 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Découverts par l'équipe de sécurité de Google les détails techniques de la faille ont été rendus publics mais le patch pour la corriger n'est pas encore prêt.
Une nouvelle faille de sécurité a été découverte dans le navigateur Edge et Microsoft en a été informé l'année dernière. Toutefois les développeurs Microsoft ont trop tardé à mettre en place un correctif pour corriger le problème.
L'équipe de chercheurs en sécurité de Google Project Zero suit une procédure bien particulière lorsqu'une faille est découverte dans un logiciel. Il informe tout d'abord l'éditeur sans divulguer la faille publiquement pour que celui-ci ait le temps de la corriger. Après un certain délai, que le correctif soit disponible ou non, la faille est rendue publique. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Quantum bits are the basic units of information in quantum computing, a new type of computer in which particles like electrons or photons can be utilized to process information, with both “sides” (polarizations) acting as a positive or negative (i.e. the zeros and ones of traditional computer processing) alternatively or at the same time.
According to experts, quantum computers will be able to create breakthroughs in many of the most complicated data processing problems, leading to the development of new medicines, building molecular structures and doing analysis going far beyond the capabilities of today’s binary computers.
The elements of quantum computing have been around for decades, but it’s only in the past few years that a commercial computer that could be called “quantum” has been built by a company called D-Wave. Announced in January, the D-Wave 2000Q can “solve larger problems than was previously possible, with faster performance, providing a big step toward production applications in optimization, cybersecurity, machine learning and sampling.”
IBM recently announced that it had gone even further — and that it expected that by the end of 2017 it would be able to commercialize quantum computing with a 50-qubit processor prototype, as well as provide online access to 20-qubit processors. IBM’s announcement followed the September Microsoft announcement of a new quantum computing programming language and stable topological qubit technology that can be used to scale up the number of qubits.
Taking advantage of the physical “spin” of quantum elements, a quantum computer will be able to process simultaneously the same data in different ways, enabling it to make projections and analyses much more quickly and efficiently than is now possible. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=Quantum-Computing https://www.scoop.it/t/securite-pc-et-internet/?&tag=Quantum

|
Scooped by
Gust MEES
|
Over the weekend, officials from the Winter Olympics taking place in South Korea confirmed a cyberattack hit systems helping run the event during the opening ceremony. They didn't provide much detail, though the attack coincided with 12 hours of downtime on the official website, the collapse of Wi-Fi in the Pyeonchang Olympic stadium and the failure of televisions and internet in media rooms, according to reports.
Researchers from Cisco's Talos cybersecurity unit now believe with "moderate" confidence they've found the malware responsible. They've suitably named it Olympic Destroyer, for its main focus is taking down systems and wiping data, rather than stealing information. More specifically, it deletes files and their copies, as well as event logs, whilst using legitimate features on Windows computers to move around targeted networks.
For the latter, the malware tries to use PsExec and Windows Management Instrumentation, both used by network administrators to access and carry out actions on other users' PCs. Both were used by the NotPetya ransomware in 2017. Whilst no one has attributed the Olympics attacks, Ukraine blamed Russia for NotPetya and suspicions the latter would target the event via digital means have been rife. Russia, meanwhile, has told media it was not responsible.
"We know that Western media are planning pseudo-investigations on the theme of 'Russian fingerprints' in hacking attacks on information resources related to the hosting of the Winter Olympic Games in the Republic of Korea," the foreign ministry said, according to the BBC. "Of course, no evidence will be presented to the world." Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet

|
Scooped by
Gust MEES
|
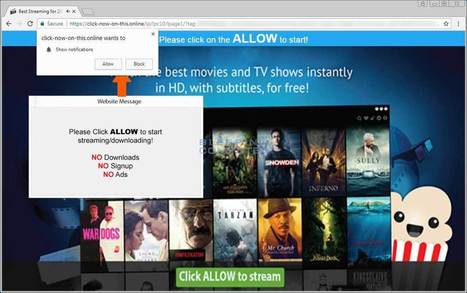
If there is one thing that is universally disliked, it is spam. Thankfully, most large email services and providers do an admirable job filtering spam before it even gets to your inbox.
Unfortunately, a new method of sending you spam has been created that skips your email altogether and sends it directly to your browser. This new method is called web notification spam and I have started to see numerous sites being setup to utilize this new tactic.
What are web notifications?
Web notifications is a legitimate method that sites can use to send subscribers notifications when new content is available.
It works like this. A visitor goes to a site and they are presented with a notification at the top of the browser that asks them to allow the web site to send or show notifications. If a user clicks on the Allow button, the site can send them notifications of new content when it is published.
For example, if BleepingComputer utilized web notifications, you would get a prompt like the one below when you visited the site. If you subscribed, it is expected that you would only receive notifications about new content at BleepingComputer.com.
Learn more / En savoir plus / Mehr erfahren. https://www.scoop.it/t/securite-pc-et-internet/?&tag=Spam

|
Scooped by
Gust MEES
|
Un problème de sécurité informatique découvert dans l’application Telegram Desktop. Des attaques ont été confirmées.
Une vulnérabilité dans Telegram utilisées dans une attaque informatique en cours. Alors que les messageries sociales font partie de l’environnement quotidien connecté d’une part importante de notre société, la confiance des utilisateurs en une plateforme dépend de la sécurité des données qui s’y trouvent et des plateformes en elles-mêmes. La confidentialité et la fréquence des messages partagés sur ces types de messageries entraine une prise de risque conséquente pour les utilisateurs, en cas de cyberattaque ou de faille de sécurité.
Après la découverte du malware mobile compromettant WhatsApp, les chercheurs de Kaspersky Lab ont cette fois-ci découvert des attaques en cours, menées par un nouveau malware exploitant une vulnérabilité Zero Day dans l’application Telegram Desktop. La faille a servi à diffuser ce malware multifonction qui, suivant le type d’ordinateur, peut agir comme une porte dérobée (backdoor) ou comme vecteur d’un logiciel de minage de cryptomonnaies (Monero, Zcash, etc.).
La faille Zero Day dans Telegram repose sur la méthode Unicode RLO (Right-to-Left Override), généralement employée pour le codage de langues qui s’écrivent de droite à gauche, telles que l’arabe ou l’hébreu. En dehors de cela, toutefois, la vulnérabilité peut également être exploitée par les auteurs du malware pour inciter par ruse les utilisateurs à télécharger des fichiers malveillants, par exemple masqués sous forme d’images. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet https://www.scoop.it/t/securite-pc-et-internet/?&tag=Telegram

|
Scooped by
Gust MEES
|
Cyberwarfare is taking to the skies, aboard dronesHovering computers will make it increasingly possible to hack equipment that doesn’t connect directly to the internet. The drones: Cyberscoop rounded up a selection of drones that hack into networks. Take your pick: flying wiretaps for mobile networks, home-brew devices that turn off smart bulbs, or giants with 20-foot wingspans that meddle with Wi-Fi networks. What the experts say: “This market is about to blow up,” Francis Brown of thecybersecurity firm Bishop Fox told Cyberscoop. “Everyone is dumping money into this.” Why it matters: It’s often assumed that devices that don’t directly connect to the internet are relatively sheltered from attack. While it’s not straightforward, hovering a drone close to a vehicle or building could enable people to hack devices that use wireless communication but were once thought relatively safe. Hack backs: It’s also worth noting that drones, with wireless connections and precarious modes of travel, are highly susceptible to being hacked out of the sky, too. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet https://www.scoop.it/t/21st-century-innovative-technologies-and-developments/?&tag=Drones

|
Scooped by
Gust MEES
|
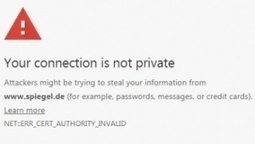
Mit Chrome 66 und 70 im April und Oktober entzieht Google gut hunderttausend der wichtigsten Domains das Vertrauen, falls diese sich keine neuen SSL-Zertifikate besorgen. Das Ganze ist eine Bestrafungsaktion gegen den Zertifikatsaussteller Symantec.
Geht alles nach Plan, macht Google am 17. April mit Chrome 66 Ernst: Ab dann werden Nutzer gewarnt, wenn der Browser auf ein Symantec-Zertifikat trifft, das vor dem 1. Juni 2016 ausgestellt wurden. Chrome beschwert sich dann, dass die Verbindung nicht sicher sei und eventuell Daten von Dritten abgefangen werden könnten. Am 23. Oktober, wenn Chrome 70 erscheinen soll, wird es noch unangenehmer für die Besitzer von Seiten mit Symantec-Zertifikaten: Ab dann stuft Googles Browser alle Verbindungen, die Symantec-Zertifikate nutzen, als nicht vertrauenswürdig ein und warnt noch lauter. Ein Sicherheitstechniker der Firma Airbnb hat sich nun die Mühe gemacht, herauszufinden, wie viele Seiten genau betroffen sind.
Spiegel, Uni Hildesheim und Tesla mit betroffenen Zertifikaten
Das Skript, das Arkadiy Tetelman gebaut hat um eine Million der (laut Alexa-Ranking) meistbesuchten Seiten im Netz nach Symantec-Zertifikaten zu durchsuchen, lief elf Stunden und fand insgesamt 11.510 Domains, die im April Fehler produzieren werden. Weitere 91.627 Domains werden mit dem Chrome-Update im Oktober Warnmeldungen auslösen. Für Admins, die nachschauen wollen, ob die eigene Seite betroffen ist, hat Tetelman eine Textdatei zur Verfügung gestellt.
Unter anderem in der Liste: Das Bundesfinanzministerium, Spiegel Online, die Uni Hildesheim, wetter.de, die Stadt Nottingham und Elon Musks Elektroautohersteller Tesla. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=HTTPS

|
Scooped by
Gust MEES
|
Adobe hat für seinen Flash Player ein Sicherheits-Update freigegeben. Version 28.0.0.161 schließt die kritische Sicherheitslücke, die vergangene Woche publik wurde. Nachdem die Lücke bereits ausgenutzt wird, sollten Sie als Flash-Nutzer dringend aktualisieren. Wie dies manuell funktioniert, erklären wir Ihnen im Video. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Flash-Player-Vulnerabilities

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Have you watched a YouTube video lately in a country where English is widely used?
If so, we’re willing to bet that you’ve seen an advert for Grammarly, an online spelling and grammar checker.
In fact, we’ll suggest you’ve seen the Grammarly ad many times, perhaps even very many times – we certainly have.
The ads seem to be working, with the product currently closing in on 1,000,000 installs in Firefox, and already claiming more than 10,000,000 in Chrome.
As the product pitch in the Firefox add-on store explains:
Once you register your new account, you will start to receive weekly emails with personalized insights and performance stats (one of our most popular new features). Working on a large project, an essay, or a blog post? No sweat. You can create and store all of your documents in your new online editor.
In other words, your Grammarly account ends up knowing a lot about you, and holding copies of a lot of what you’ve written.
A security hole in Grammarly could therefore tell crooks much more about you than you’d like them to know. Learn more / En savoir plus / Mehr erfahren. https://www.scoop.it/t/securite-pc-et-internet/?&tag=Grammarly

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Zero-Day Sicherheitslücke in Adobe Flash Player - aktiv ausgenützt - Patches noch nicht verfügbar
1. Februar 2018
Beschreibung
Adobe hat bekanntgegeben, dass es aktuell eine kritische Sicherheitslücke in Adobe Flash Player gibt, die auch bereits aktiv ausgenützt wird.
CVE-Nummer: CVE-2018-4878
Es ist noch keine entsprechend gefixte Version verfügbar - Adobe hat eine solche für nächste Woche (beginnend mit 5. Februar 2018) in Aussicht gestellt.
Auswirkungen
Durch Ausnützen dieser Lücke kann ein Angreifer laut Adobe volle Kontrolle über betroffene Systeme übernehmen.
Damit sind alle Daten auf diesen Systemen, sowie alle durch diese erreichbaren (etwa durch Login, VPN etc.) Daten und Systeme gefährdet.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Flash-Player-Vulnerabilities

|
Scooped by
Gust MEES
|
|

|
Scooped by
Gust MEES
|
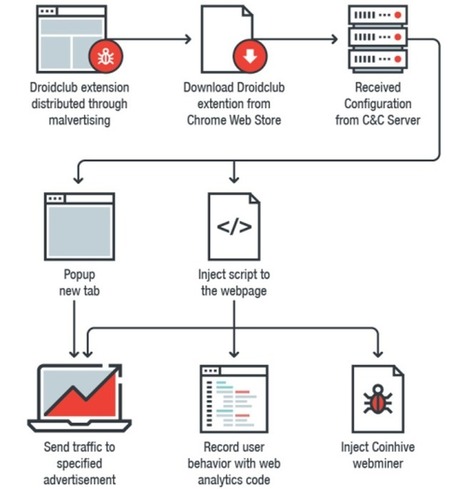
Google has removed 89 malicious extensions from the Chrome Web Store that have been installed on over 420,000 browsers, turning them into Monero-mining slaves and loading a tool to record and replay what their owners do on every website they visit.
Researchers at Trend Micro dubbed the family of malicious extensions Droidclub and discovered they included a software library with so-called "session-replay scripts" used by online analytics firms.
Princeton's Center for Information Technology in November drew attention to the increasing use of session-replay scripts by third-party analytics firms on high-traffic websites.
The study looked at replay services from Yandex, FullStory, Hotjar, UserReplay, Smartlook, Clicktale, and SessionCam, which were found on nearly 500 popular sites.
The scripts allow a site owner to essentially shoulder-surf their visitors by recording and replaying your "keystrokes, mouse movements, and scrolling behavior, along with the entire contents of the pages you visit".
But instead of allowing a site owner to record and play back what users do on one site, Droidclub extensions allow the attacker to see what victims do on every single site they visit. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Cyberespionage https://www.scoop.it/t/securite-pc-et-internet/?&tag=Privacy https://gustmees.wordpress.com/2013/12/21/privacy-in-the-digital-world-shouldnt-we-talk-about-it/ https://www.scoop.it/t/securite-pc-et-internet/?&tag=Session-Replay+Scripts

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
A cryptojacking attack hit thousands of websites, including government ones.
Surreptitious mining of cryptocurrency by hackers is spreading very, very fast.
The news: Over 4,000 websites, including those of the US federal judiciary and the UK National Health Service, have been weaponized by hackers to mine the cryptocurrency Monero on their behalf.
How it worked: Hackers injected malware into a widely used plug-in called Browsealoud that reads web pages our loud as a way of helping partially sighted people navigate the internet. The malware is based on the popular app Coinhive, a piece of software that uses processing power on someone’s device to mine cryptocurrency. The malicious version of the app does this without people's knowledge, coopting their computing power to enrich hackers.
Why it matters: Cryptojacking is rapidly becoming one of the world’s biggest cyberthreats. This news shows how easy it is for crooks to spread the trick, by infecting a single product used across multiples sites with a single hack.
Learn more / En savoir plus / mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Coinhive https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
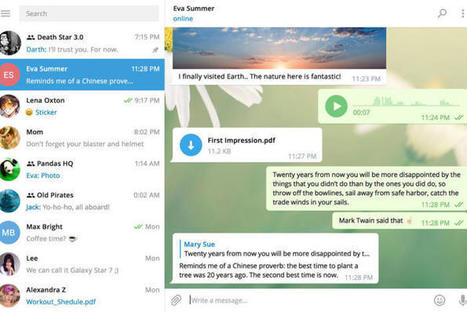
Cyber thugs have been exploiting a zero-day flaw in the Telegram Messenger desktop app in order to mine for cryptocurrencies or to install a backdoor to remotely control victims’ computers.
Kaspersky Lab discovered “in the wild” attacks on Telegram Messenger’s Windows desktop client back in October 2017. The vulnerability in the popular Telegram app had been actively exploited since March 2017 to mine a variety of cryptocurrencies, such as Monero, Zcash, Fantomcoin and others. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Telegram

|
Scooped by
Gust MEES
|
In 2018, European countries and the EU Agency for Network and Information Security (ENISA) will organise the 5th pan European cyber crisis exercise, Cyber Europe 2018 (CE2018). CE2018 is part of the bi-annual Cyber Europe series of exercises launched in 2010. The last exercise in the series, Cyber Europe 2016, involved over 1000 participants from across Europe. The scenario - Cyber Europe 2018 planners developed a scenario revolving around Aviation which can include, Civil Aviation Authorities, Air Navigation Service Providers (ANSPs), Airport Companies, Air Carriers, with potential impacts in other sector.
- The scenario will contain real life inspired technical incidents to analyse, from forensic and malware analysis, open source intelligence, and of course non-technical incidents.
- The incidents will build up into a crisis at all levels: local, organization, national, European. Business continuity plans and Crisis management procedures will be put at test
The exercise is organised for IT security, business continuity and crisis management teams coming from EU and EFTA Member States only. Learn more / En savoir plus / Mehr erfahren:

|
Scooped by
Gust MEES
|
Die Internet-Organisation ICANN scheint auch knapp vier Monate vor Inkrafttreten der EU-DSGVO keinen praktikablen Plan zu haben, wie ihre Whois-Datenbank sich mit den neuen Vorschriften vertragen könnte.
Die Datenschutzgrundverordnug der Europäischen Union sorgt nicht nur in Europa, sondern weltweit für verstärkte Aufmerksamkeit für Datenschutzfragen. Die im englischen Sprachraum als "European Union's General Data Protection Regulation" (GDPR) bezeichneten Vorschriften betreffen unter anderem auch das Whois-Sytem, den weltweiten Verzeichnisdienst für Domain-Namen.
Diese Daten sind in der Whois-Datenbank gespeichert und öffentlich abrufbar. Und da nicht nur simple Zuordnungen von Nameserver-Adressen und Domain-Namen in der Datenbank enthalten sind, sondern auch personenbezogene Daten wie die Namen von für den Domain-Betrieb Verantwortlichen (AdminC, TechC oder BillingC), entspricht das Whois-System nicht den Ende Mai 2018 inkrafttretenden EU-Vorschriften. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=GDPR

|
Scooped by
Gust MEES
|
La mise à jour Flash Player est au rendez-vous prévu afin de corriger une vulnérabilité exploitée dans des attaques. Un exploit qui pourrait être nord-coréen. Adobe en profite pour corriger une autre faille critique.
Comme promis la semaine dernière, Adobe publie une mise à jour de sécurité pour Flash Player afin de corriger la vulnérabilité CVE-2018-4878 qui est exploitée dans des attaques ciblées visant des utilisateurs Windows.
L'exploitation s'appuie sur des documents Office avec du contenu Flash malveillant. Un objet ActiveX (un fichier SWF) est intégré dans le document et contient l'exploit Flash. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Flash-Player-Vulnerabilities

|
Scooped by
Gust MEES
|
Swiss telecoms giant Swisscom has admitted that it suffered a serious security breach in the autumn of 2017 that saw the theft of contact details of approximately 800,000 customers – most of whom were mobile subscribers.
Data exposed during the breach included:
Customers’ first and last names
Customers’ home addresses
Customers’ dates of birth
Customers’ telephone numbers
Interestingly, in a press release, Swisscom pointed a finger of blame at an unnamed third-party sales partner who had been granted “limited access” to the data in order that they could identify and advise customers approaching contract renewal.
That sales partner, Swisscom says, suffered its own security breach – somehow allowing its access keys to Swisscom to fall into criminal hands.
A routine check of Swisscom’s operational activities uncovered the unauthorised data access, and the offending partner’s access rights revoked.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
A flaw in Hotspot Shield can expose VPN users, locations
The virtual private network says it provides a way to browse the web "anonymously and privately," but a security researcher has released code that could identify users' names and locations.
A security researcher has found a way to identify users of Hotspot Shield, a popular free virtual private network service that promises its users anonymity and privacy.
Hotspot Shield, developed by AnchorFree, has an estimated 500 million users around the world relying on its privacy service. By bouncing a user's internet and browsing traffic through its own encrypted pipes, the service makes it harder for others to identify individual users and eavesdrop on their browsing habits.
But an information disclosure bug in the privacy service results in a leak of user data, such as which country the user is located, and the user's Wi-Fi network name, if connected.
That information leak can be used to narrow down users and their location by correlating Wi-Fi network name with public and readily available data.
"By disclosing information such as Wi-Fi name, an attacker can easily narrow down or pinpoint where the victim is located," said Paulos Yibelo, who found the bug. Combined with knowing the user's country, "you can narrow down a list of places where your victim is located," he said.
ZDNet was able to independently verify Yibelo's findings by using his proof-of-concept code to reveal a user's Wi-Fi network. We tested on several machines and different networks, all with the same result.
VPNs are popular for activists or dissidents in parts of the world where internet access is restricted because of censorship, or heavily monitored by the state, as these services mask a user's IP addresses that can be used to pinpoint a person's real-world location.
Being able to identify a Hotspot Shield user in an authoritarian state could put them at risk!!! Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=VPN

|
Scooped by
Gust MEES
|
Grammarly has fixed a security bug in its Chrome extension that inadvertently allowed access to a user's account -- including their private documents and data.
Tavis Ormandy, a security researcher at Google's Project Zero who found the "high severity" vulnerability, said the browser extension exposed authentication tokens to all websites.
That means any website can access a user's documents, history, logs, and other data, the bug report said.
"I'm calling this a high severity bug, because it seems like a pretty severe violation of user expectations," said Ormandy, because "users would not expect that visiting a website gives it permission to access documents or data they've typed into other websites."
In proof-of-concept code, he explained how to trigger the bug in four lines of code.
More than 22 million users have installed the grammar-checking extension.
Ormandy filed his bug report Friday, subject to a 90-day disclosure deadline -- as is the industry standard. Grammarly issued an automatic update Monday to fix the issue.
Ormandy has in recent months examined several vulnerable web browser extensions. Earlier this year, he found a remote code execution flaw in the Cisco WebEx Chrome extension, and a data-stealing bug in the popular LastPass password manager.
A spokesperson for Grammarly did not immediately return a request for comment.
Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=DATA-BREACHES

|
Scooped by
Gust MEES
|
Sicherheitsexperten von Proofpoint untersuchten das Mining-Botnet Smominru, das auf mehr als 500.000 Windows-Maschinen die Kryptowährung Minero schürft.
Nach Erkenntnissen von Sicherheitsexperten der Firma Proofpoint missbrauchen Kriminelle die Rechenleistung von mehr als einer halben Million Windows-Systemen, um die Kryptowährung Minero zu "schürfen". Laut Proofpoint handelt es sich bei den befallenen Maschinen vor allem um Windows-Server, von denen viele in Russland, Indien, Taiwan und der Ukraine laufen. Im Beobachtungszeitraum von Mai 2017 bis Januar 2018 hätten die Angreifer Mineros im Wert von rund 3,6 Millionen US-Dollar ergattert.
Server unbrauchbar
Auf den Stromkosten bleiben die Geschädigten sitzen, außerdem vermuten die Sicherheitsforscher, dass viele der befallenen Server wegen der zusätzlichen Rechenlast nur noch eingeschränkt funktionieren. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=crypto-currency https://www.scoop.it/t/securite-pc-et-internet/?&tag=cryptojacking

|
Scooped by
Gust MEES
|
|



 Your new post is loading...
Your new post is loading...

























Découverts par l'équipe de sécurité de Google les détails techniques de la faille ont été rendus publics mais le patch pour la corriger n'est pas encore prêt.
Une nouvelle faille de sécurité a été découverte dans le navigateur Edge et Microsoft en a été informé l'année dernière. Toutefois les développeurs Microsoft ont trop tardé à mettre en place un correctif pour corriger le problème.
L'équipe de chercheurs en sécurité de Google Project Zero suit une procédure bien particulière lorsqu'une faille est découverte dans un logiciel. Il informe tout d'abord l'éditeur sans divulguer la faille publiquement pour que celui-ci ait le temps de la corriger. Après un certain délai, que le correctif soit disponible ou non, la faille est rendue publique.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers