate websites to fake websites which tell them that their computer is infected with a virus. The user is then offered Mac Defender "anti-virus" software to solve the issue.
This “anti-virus” software is malware (i.e. malicious software). Its ultimate goal is to get the user's credit card information which may be used for fraudulent purposes. The most common names for this malware are MacDefender, MacProtector and MacSecurity. In the coming days, Apple will deliver a Mac OS X software update that will automatically find and remove Mac Defender malware and its known variants. The update will also help protect users by providing an explicit warning if they download this malware. In the meantime, the Resolution section below provides step-by-step instructions on how to avoid or manually remove this malware.
From
ask-leo
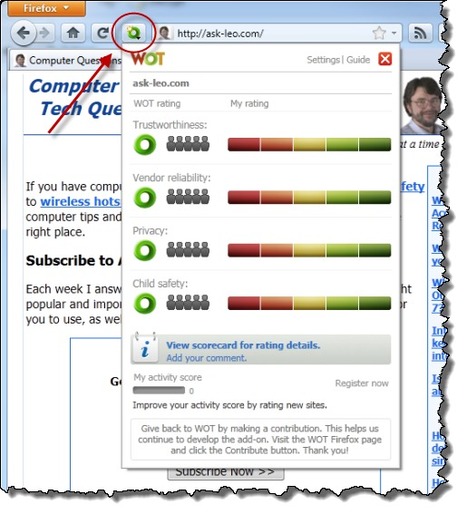
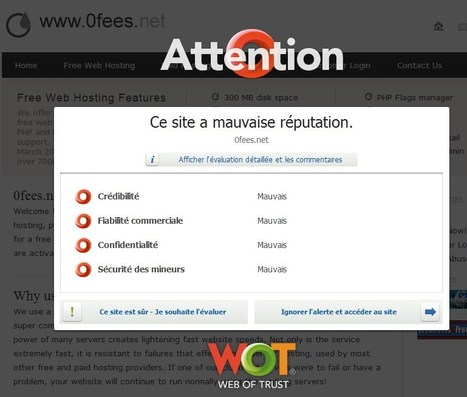
WOT relies on a "crowdsourced" model of information gathering. What that means is that registered WOT members provide ratings of websites based on four criteria: Trustworthiness, Vendor reliability, Privacy and Child Safety. Members rate sites that they actually visit and interact with.
Much like a rating system that you might find in an online store or other votable venue, sites accumulate a reputation based on how people vote. Those ratings are then made available to anyone.
From
www
This isn’t about Mac-versus-Windows. It’s about engineering and (shady) economics.
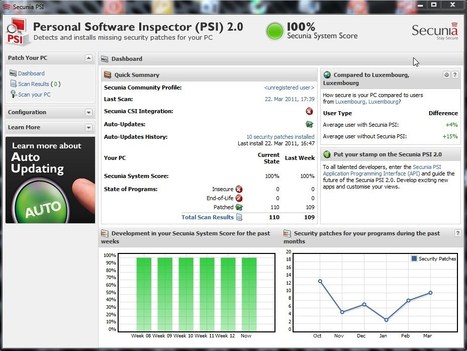
Un antivirus et un pare-feu ne suffisent plus, disons le clairement. Proposition d'une liste de logiciels spéciaux qui...
|