 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
A dangerous Drupal flaw could leave your site completely compromised if you don't patch the flaw immediately.
Developers of popular open-source CMS Drupal are warning admins to immediately patch a flaw that an attacker can exploit just by visiting a vulnerable site.
The bug affects all sites running on Drupal 8, Drupal 7, and Drupal 6. Drupal's project usage page indicates that about a million sites are running the affected versions.
Admins are being urged to immediately update to Drupal 7.58 or Drupal 8.5.1. Drupal issued an alert for the patch last week warning admins to allocate time for patching because exploits might arrive "within hours or days" of its security release. So far, there haven't been any attacks using the flaw, according to Drupal.
The bug, which is being called Drupalgeddon2, has been assigned the official identifier CVE-2018-7600.
Drupal has given it a 'highly critical' rating with a risk score of 21 out of 25 under the NIST Common Misuse Scoring System.
Although there are no security releases for the unsupported Drupal 8.3.x and 8.4.x, Drupal has released patches for quick remediation. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Drupal

|
Scooped by
Gust MEES
|
Monero-mining Android malware will exhaust your phone in its quest for cash.
A new strain of Android malware will continuously use an infected device's CPU to mine the Monero cryptocurrency until the device is exhausted or even breaks down.
Security company Trend Micro has named the malware HiddenMiner because of the techniques it uses to protect itself from discovery and removal.
Like most cryptocurrency-mining software, HiddenMiner uses the device's CPU power to mine Monero. But Trend Micro said that because there is no switch, controller, or optimizer in HiddenMiner's code it will continuously mine Monero until the device's resources are exhausted.
"Given HiddenMiner's nature, it could cause the affected device to overheat and potentially fail," the company said. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=Crypto+Mining https://www.scoop.it/t/securite-pc-et-internet/?&tag=Android

|
Scooped by
Gust MEES
|
Ein Sicherheitsforscher warnt erneut: In Firefox und Thunderbird gespeicherte Passwörter sind nicht effektiv vor Datendiebstahl geschützt.
Angreifer könnten mit vergleichsweise wenig Aufwand das Master-Kennwort des Passwort-Tresors in Mozillas Firefox und Thunderbird erraten. Wer das kennt, kann die im Mail-Client und Webbrowser gespeicherten Passwörter für Onlinedienste im Klartext einsehen.
Davor warnt nun erneut ein Sicherheitsforscher. Bereits vor neun Jahren gab es Hinweise auf diesen Missstand. Daran hat sich offensichtlich bis jetzt nichts geändert.
Schutz knackbar
Die beiden Anwendungen schützen das Master-Passwort zwar, dafür kommt jedoch das längst als geknackt geltende Hash-Verfahren SHA-1 zum Einsatz. Eine Zufallszahl (Salt) verfremdet den Hash, damit gleiche Passwörter nicht den gleichen Hash bekommen. Das erschwert ein Erraten. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Firefox... https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Facebook appears to be getting tougher on people who break its rules.
Hot on the heels of banning the Britain First group from its network, Facebook has announced it has suspended political data analytics firm Cambridge Analytica, and its parent company Strategic Communication Laboratories (SCL).
But the reason for the organisations being blocked from Facebook are very different. Britain First is accused of spreading vile hateful messages about Muslims, but Cambridge Analytica is accused of acquiring the data of more than 50 million Facebook users via an illegitimate route.
Cambridge Analytica is the shady data analytics firm that specialises in “psychographic” profiling. In short, they scoop up data online and use it to create personality profiles for voters.
That knowledge could be extremely useful, as individuals can then be targeted with content targeted to appeal to them, and perhaps influence their behaviour. Maybe even change their likelihood to vote in a particular direction.
Cambridge Analytica is widely credited for helping Donald Trump’s successful campaign on social media to be elected President of the United States. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Big+Data https://www.scoop.it/t/securite-pc-et-internet/?&tag=Ethics

|
Scooped by
Gust MEES
|
Samuel Groß et Richard Zhu se sont distingués durant la première journée du Pwn2Own 2018. Samuel Groß a exploité une faille de Safari permettant une élévation de privilèges pour écrire son nom sur la barre tactile d'un MacBook Pro. Il a reçu 65 000 $ en guise de récompense et six points pour le titre tant convoité de Master of Pwn. De son côté, Richard Zhu a quant à lui contourné les défenses de Microsoft Edge en utilisant deux vulnérabilités de type use-after-free et un dépassement d'entier dans le noyau. Il a gagné 70 000 $ et 7 points supplémentaires dans la course au titre de Maître. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pwn20wn

|
Scooped by
Gust MEES
|
In today’s day and age, when you ask a security expert about some basic tips to stay safe on the web, one of the most important things he will probably tell you is to download software only from legitimate sources. Sometimes even such a basic and obvious advice might not save you from malware encounters. We found three trojanized applications hosted on download.cnet.com, which is one of the most popular software hosting sites in the world as its Alexa rank (163th) shows. Learn more / en savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Malware

|
Scooped by
Gust MEES
|
Password manager maker Keeper hit by another security snafu
The exposed server contained the company's downloadable software -- including a code-signing certificate.
Keeper, an embattled password manager maker currently suing a news reporter for defamation, left a server hosting the company's installer files exposed with full permissions, allowing anyone to access and replace files with malicious content, a security researcher told ZDNet.
Chris Vickery, who found the exposed server, immediately notified ZDNet of the exposure. We reached out to Keeper by phone and email on Friday. Within an hour of disclosure, the server had been secured. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Password+Managers https://www.scoop.it/t/securite-pc-et-internet/?&tag=Passwords

|
Scooped by
Gust MEES
|
BUNDESHACK:
Hack auf Bundesregierung erfolgte über Lernplattform Ilias
Die Bundesregierung wurde über die Lernplattform Ilias gehackt, die an der Hochschule des Bundes zu Weiterbildungszwecken genutzt wird. Die Einrichtung nutzte eine alte Version mit zahlreichen Sicherheitslücken.
Eine Exklusivmeldung von Hauke Gierow und Hanno Böck
Unter lernplattform-bakoev.bund.de können Mitarbeiter des Bundes Weiterbildungsangebote der Bundesakademie für Öffentliche Verwaltung wahrnehmen - eigentlich. Denn die von der Hochschule des Bundes betriebene Webseite ist derzeit nicht erreichbar. Wer sie besuchen will, bekommt nur die Fehlermeldung: "Die Lernplattform Ilias ist zurzeit nicht erreichbar. Sie wurde auf Empfehlung des BSI vorsorglich vom Netz genommen." Über diese Plattform soll der Hack auf die Bundesregierung abgelaufen sein. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
As location-aware advertising goes mainstream—like that Jack in the Box ad that appears whenever you get near one, in whichever app you have open at the time—and as popular apps harvest your lucrative location data, the potential for leaking or exploiting this data has never been higher.
It’s true that your smartphone’s location-tracking capabilities can be helpful, whether it’s alerting you to traffic or inclement weather. That utility is why so many of us are giving away a great deal more location data than we probably realize. Every time you say “yes” to an app that asks to know your location, you are also potentially authorizing that app to sell your data.
Dozens of companies track location and/or serve ads based on this data. They aim to compile a complete record of where everyone in America spends their time, in order to chop those histories into market segments to sell to corporate advertisers.
Marketers spent $16 billion on location-targeted ads served to mobile devices like smartphones and tablets in 2017. That’s 40% of all mobile ad spending, research firm BIA/Kelsey estimates, and it expects spending on these ads to double by 2021.
The data required to serve you any single ad may pass through many companies’ systems in milliseconds—from data broker to ad marketplace to an agency’s custom system. In part, this is just how online advertising works, where massive marketplaces hold ongoing high-speed auctions for ad space. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=tracking https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://gustmees.wordpress.com/2014/03/05/often-asked-questions-are-there-cyber-security-dangers-with-apps-and-whats-about-privacy/

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
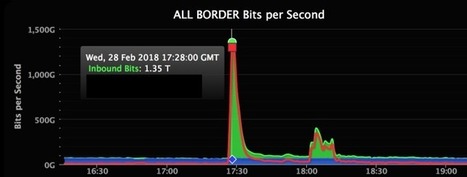
GitHub has revealed it was hit with what may be the largest-ever distributed denial of service (DDoS) attack.
The first portion of the attack against the developer platform peaked at 1.35Tbps, and there was a second 400Gbps spike later. This would make it the biggest DDoS attack recorded so far. Until now, the biggest clocked in at around 1.1Tbps.
In a post on its engineering blog, the developer platform said that, on Feb. 28, GitHub.com was unavailable from 17:21 to 17:26 UTC and intermittently unavailable from 17:26 to 17:30 UTC due to the DDoS attack.
Github said that at no point "was the confidentiality or integrity of your data at risk. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Canoncinal vient d’annoncer la disponibilité de correctifs pour 26 vulnérabilités recensées dans le noyau d’Ubuntu 14.04 (Trusty Tahr). Cette version qui est sortie depuis avril 2014 bénéficie d’un support Long Term Support abrégé LTS (pour support à long terme en français) ce qui fait qu’elle est prise en charge par l’équipe de développement pendant cinq ans (pour les versions bureau et serveur), soit jusqu’en avril 2019.
Dans cette récente annonce, l’entreprise rapporte parmi les failles corrigées qu’une vulnérabilité d’écriture hors limites existait dans le système de fichiers Flash-Friendly (f2fs) du noyau Linux. Cette faille qui a été consignée sous la référence CVE-2017-0750 pourrait être exploitée par un attaquant pour construire un système de fichiers malveillant qui, lorsqu’il est monté, peut provoquer un déni de service (panne du système) ou éventuellement exécuter du code arbitraire.
À côté de cette faille, une situation de concurrence débouchant sur une faille use-after-free a été découverte dans la fonction snd_pcm_info du sous-système ALSA PCM sur le noyau Linux. Cette situation de compétition rapportée par l’équipe de sécurité d’Ubuntu pourrait être utilisée par une personne malveillante pour obtenir des privilèges non autorisés à travers des vecteurs non spécifiés et provoquer une panne du système ou éventuellement exécuter du code arbitraire. Cette faille portant le code CVE-2017-0861 a été classée à un niveau élevé de sévérité selon la version 3 de CVSS Severity. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Linux

|
Scooped by
Gust MEES
|
Der JIT-Compiler, der Microsofts Edge-Browser von Angriffscode aus dem Web isolieren soll, lässt sich selbst zum Einschleusen von Angriffscode missbrauchen. Google hat die dazugehörige Lücke nun veröffentlicht, ohne dass Microsoft Zeit zum Patchen hatte.
Um zu verhindern, dass Angreifer über den Windows-eigenen Browser Edge Schadcode ausführen können, verfügt dieser über Exploit-Schutz-Funktionen namens Code Integrity Guard (CIG) und Arbitrary Code Guard (ACG). ACG verwendet einen Just-in-Time-Compiler in einem eigenen Prozess und soll sicherstellen, dass der von CIG geladene und als vertrauenswürdig verifizierte Code nicht vor der Ausführung im Speicher modifiziert wird, um böse Dinge zu tun. ACG soll also den aus dem Web geladenen Code isolieren, damit dieser den Browser-Prozess nicht dazu missbrauchen kann, Schaden auf dem System anzurichten. Leider steckt gerade im JIT-Compiler des ACG-Schutzmechanismus eine Schwachstelle. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers
|

|
Scooped by
Gust MEES
|
Researchers say the malware is "highly efficient," even if it's not very sophisticated.
A newly-discovered keylogger malware has been found infecting computers in the wild. Though the malware is far from advanced, it's efficient at stealing passwords.
Researchers at Cybereason, a Boston, Mass.-based security firm, call the malware "Fauxpersky," as it impersonates the Russian antivirus software Kaspersky. The keylogger is built off a popular app, AutoHotKey, which lets users write small scripts for automating tasks, and compile the script into an executable file. In this case, the app was abused to build a keylogger, which spreads through USB drives and infects Windows PCs -- and replicates on the computer's listed drives.
"This malware is by no means advanced or even very stealthy," said researchers Amit Serper and Chris Black, in a detailed blog post, published Wednesday.
"However, this malware is highly efficient at infecting USB drives and exfiltrating data from the keylogger through Google directly to the attacker's mailbox," the researchers said.
That's where the malware's functionality gets interesting: Once the malware's core files are all running, everything typed on the computer is recorded into a text file with the window's name -- giving the malware author a better idea of the context to the keylogged text.
The contents of that text file is exfiltrated from the computer through a Google Form. The file is then deleted from the disk. Each form response goes directly to the malware author's email inbox.
Serper and Black reported the malicious form to Google, which took it down within an hour.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Keylogger

|
Scooped by
Gust MEES
|
Nation-state attackers are attempting to undermine trust in critical services -- so how do we go about stopping them?
While cyber-attacks focusing on stealing email or other data are still very much part of the threat landscape, some of the most advanced hacking operations are focusing on grander goals.
Some of these groups -- almost all nation-state backed -- are turning their attention to critical infrastructure including utilities firms and power plants, while others are attempting to manipulate public attitudes and even elections through the use of fake news and other social media propaganda.
"It's not so much an attack on critical infrastructure, but rather an attack on the confidence and psychology of a nation," said Chris Inglis, former deputy director of the National Security Agency, speaking at World Cyber Security Congress event in London.
Attacking critical infrastructure and spreading disinformation is a powerful combination: after all, the reason that governments exist is to make sure the citizens of a country remain safe. Such tactics have been tried out in Ukraine over the last few years. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
Palant commented: "Turns out that the corresponding NSS bug has been sitting around for the past nine years. That’s also at least how long software to crack password manager protection has been available to anybody interested.
So, is this issue so hard to address? Not really according to Palant: "NSS library implements PBKDF2 algorithm, which would slow down brute-forcing attacks considerably if used with at least 100,000 iterations. Of course, it would be nice to see NSS implement a more resilient algorithm like Argon2, but that’s wishful thinking seeing a fundamental bug that didn’t find an owner in nine years."
It is not clear whether the bug has been fixed by Mozilla. Infosecurity Magazine has contacted the company for comment. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Firefox... https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Dieses Jahr haben die Pwn2Own-Veranstalter ein Preisgeld von zwei Millionen US-Dollar ausgerufen. Trotz einiger Hack-Erfolge blieb ein Großteil der Prämie jedoch im Topf.
An zwei Tagen haben sich Hacker aus vielen Teilen der Welt über verschiedene Anwendungen, Browser, virtuelle Maschinen und Windows hergemacht und einige Erfolge erzielt. Auf dem jährlich stattfindenden Wettbewerb Pwn2Own nutzen Hacker für den guten Zweck Zero-Day-Sicherheitslücken unter Zeitdruck aus. Klappt das, streichen die Teilnehmer Prämien ein. Die Entwickler der geknackten Software haben dann 90 Tage Zeit, die Lücken zu schließen.
Dieses Jahr war der Topf mit zwei Millionen US-Dollar prall gefüllt. Der Veranstalter Trend Micro schüttete aber "nur" 267.000 US-Dollar aus. Das könnte unter anderem dran liegen, dass die chinesische Regierung Sicherheitsforschern aus dem eigenen Land seit Neuestem die Teilnahme an Hacking-Wettbewerben verbietet. In der Vergangenheit haben chinesische Sicherheitsforscher den Wettbewerb oft dominiert.
Jacke als Auszeichnung
Gewonnen hat dieses Jahr mit Abstand der Sicherheitsforscher Richard Zhu. Er hat Microsofts Edge und Mozillas Firefox erfolgreich attackiert und übernommen. Dafür hat Zhu 120.000 US-Dollar eingestrichen. Klappt ein Hack, kann der Teilnehmer das gehackte Gerät behalten. Der Hauptgewinner darf sich zudem mit der Master-of-Pwn-Jacke schmücken.
Insgesamt nutzten die diesjährigen Pwn2Own-Hacker fünf Apple-Bugs, vier Microsoft-Lücken, zwei Oracle-Schwachstellen und einen Mozilla-Bug erfolgreich aus. Mit 250.000 US-Dollar war das höchste Preisgeld für einen Ausbruch aus der Sandbox von Microsofts Virtualisierungslösung Hyper-V ausgeschrieben. Das hat dieses Jahr jedoch nicht geklappt. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pwn20wn

|
Scooped by
Gust MEES
|
Les applications Hotspot Shield, PureVPN et ZenMate exhibent des vulnérabilités
Qui laissent les adresses IP des utilisateurs filtrer
Le 14 mars 2018, par Patrick Ruiz, Chroniqueur Actualités
Des services VPN populaires exhibent des failles de sécurité qui permettent la divulgation des informations sensibles de leurs utilisateurs. L’information est de vpnMentor, un site qui a vocation à les classer ; ce dernier pointe Hotspot Shield, PureVPN et ZenMate du doigt. Le site dit s’être appuyé sur l’expertise de trois chercheurs en sécurité spécialisés en la matière. Dans le détail technique publié par ces derniers, on peut d’ores et déjà dire que les vulnérabilités sont liées à des soucis avec des scripts de configuration de proxy.
Le rapport des chercheurs crédite Hotspot Shield de trois entrées dans la base de données du projet Common Vulnerabilities and Exposures (CVE). La faille référencée CVE-2018-7880 illustre clairement le propos des chercheurs. Une analyse du script de configuration de proxy (d’une version non corrigée du plugin Chrome de Hotspot Shield) a révélé qu’il suffit qu’une URL contienne une interface logique de réseau (un hôte local) pour contourner le VPN.
Dit autrement, il suffit qu’un attaquant amène un internaute à visiter une adresse du type localhost.test.com pour que le VPN cesse de le protéger. Dans ce cas, le navigateur se connecte directement à la cible sans suivre les règles inscrites dans le fichier de configuration de proxy. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
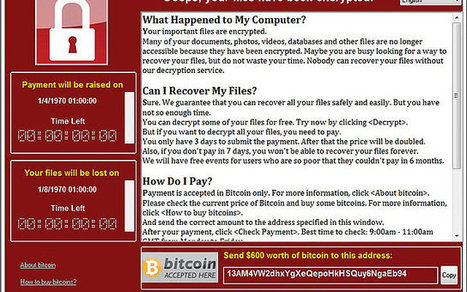
Researchers found they were able to infect robots with ransomware; in the real world such attacks could be highly damaging to businesses if robotic security isn't addressed.
Ransomware has been a headache for PC and smartphone users but in the future it could be robots that stop working unless a ransom is paid.
Researchers at security company IOActive have shown how they managed to hack the NAO robot made by Softbank and infect one with custom-built ransomware. The researchers said the same attack would work on the Pepper robot too.
After the infection, the robot is shown insulting its audience and demanding to be 'fed' bitcoin cryptocurrency in order to restore systems back to normal.
While a tiny robot making threats might initially seem amusing - if a little creepy - the proof-of-concept attack demonstrates the risks associated with a lack of security in robots and how organisations which employ robots could suddenly see parts of their business grind to a halt should they become a victim of ransomware.
"In order to get a business owner to pay a ransom to a hacker, you could make robots stop working. And because the robots are directly tied to production and services, when they stop working they'll cause a financial problem for the owner, losing money every second they're not working," Cesar Cerrudo, CTO at IOActive Labs, told ZDNet. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
A previously undisclosed flaw in Nike's website allowed anyone with a few lines of code to read server data like passwords, which could have provided greater access to the company's private systems.
An 18-year-old researcher Corben Leo discovered the flaw late last year and contacted Nike through the company's dedicated email address for reporting security flaws, which it advertises on its bug bounty page.
After hearing nothing back for more than three months, Leo contacted ZDNet, which also alerted the company to the vulnerability.
The bug exploited an out-of-band XML external entities (OOB-XXE) flaw that abused how Nike's website parses XML-based files, allowing the researcher to read files directly on the server. OOB-XXE flaws are widely seen as esoteric and difficult to carry out, but can be used to gain deep access to a server's internals. Gaining access to a server's files can disclose other avenues for exploitation, such as remote code execution or pivoting to other connected servers or databases. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES https://www.scoop.it/t/securite-pc-et-internet/?&tag=wearables https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/

|
Scooped by
Gust MEES
|
In a growing sign of the increased sophistication of both cyber attacks and defenses, GitHub has revealed that this week it weathered the largest-known DDoS attack in history.
DDoS — or distributed denial of service in full — is a cyber attack that aims to bring websites and web-based services down by bombarding them with so much traffic that their services and infrastructure are unable to handle it all. It’s a fairly common tactic used to force targets offline.
GitHub is a common target — the Chinese government was widely suspected to be behind a five-day-long attack in 2015 — and this newest assault tipped the scales at an incredible 1.35Tbps at peak.
In a blog post retelling the incident, GitHub said the attackers hijacked something called “memcaching” — a distributed memory system known for high-performance and demand — to massively amplify the traffic volumes that were being fired at GitHub. To do that, they initially spoofed GitHub’s IP address and took control of memcached instances that GitHub said are “inadvertently accessible on the public internet.”
The result was a huge influx of traffic. Wired reports that, in this instance, the memcached systems used amplified the data volumes by around 50 times. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DDos

|
Scooped by
Gust MEES
|
Hackers -- possibly Russian -- have reportedly had access to the German government's secure network for over a year.
As first revealed by German news agency DPA, the hackers were able to steal data in the intrusion, which was apparently spotted in December.
The report quoted unnamed sources as saying the chief suspect is the notorious APT28 or Fancy Bear group, which was reportedly behind the German parliament's big 2015 hacking and, months later, the Democratic National Committee (DNC) compromise in the US.
Fancy Bear is widely believed to be under the Kremlin's control. Apart from the Bundestag and DNC, its targets have included everyone from the Ukrainian military and US defense contractors, to Russian opposition parliamentarians and the Putin-critical punk group Pussy Riot.
The group's previous German hack involved the Bundestag's regular network. This time it's the secure Berlin-Bonn Information Network (IVBB), an intranet run by the Interior Ministry that comes with higher usage restrictions for users and is supposed to be firewalled to the gills. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberattacks

|
Scooped by
Gust MEES
|
New Mirai variant named Mirai OMG
Fortinet has named this variant Mirai OMG —based on the OOMGA string found in some parts of the malware's source code where the term "Mirai" used to be— and this variant now joins a growing Mirai family that also includes variants such as Satori (Okiru), Masuta, and Akuma.
But while Fortinet has not analyzed the traffic flowing through the Mirai OMG network, in theory, it should not be any different from the regular type of traffic that malicious proxy networks have been relaying for years. This includes:
⠕ relaying traffic meant for malware C&C servers to hide their true location
⠕ acting as launching points for dictionary and brute-force attacks to bypass security solutions that limit the number of failed attempts per IP
⠕ launching SQL injection, CSRF, LFI, and XSS attacks to bypass geofencing rules and exploit other web applications
Since Mirai OMG still relies on the classic Mirai spreading technique of brute-forcing devices using weak passwords, changing any IoT equipment's default password should safeguard most users from having their device taken over for a crime spree.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot https://www.scoop.it/t/securite-pc-et-internet/?&tag=Mirai+Botnet

|
Scooped by
Gust MEES
|
Geleistete Lösegeldzahlungen sind nur die Spitze des Eisbergs und nehmen sich im Vergleich zu den übrigen (Folge-)Kosten einer Infektion eher gering aus. Die eigentlichen Schadenssummen umfassen auch andere Kosten:
Datenverlust
Ausfallzeiten
Ersatz / Neuaufsetzen von Infrastruktur
Produktivität
Kosten für IT-Forensik
Reputationsschäden
Leib und Leben - gerade in Fällen, in denen Krankenhäuser und Pflegeeinrichtungen betroffen sind.
Nach einer Studie von CyberSecurity Ventures, einem der weltweit führenden Forschungsunternehmen der Internetwirtschaft, wird sich die gesamte weltweite Schadenssumme für das Jahr 2017 schätzungsweise um oder über fünf Millarden Dollar bewegen. Das bedeutet einen Anstieg um das fünffache der Schadenssumme von 2016. Experten prognostizieren hier einen weiteren Anstieg bis auf das 15-fache innerhalb der kommenden zwei Jahre: Um 2019 herum könnten es Schäden in Höhe von über 11.5 Milliarden Dollar sein.
Werfen wir einen Blick auf die prominentesten Vertreter der Gattung Ransomware und darauf, wie solche astronomischen Schadenssummen zustande kommen. Die nachfolgende Tabelle enthält Hinweise auf ein bestimmtes Verhaltensmuster, nach dem sich Malware-Autoren zunehmen auf Wirtschaftszweige kontentrieren, in denen die Absicherung wichtiger Kundendaten einen hohen Stellenwert hat.
Die Tatsache, dass Lösegelder gezahlt werden und dass hier massive Imageschäden angerichtet werden, unterstreicht, dass diese Strategie Wirkung zeigt. Petna bildet hier eine Ausnahme, da dieser Schädling nie dazu gefdacht war, Profit zu generieren. Stattdessen war Petnas Ziel, betroffene Betriebe lahmzulegen. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE
|



 Your new post is loading...
Your new post is loading...




























A dangerous Drupal flaw could leave your site completely compromised if you don't patch the flaw immediately.
Developers of popular open-source CMS Drupal are warning admins to immediately patch a flaw that an attacker can exploit just by visiting a vulnerable site.
The bug affects all sites running on Drupal 8, Drupal 7, and Drupal 6. Drupal's project usage page indicates that about a million sites are running the affected versions.
Admins are being urged to immediately update to Drupal 7.58 or Drupal 8.5.1. Drupal issued an alert for the patch last week warning admins to allocate time for patching because exploits might arrive "within hours or days" of its security release. So far, there haven't been any attacks using the flaw, according to Drupal.
The bug, which is being called Drupalgeddon2, has been assigned the official identifier CVE-2018-7600.
Drupal has given it a 'highly critical' rating with a risk score of 21 out of 25 under the NIST Common Misuse Scoring System.
Although there are no security releases for the unsupported Drupal 8.3.x and 8.4.x, Drupal has released patches for quick remediation.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Drupal